Malware obfuscation techniques: four simple examples
Malware using obfuscation to avoid detection, and the possibilities are quite endless
Obfuscation is a technique that makes binary and textual data unreadable and/or hard to understand.
Software developers sometimes employ obfuscation techniques because they don’t want their programs being reverse-engineered or pirated.
But the obfuscation is widely used also by malware writers in order to evade antivirus scanners, so it becomes important to analyze how this technique is applied to malwares.
Exclusive OR (XOR)
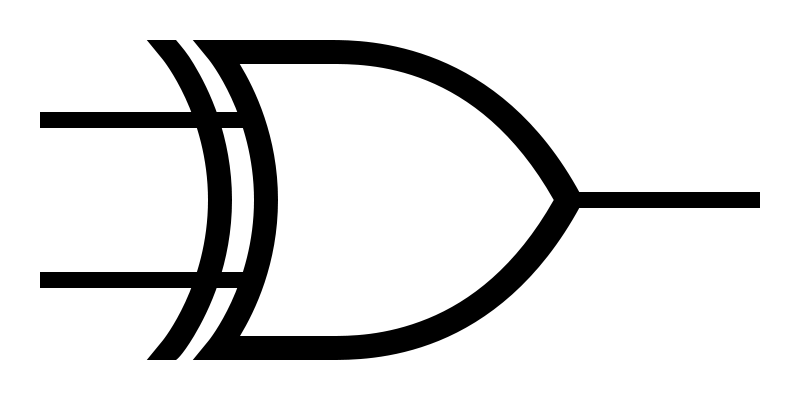
The XOR operation is probably the most commonly used method of obfuscation. This is because it is very easy to implement and easily hides your data from untrained eyes.
A tool like Didier Steven’s XORSeach can scan any file, looking for strings encoded using XOR method: you need to know the clear-text version of the string you’d like XORSearch to locate.
One good value to look for is “http”, because attackers often wish to conceal URLs within malicious code.
Another good string might be “This program”, because that might identify an embedded and XOR-encoded Windows executable, which typically has the string “This program cannot be run in DOS mode” in the DOS portion of the PE header.
Base64 encoding
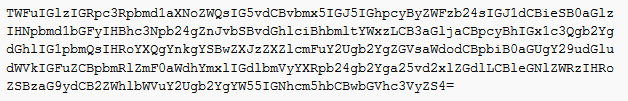
Base64 is commonly used in malware to disguise text strings.
The encoded output is completely unreadable but Base64 encoding is easier to identify than a lot of encoding schemes, usually because of its padding character.
There are a lot of tools that can perform Base64 encode/decode functions, both online and via downloaded programs.
ROT13
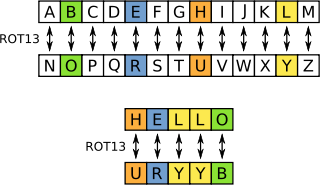
ROT13 is probability the most simple obfuscation technique.
ROT is an ASM instruction for “rotate”, so ROT13 would mean “rotate 13”: using a simple letter substitution obtains an obfuscated output.
For example: let’s start by encoding the letter ‘a’. Since we’re rotating by 13, we count the next thirteen letters of the alphabet until we land at ‘n’.
Code Packing

A technique to hide the real code of a program through one or more layers of compression/encryption: at run-time the unpacking routine restores the original code in memory and then executes it