How to extract data and timeline from Master File Table on NTFS filesystem
The most important file in a NTFS filesystem
During a forensics analysis, after evidence acquisition, the investigation starts by doing a timeline analysis, that extract from the images all information on when files were modified, accessed, changed and created.
Different techniques and tools exist to create timelines: today i want to focus on the information that can be extracted from the Master File Table (MFT).
The Master File Table (MFT)
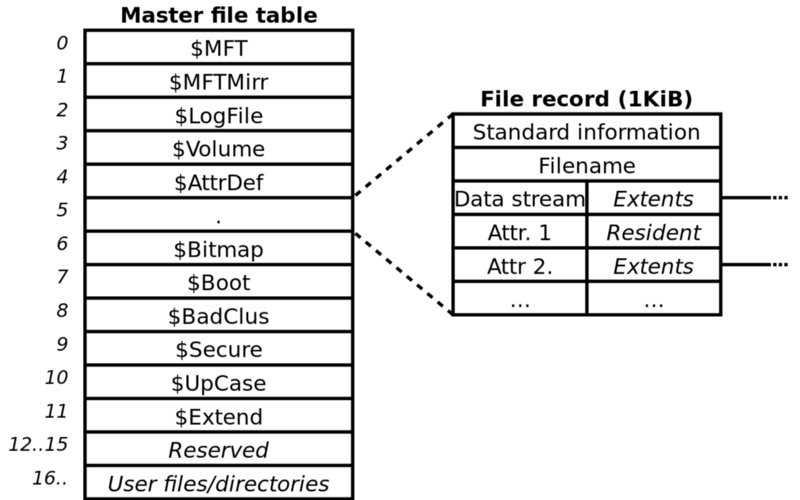
MFT is a special system file that resides on the root of every NTFS partition, named $MFT and not accessible via user mode API’s.
However it can been seen when you have raw access to the disk (e.g, forensic image or specific tools).
This special file is the heart of NTFS and contains entries for every file and directory on disk.
Each entry of the $MFT contains a series of attributes about the filesystem object and indicates where it resides on the physical disk and if is active or inactive.
How to extract data from MFT?
On Windows systems
You can use Mft2Csv: is a powerful tool developed by Joakim Schicht with the ability to read $MFT from a variety of sources, including live system acquisition.
The output by default is saved in a CSV format but could be also exported as log2timeline or bodyfile:
This tool is for parsing, decoding and logging information from the Master File Table ($MFT) to a csv. It is logging a large amount of data and that has been the main purpose from the very start. Having all this data in a csv is convenient for further analysis. It supports getting the $MFT from a variety of sources.
Details
Input can be any of the following:
- Raw/dd image of disk (MBR and GPT supported)
- Raw/dd image of partition
- $MFT extracted file
- Reading of $MFT directly from a live system
- Reading of $MFT by accessing .PhysicalDriveN directly (no mount point needed).
- Reading of $MFT directly from within shadow copies.
- $MFT fragments extracted from memory dumps or unallocated (see MFTCarver).
- Single records extracted. See MftRcrd with the -w switch.
The format of output can be chosen. Currently it is possible to choose from:
- All (will write to csv everything it can). Default set.
- log2timeline: http://code.google.com/p/log2timeline/wiki/l2t_csv
- bodyfile (v3.x): http://wiki.sleuthkit.org/index.php?title=Body_file
On Linux systems
A similar tool on linux environment is analyzeMFT:
analyzeMFT.py is designed to fully parse the MFT file from an NTFS filesystem
and present the results as accurately as possible in multiple formats.
analyzeMFT can produce output in CSV or bodyfile format.
Installation
You can install analyzeMFT with pip:
pip install analyzeMFT
Usage
Usage: analyzeMFT.py [options]
Options:
-h, --help show this help message and exit
-v, --version report version and exit
File input options:
-f FILE, --file=FILE read MFT from FILE
File output options:
-o FILE, --output=FILE
write results to FILE
-c FILE, --csvtimefile=FILE
write CSV format timeline file
-b FILE, --bodyfile=FILE
write MAC information to bodyfile
Options specific to body files:
--bodystd Use STD_INFO timestamps for body file rather than FN
timestamps
--bodyfull Use full path name + filename rather than just
filename
Other options:
-a, --anomaly turn on anomaly detection
-l, --localtz report times using local timezone
-e, --excel print date/time in Excel friendly format
-d, --debug turn on debugging output
-s, --saveinmemory Save a copy of the decoded MFT in memory. Do not use
for very large MFTs
-p, --progress Show systematic progress reports.
-w, --windows-path Use windows path separator when constructing the filepath instead of linux
You can extract and analyze the MFT in 3 simple steps, starting from an EWS ( Expert Witness) image.
- Find the correct offset using mmls (from sleuthkit):
# mmls image.E01
DOS Partition Table
Offset Sector: 0
Units are in 512-byte sectors
Slot Start End Length Description
000: Meta 0000000000 0000000000 0000000001 Primary Table (#0)
001: ------- 0000000000 0000000062 0000000063 Unallocated
002: 000:000 0000000063 0035551844 0035551782 NTFS / exFAT (0x07)
003: ------- 0035551845 0035567909 0000016065 Unallocated- Extract MFT using icat:
icat -o 63 image.E01 0 > mft.raw- Parse the MFT with analyzeMFT:
analyzeMFT.py -f mft.raw -o mftanalyzed.csv