MAC(b) times in Windows forensic analysis
Essential information during timeline analysis
During a forensic analysis, especially during timeline analysis, you deal with MAC timestamps, so it’s important to know and understand the concept of time resolution.
The MAC(b) times are derived from file system metadata and they stand for:
- Modified
- Accessed
- Changed ($MFT Modified)
- Birth (file creation time)
The (b) is in parentheses because not all file systems record a birth time.
Where are they stored?
Into two attributes, $STANDARD_INFO and $FILE_NAME:
$STANDARD_INFO
$STANDARD_INFO ($SI) stores file metadata such as flags, the file SID, the file owner and a set of MAC(b) timestamps.
$STANDARD_INFO is the timestamp collected by Windows explorer, fls, mactime, timestomp, find and the other utilities related to the display of timestamps.
$FILE_NAME
The $File_Name attribute contains forensically interesting bits, such as MACB times, file name, file length and more.
Timestamps are only updated with the attribute is changed.
Files can have either one or two $File_Name attributes depending on how long the file name is:
- Short file names (“file.txt”) has only one $File_Name attribute.
- Long file names (“extremelylongfilename.txt”) will have two $File_Name attributes.
- One for the long file name, and one for the DOS-compatible short name (EXTRE~1.TXT).
What are the differences?
- $STANDARD_INFO can be modified by user level processes like timestomp.
- $FILE_NAME can only be modified by the system kernel. (There are no known anti-forensics utilities that can accomplish this.)
Time Rules
There are general rules when it comes to files being moved, copied, accessed or created.
Each operation alters different metadata, here a table of time rules related to $STANDARD_INFORMATION:
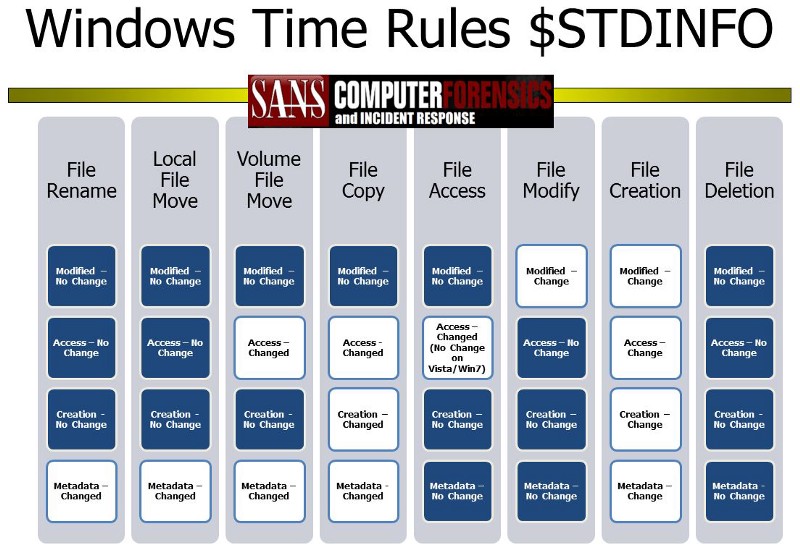
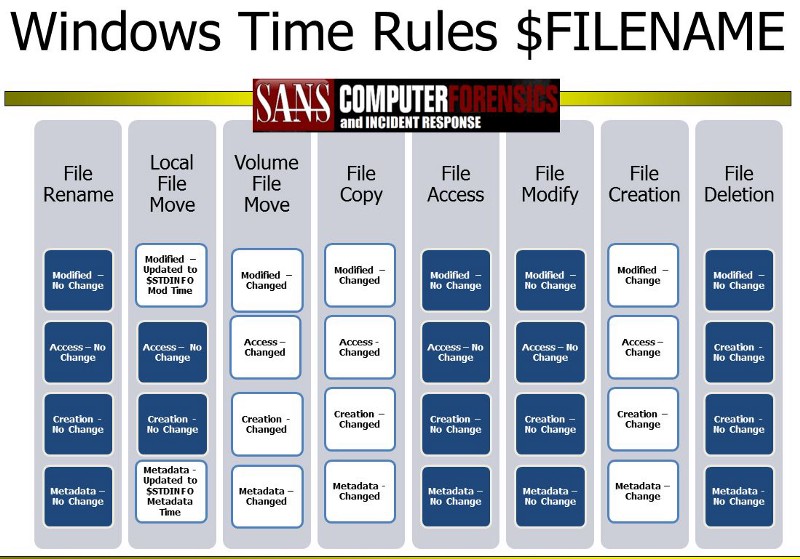
While examining the $FILE_NAME timestamps the rules are pretty different:
How to detect Anti-Forensics Timestamp Anomalies?
Tool such as timestomp allow attackers to backdate a file to an arbitrary time in order to trying to hide it in system32 or other similar directories.
So, during analysis you can use analyzeMFT.py in order to check if the $FILE_NAME time occurs after the $STANDARD_INFORMATION Creation Time.
If this anomaly occurs, it is likely that an attacker has been alterated timestamps in $STANDARD_INFO using timestomp.