RunPE: a practical example of Process Hollowing technique
About the "Process Hollowing" i have already written some posts (like this).
However, i've never published any practical example.
So, today i want to quote this interesting article where Tigzy explains the process hollowing with a brief code snippet. in wich the process hollowing is explained with a brief code snippet.
A brief recap: what is Process Hollowing?
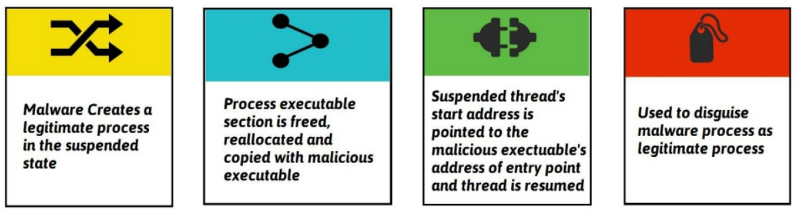
Process hollowing is a technique used by malware in which a legitimate process is loaded on the system solely to act as a container for hostile code: the legitimate process is launched in a suspended state and its memory area is replaced with the code of a second program that will be executed instead of the original .
This trick is known under the name “RunPE” and has been used many time in malware industry, especially in RATs (Remote Administration Tools).
Basically, when a malware starts, it will pick a victim among the Windows processes (like explorer.exe) and start a new instance of it, in a suspended state. In that state it’s safe to modify and the malware will totally clear it from its code, extend the memory if needed, and copy its own code inside.
Then, the malware will do some magic to adjust the address of entry point as well as the base address and will resume the process.
After being resumed, the process shows being started from a file (explorer.exe) that has nothing to do anymore with what it actually does.
Here the code snippet:
[embed]https://gist.github.com/andreafortuna/d7fb92fb29e4ade27c0c6ce4401c99fa[/embed]
The main program will call RunPe function with explorer.exe as a target, and calc.exe as a source. This will result in running calc.exe code into an explorer.exe “skin”.
The RunPe function will simply create explorer.exe in a suspended state, remove the sections belonging to that module with NtUnmapViewOfSection. Then it will allocate more memory at the same preferred address as the former unmapped sections to host the target (calc.exe) code.
That code (header + sections) is copied into the newly allocated section, and we adjust the image base + entry point address to match the new offset (explorer.exe base may be different). To finish, the main thread is resumed.
And here a video example of this technique:
[embed]https://www.youtube.com/watch?v=k2pLF56gXXw&t=45s[/embed]
For more information and the technical explanation, please refers to original article:
[embed]https://www.adlice.com/runpe-hide-code-behind-legit-process/[/embed]
About the author
Founder and owner of Adlice Software, Tigzy started as lead developer on the popular Anti-malware called RogueKiller. Involved in all the Adlice projects as lead developer, Tigzy is also doing research and reverse engineering as well as writing blog posts.