Stock-market fraud, steganography and cyberattacks...in 1834! The fascinating tale of Blanc brothers
When the first hacking of a telecommunication system occurred?
In 1834, according to this article by Tom Standage!
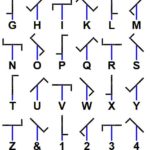
At that time there was no Internet or computers, but since 1794 France had its own national telecommunications network: a semaphore telegraph, composed of chains of towers of signaling, placed at distances of 8 to 10 kilometers from each other and equipped with two rotating arms.

These arms could be oriented in various ways to compose a code of symbols, which were transmitted from one tower to another with a very simple system: the operator in the receiver tower looked through the telescope the symbols shown by the transmitting tower and then repeats them by moving the arms of his tower.
So the symbols will be seen by the next tower operator who repeat them, and so on until the message arrived at its destination.
The system was developed by Claude Chappe and his brothers in 1792, who succeeded in covering France with a network of 556 stations stretching a total distance of 4,800 kilometres.
By Jeunamateur - Own work d'après "La télégraphie Chappe", FNHAR, 1993, CC BY-SA 3.0, https://commons.wikimedia.org/w/index.php?curid=19700042
Le système Chappe was used for military and national communications until the 1850s, allowing messages to travel about 500 kilometers per hour.
Providing that the visibility was good, a skilled operator could send three symbols in a minute.
A single symbol sent from Paris would arrive at Lille, a distance of about 200 km, in just nine minutes.
End-to-end encryption over telegraph
The network was reserved for government use, and to protect the confidentiality of messages a kind of encryption was used, so the telegraphists did not know the content of the messages they were repeating.
Only those who sent a message and those who received it can decode: a sort of end-to-end encryption.
Human factor and steganography
In 1834 François and Joseph Blanc, two bankers working on the Bordeaux stock exchange, hired a colleague in Paris for keeping a watch on Paris stock exchange and pass information on the most significant trends to a telegraph operator in Tours, on the line that transmitted data to Bordeaux.
Since the telegraph network was for governmental use only, the Blanc brothers found a way to nest their messages inside those authorized using the symbols used to indicate transmission errors.
The telegraph’s encoding system included a “backspace” symbol that instructed the transcriber to ignore the previous character.
The brothers corrupt the telegraph operator in Tours, giving him instructions to make very specific errors in the transmissions, letting them propagate along the line, and then correcting them thereafter.
The spurious character indicating the direction of the previous day’s market movement: but it was followed by a backspace, meant the text of the message being sent was unaffected when it was written out for delivery at the end of the line.
A accomplice who lived near the last station along the line, near Bordeaux, reported the errors to the Blanc brothers that are able to decode them: a sort of steganography!
This system allowed the bankers to know the trends of the Paris stock exchanges five days in advance of the local competitors (the mail from Paris took five days to arrive in Bordeaux), so the brothers earned playing in advance.
They have managed avoid getting caught for two years, but when they were unmasked (in 1836), the authorities realized that there were no laws that specifically prohibiting the injection of private messages into the optical telegraph network and therefore the two remained free.
Some highlights from Tom Standage's article
- Most attackers, like the Blancs, do not advertise their presence.
- Security is like a chain and humans are always the weakest link.
- With any new invention, people will always find a way to make malicious use of it.