Docker images under cryptojacking attack: how to check if a downloaded image is safe
Researchers at Kromtech Security Center discovers seventeen malicious Docker containers with embedded cryptominer applications that permitted to cybercriminals to earn $90,000 in 30 days.
According to the Kromtech's report, containers are shaping up to be the next target for these types of criminals.
[caption id="attachment_3391" align="alignnone" width="1024"]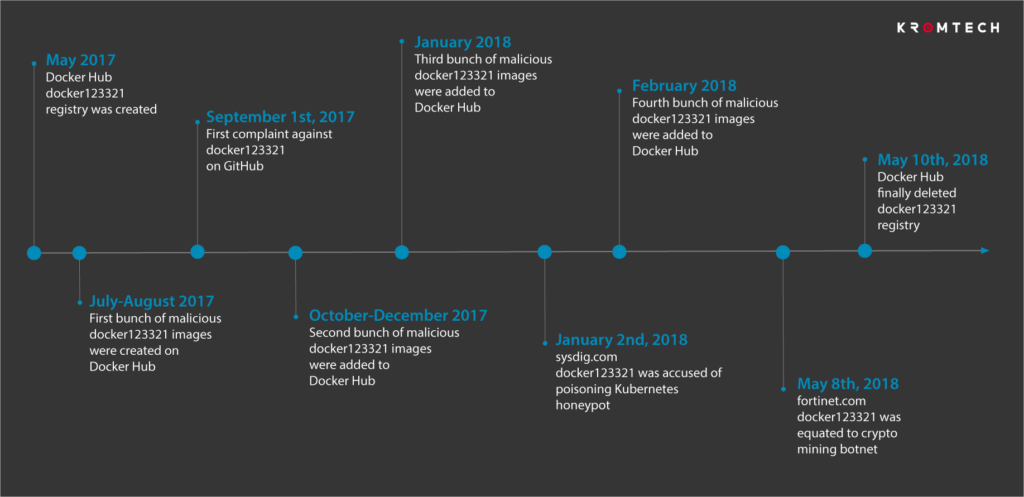 source: https://kromtech.com/blog/security-center/cryptojacking-invades-cloud-how-modern-containerization-trend-is-exploited-by-attackers[/caption]
source: https://kromtech.com/blog/security-center/cryptojacking-invades-cloud-how-modern-containerization-trend-is-exploited-by-attackers[/caption]
Researchers can’t say for sure how many times the rogue containers were used by Docker Hub users, but estimates that the 17 images were downloaded collectively 5 million times during the year they were available.
What is a Docker image?
Docker images are "snapshots" of applications and daemons, which can be easily launched when needed (into a 'container'), and are often used by developers to 'build' a software solution using this blocks out-of-the-box.
Docker also provides a public repository with a collection of images that can be downloaded freely.
In this case, cyber criminals have inserted crypto-currency generation software into published Docker images.
This images were uploaded by the same user, registered with the name of docker123321, which would have acted undisturbed for at least a year (from May 2017 to May 2018) despite there were reports of suspicious behavior.
Inside the images the criminals have added additional code that launches a series of commands and opens a shell through which allows attackers to interact with the system.
Despite the fact that only Crypto-Jacking software was detected, the researchers point out that the backdoors distributed by docker123321 would have allowed to carry out any type of action, including the execution of a ransomware.
How can i verify if a downloaded docker image is safe?
A lot of tool are developed in order to check security of docker images, below my personal shortlist.
CoreOS Clair

Clair is an open source project for the static analysis of vulnerabilities in containers, that periodically refreshes its vulnerability database from a set of configured CVE sources, scrubs the available container images and indexes the installed software packages.
If any insecure software is detected, it can alert or block deployment to production.
Since Clair image analysis is static, containers never need to be actually executed, so you can detect a security threat before is already running in your systems.
Docker Bench for Security

The Docker Bench for Security is a script that checks for dozens of common best-practices around deploying Docker containers in production, conveniently packaged as a Docker container.
Dockscan

A simple ruby script that analyzes the Docker installation and running containers, easy to install and run: with just one command and can generate HTML report files reporting configured resource limits, containers spawning too many processes or with a high number of modified files, and also if your Docker host is allowing containers to directly forward traffic to the host gateway (and much more).
Actuary
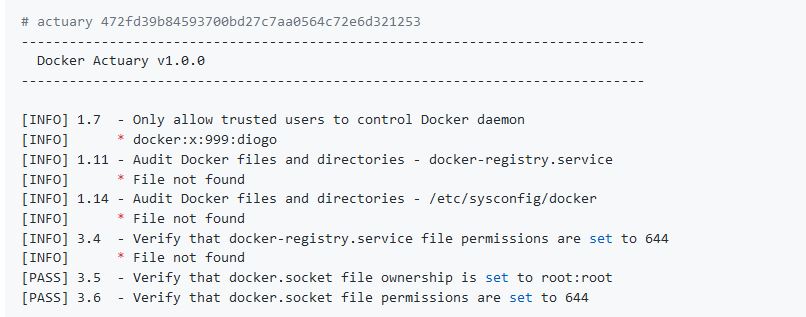
Actuary is an application that checks for dozens of common best-practices around deploying Docker containers in production, that takes in a checklist of items to check, and automates the running, inspecting and aggregation of the results.
Anchore
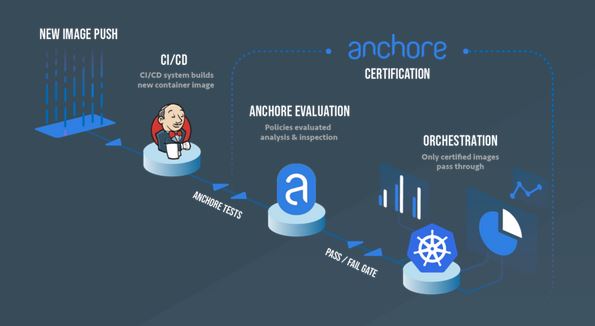
Anchore is an automated scanning tool to check for CVEs - and also custom checks on container or application configuration rules - in Docker images.
Anchore is available as a free SaaS online Navigator for public registries, and an open source engine for on-prem scanning.