Malhunt: automated malware search in memory dumps
Recently i've published this post focused on hunting malware using volatility and Yara rules.
Into the article i've shared the simple script which i use for downloading and merging all yara rules related to malware into a single file, useful for scan with yarascan volatility's plugin.
So, starting from this script, i've developed a more complex solution that currently I use for first phases of analysis: the script, dubbed "Malhunt", automatize my workflow for malware hunting
The workflow
My personal workflow is composed by 2 main steps:
Identify suspicios processes
First, a list of suspicious preocesses is needed for further analysis.
Usually i use the mixed result of 3 volatility plugin:
- yarascan: search suspicious processes trying to identify malware artifacts using a list of yara rules. This step is already explained in this article.
- malfind: scans process memory in order to find some condition that may suggest some code injection (usually a memory area marked as Page_Execute_ReadWrite, which allows a piece of code to run and write itself).
- network scan: using correct plugin according to Windows version (netscan or connscan), i extract a list of foreign address and PIDs. If an ip is present into a blacklist (currently http://getipintel.net/), the related PID is added into the "suspiscios list".
Check processes for malware
In this second step, I dump all suspicious processes and related handles and check them with clamscan, in order to confirm the detection performed in the first step or mark it as false-positive.
If this workflow return even a single result, you have a good pivot point for further investigations.
Malhunt
Obviously, the name is a pun based on "manhunt" word.
The script, developed in python with a very short list of dependencies, applies all steps of the just mentioned workflow and present the results a simple report.
Further, automatize the image identification process, caches some result and automatically downloads and merges yara rules.
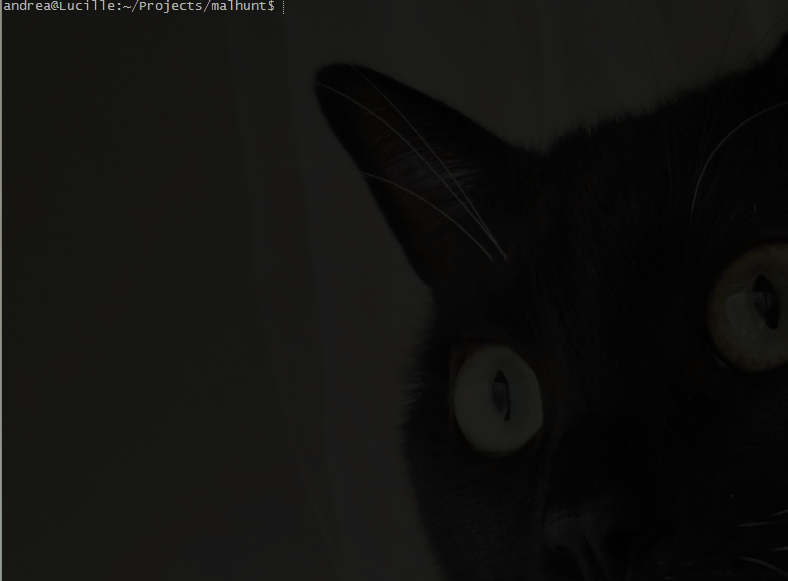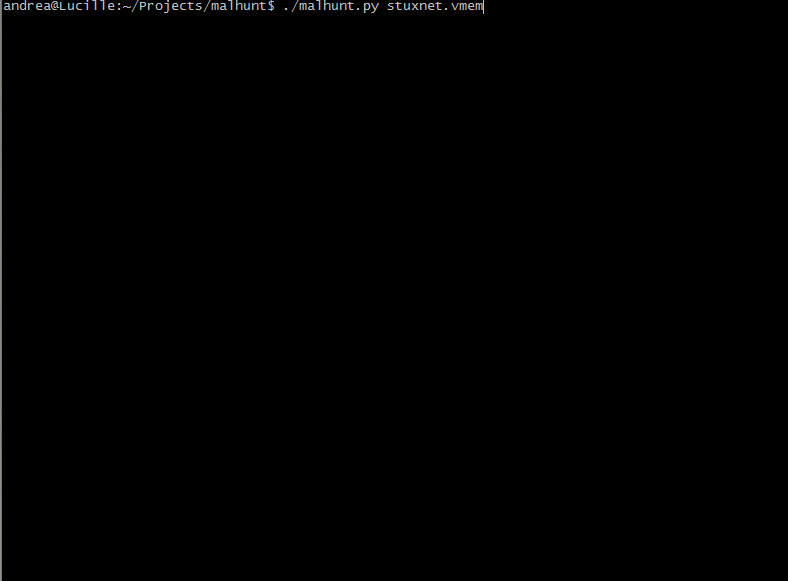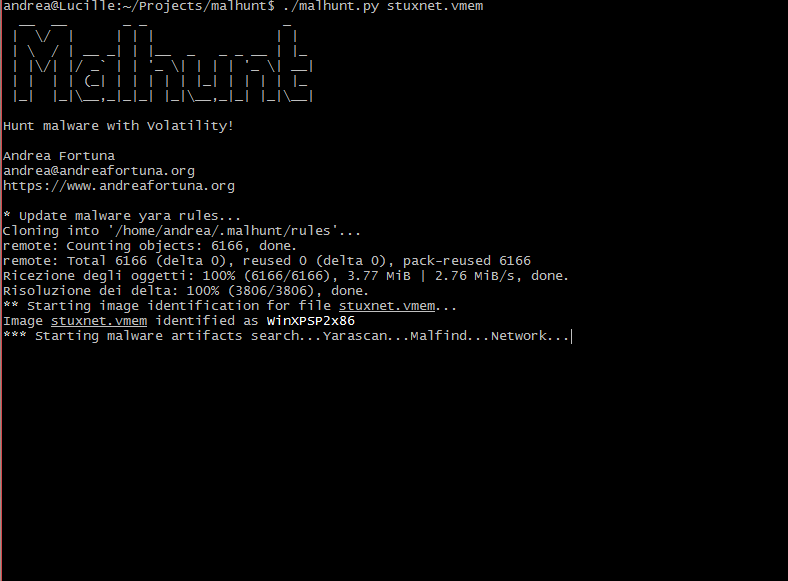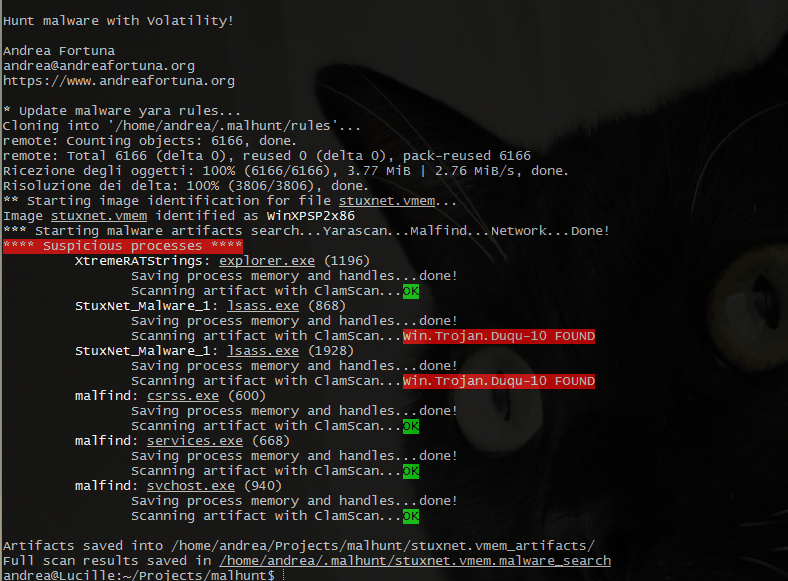
Here a simple gif that shows the Malhunt output, during the analysys of a memory dump extracted from a stuxnet infected machine:
Requirements
- Python
- Git
- Volatility
- Clamscan from ClamAV
Installation
Simply clone the repository:
git clone git@github.com:andreafortuna/malhunt.git
Usage
Start malhunt.py specifing the memory image file:
./malhunt.py stuxnet.vmem
__ __ _ _ _
| \/ | | | | | |
| \ / | __ _| | |__ _ _ _ __ | |_
| |\/| |/ _` | | '_ \| | | | '_ \| __|
| | | | (_| | | | | | |_| | | | | |_
|_| |_|\__,_|_|_| |_|\__,_|_| |_|\__|
Hunt malware with Volatility!
Andrea Fortuna
andrea@andreafortuna.org
https://www.andreafortuna.org
* Update malware yara rules...
Cloning into '/home/andrea/.malhunt/rules'...
remote: Counting objects: 6166, done.
remote: Total 6166 (delta 0), reused 0 (delta 0), pack-reused 6166
Ricezione degli oggetti: 100% (6166/6166), 3.77 MiB | 2.08 MiB/s, done.
Risoluzione dei delta: 100% (3806/3806), done.
** Starting image identification for file stuxnet.vmem...
Image stuxnet.vmem identified as WinXPSP2x86
*** Starting malware artifacts search...Yarascan...Malfind...Network...Done!
**** Suspicious processes ****
XtremeRATStrings: explorer.exe (1196)
Saving process memory and handles...done!
Scanning artifact with ClamScan...OK
StuxNet_Malware_1: lsass.exe (868)
Saving process memory and handles...done!
Scanning artifact with ClamScan...Win.Trojan.Duqu-10 FOUND
StuxNet_Malware_1: lsass.exe (1928)
Saving process memory and handles...done!
Scanning artifact with ClamScan...Win.Trojan.Duqu-10 FOUND
malfind: csrss.exe (600)
Saving process memory and handles...done!
Scanning artifact with ClamScan...OK
malfind: services.exe (668)
Saving process memory and handles...done!
Scanning artifact with ClamScan...OK
malfind: svchost.exe (940)
Saving process memory and handles...done!
Scanning artifact with ClamScan...OK
That's all: I hope can be useful!