AutoTimeliner: automatically extract forensic timeline from memory dumps
Often, during an incident response, may be necessary to analyze a lot of evidences, like disk and memory dumps.
In my workflow, one of the first step is the creation of a timeline extracted from the volatile memory dump.
For this process, i've developed a simple python script that automatically performs the timeline creation on multiple memory images.
The tool, named AutoTimeline, is developed in Python3, reusing some code from Malhunt.
AutoTimeline automates a workflow similar to that I described in this article:
- Identify correct volatility profile for the memory image.
- Runs the timeliner plugin against volatile memory dump using volatility
- Runs the mftparser volatility plugin, in order to extract $MFT from memory and generate a bodyfile
- Runs the shellbags volatility plugin in order to generate a bodyfile of the user activity. (suggested by Matteo Cantoni)
- Merges the timeliner, mftparser and shellbags output files into a single bodyfile
- Sorts and filters the bodyfile using mactime and exports data as CSV.
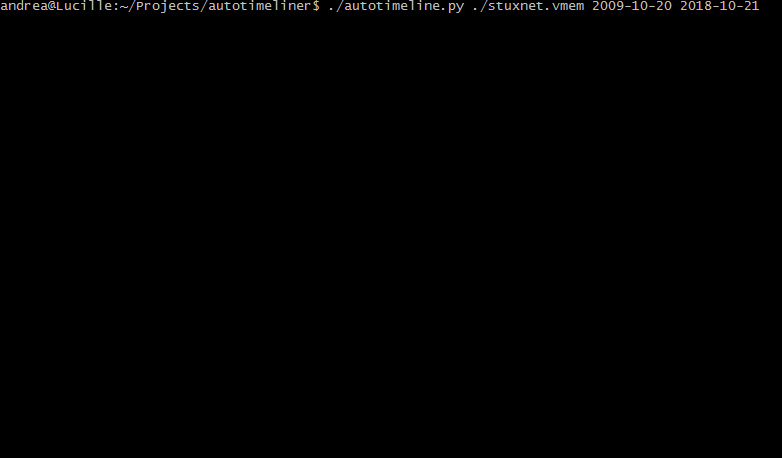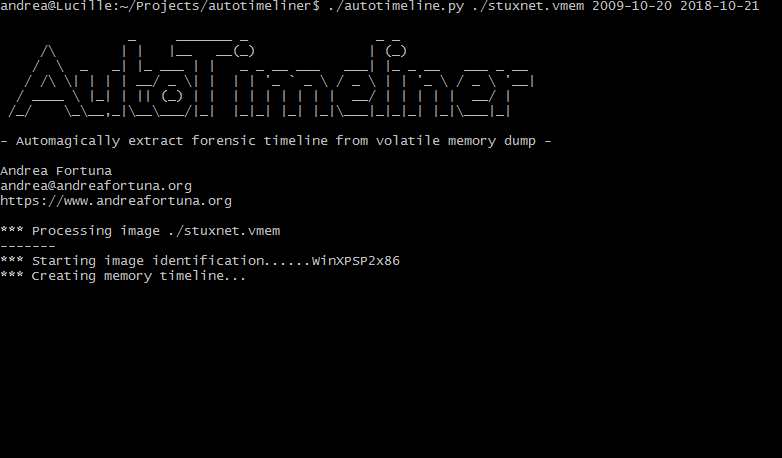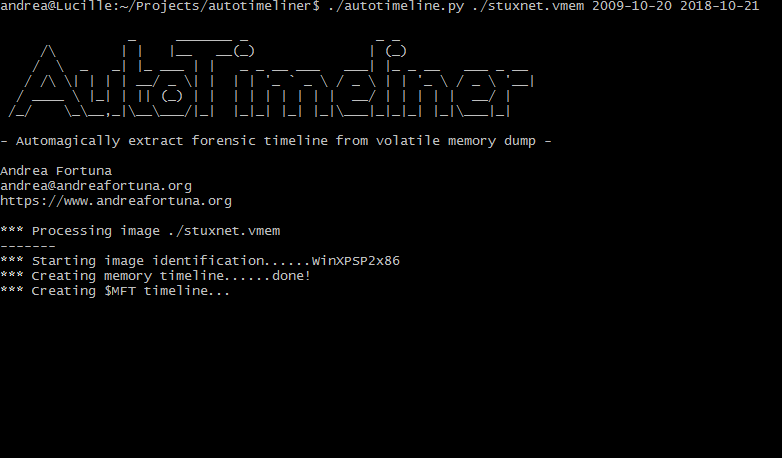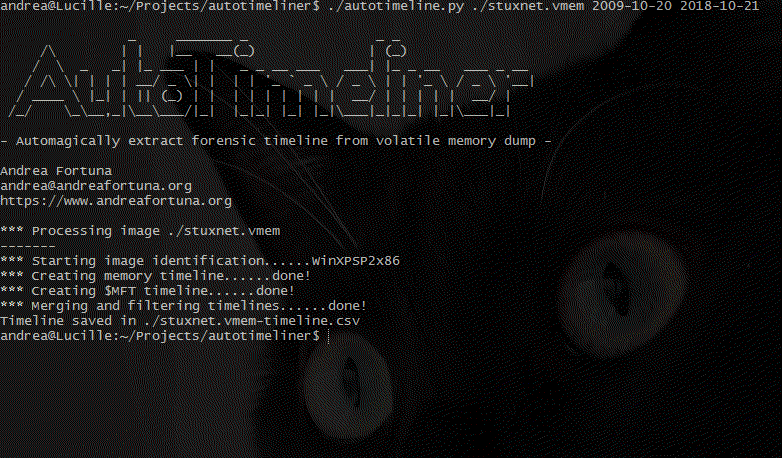
The tool allows the use of wildcards, in order to start the process (for example) on an entire directory containing a set of memory dumps.
Requirements
- Python 3
- Volatility
- SleuthKit
Installation
Simply clone the GitHub repository:
git clone https://github.com/andreafortuna/autotimeliner.git
Usage
autotimeline.py [-h] -f IMAGEFILE [-t TIMEFRAME] [-p CUSTOMPROFILE]
optional arguments:
-h, --help show this help message and exit
-f IMAGEFILE, --imagefile IMAGEFILE
Memory dump file
-t TIMEFRAME, --timeframe TIMEFRAME
Timeframe used to filter the timeline (YYYY-MM-DD
..YYYY-MM-DD)
-p CUSTOMPROFILE, --customprofile CUSTOMPROFILE
Jump image identifcation and use a custom memory
profileExamples
Extract timeline from TargetServerMemory.raw, limited to a timeframe from 2018-10-17 to 2018-10-21:
./autotimeline.py -f TargetServerMemory.raw -t 2018-10-17..2018-10-21
Extract timeline from all images in current directory, limited to a timeframe from 2018-10-17 to 2018-10-21:
./autotimeline.py -f ./*.raw -t 2018-10-17..2018-10-21
Extract timeline from TargetServerMemory.raw, using a custom memory profile:
./autotimeline.py -f TargetServerMemory.raw -p Win2008R2SP1x64
All timelines will be saved as $ORIGINALFILENAME-timeline.csv.