My Weekly RoundUp #87
Can Tesla's AI beat the Kobayashi Maru Test?
Technology
AT&T Archives: The UNIX Operating System
In the late 1960s, Bell Laboratories computer scientists Dennis Ritchie and Ken Thompson started work on a project that was inspired by an operating system called Multics, a joint project of MIT, GE, and Bell Labs. The host and narrator of this film, Victor Vyssotsky, also had worked on the Multics project. Ritchie and Thompson, recognizing some of the problems with the Multics OS, set out to create a more useful, flexible, and portable system for programmers to work with. What's fascinating about the growth of UNIX is the long amount of time that it was given to develop, almost organically, and based on the needs of the users and programmers. The first installation of the program was done as late as 1972 (on a NY Telephone branch computer). It was in conjunction with the refinement of the C programming language, principally designed by Dennis Ritchie. Because the Bell System had limitations placed by the government that prevented them from selling software, UNIX was made available under license to universities and the government. This helped further its development, as well as making it a more "open" system. This film "The UNIX System: Making Computers More Productive", is one of two that Bell Labs made in 1982 about UNIX's significance, impact and usability. Even 10 years after its first installation, it's still an introduction to the system. The other film, "The UNIX System: Making Computers Easier to Use", is roughly the same, only a little shorter. The former film was geared towards software developers and computer science students, the latter towards programmers specifically. The film contains interviews with primary developers Ritchie, Thompson, Brian Kernighan, and many others.
Adversarial Machine Learning against Tesla's Autopilot

Keen Security Lab has maintained the security research work on Tesla vehicle and shared our research results on Black Hat USA 2017 and 2018 in a row. Based on the ROOT privilege of the APE (Tesla Autopilot ECU, software version 18.6.1), we did some further interesting research work on this module. We analyzed the CAN messaging functions of APE, and successfully got remote control of the steering system in a contact-less way. We used an improved optimization algorithm to generate adversarial examples of the features (autowipers and lane recognition) which make decisions purely based on camera data, and successfully achieved the adversarial example attack in the physical world. In addition, we also found a potential high-risk design weakness of the lane recognition when the vehicle is in Autosteer mode. The whole article is divided into four parts: first a brief introduction of Autopilot, after that we will introduce how to send control commands from APE to control the steering system when the car is driving. In the last two sections, we will introduce the implementation details of the autowipers and lane recognition features, as well as our adversarial example attacking methods in the physical world.
https://www.schneier.com/blog/archives/2019/04/adversarial_mac.html
Cybersecurity
Researchers demonstrated that hackers can modify 3D Computer Tomography scans to add or remove evidence of a serious illness, including cancers

A group of researchers from the Ben-Gurion University and the Soroka University Medical Center, Beer-Sheva, in Israel, have demonstrated that hackers can modify 3D medical scans to the result of a clinical examination.
Attackers can add or remove evidence of various illnesses, including aneurysms, heart disease, blood clots, infections, arthritis, cartilage problems, torn ligaments, and tumors in the brain, heart or spine.
The experts developed proof-of-concept (PoC) malware that uses a machine learning technique known as generative adversarial network (GAN) to alter 3D images generated during a Computer Tomography (CT) scan.Scans are sent to picture archiving and communication systems (PACS) that store them. The format used to transmit and store the images is DICOM. GE Healthcare, Fujifilm, Philips, and RamSoft are main vendors of PACS systems.
https://securityaffairs.co/wordpress/83412/hacking/computer-tomography-scans-hack.html
Recovering Smartphone Typing from Microphone Sounds

We present the first acoustic side-channel attack that recovers what users type on the virtual keyboard of their touch-screen smartphone or tablet. When a user taps the screen with a finger, the tap generates a sound wave that propagates on the screen surface and in the air. We found the device's microphone(s) can recover this wave and "hear" the finger's touch, and the wave's distortions are characteristic of the tap's location on the screen. Hence, by recording audio through the built-in microphone(s), a malicious app can infer text as the user enters it on their device. We evaluate the effectiveness of the attack with 45 participants in a real-world environment on an Android tablet and an Android smartphone. For the tablet, we recover 61% of 200 4-digit PIN-codes within 20 attempts, even if the model is not trained with the victim's data. For the smartphone, we recover 9 words of size 7--13 letters with 50 attempts in a common side-channel attack benchmark. Our results suggest that it not always sufficient to rely on isolation mechanisms such as TrustZone to protect user input. We propose and discuss hardware, operating-system and application-level mechanisms to block this attack more effectively. Mobile devices may need a richer capability model, a more user-friendly notification system for sensor usage and a more thorough evaluation of the information leaked by the underlying hardware.
The Anatomy of a Hack: Perception vs. Reality

The number of data breaches has skyrocketed in recent years. Contrary to popular belief and Hollywood story lines, cyber-attacks are rarely carried out by legions of highly sophisticated coders gone rogue, deploying the most advanced techniques to penetrate organizations’ perimeter defenses. Reality paints a very different picture: cyber adversaries are no longer hacking to carry out data breaches ― they’re simply logging in by exploiting weak, stolen, or otherwise compromised credentials. Implementing an effective enterprise security strategy requires an understanding of hackers’ tactics, techniques, and procedures ― often called TTPs.
https://www.securityweek.com/anatomy-hack-perception-vs-reality
Privacy
540 Million Facebook User Records Found On unprotected AWS S3 Buckets

Researchers at the cybersecurity firm UpGuard today revealed that they discovered two datasets—one from a Mexican media company called Cultura Colectiva and another from a Facebook-integrated app called "At the pool"—both left publicly accessible on the Internet.
https://thehackernews.com/2019/04/facebook-app-database.html
Two companies exposed more than 540 million records containing information on Facebook users and their activities by leaving the data unprotected in Amazon Web Services (AWS) S3 buckets.
The data was discovered in recent months by risk management solutions provider UpGuard. The company’s researchers identified an unprotected S3 bucket belonging to a Mexico-based digital media publisher named Cultura Colectiva.
The bucket stored 146 gigabytes of files containing more than 540 million Facebook-related records, including account names, comments, likes, and Facebook IDs. It’s unclear how many unique users are impacted, but Cultura Colectiva, which publishes content for sharing on social media networks, has nearly 24 million followers on Facebook.
The second exposed AWS bucket was associated with a defunct application called “At the Pool.” This database also stored information on Facebook customers and their interests, but it also included names, email addresses and plaintext passwords for 22,000 users. While the passwords were likely associated with At the Pool accounts, they could have also exposed Facebook and other accounts to takeover attempts due to password reuse.https://www.securityweek.com/aws-s3-buckets-exposed-millions-facebook-records
Mark Zuckerberg Does Not Speak for the Internet

This past weekend, Facebook CEO Mark Zuckerberg took to the pages of the Washington Post to ask governments and regulators to play a more active role in policing the Internet, and to offer some ideas for how they should do so. As the New York Times noted, Zuckerberg’s comments were doubtless intended to stave off ideas Facebook would like even less—but that doesn’t make them good ones.
Here we look at two of Zuckerberg’s ideas for “standardized” or “global” rules for the entire Internet: platform censorship, and data privacy laws.https://www.eff.org/deeplinks/2019/04/mark-zuckerberg-does-not-speak-internet
Programming
The Next Release of PowerShell – PowerShell 7
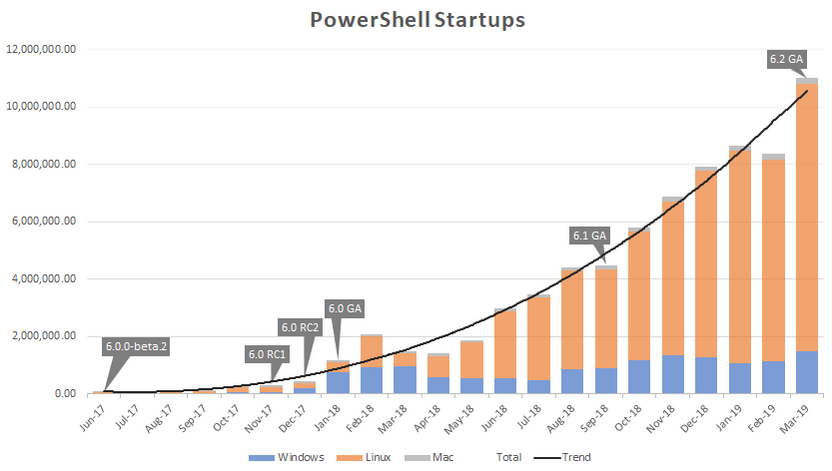
Microsoft announced the next version of PowerShell Core this week. The next version will be PowerShell 7 and not PowerShell Core 6.3 as many expected. It signals a significant change in the development of PowerPoint as Microsoft makes another important step in replacing the trusted PowerShell 5.1 on Windows with PowerShell Core.
PowerShell Core usage increased significantly in the past two years especially on Linux platforms. Windows usage has stagnated on the other hand for the most part. Microsoft explains the lack of progress on the Windows platform with the existence of PowerShell 5.1 which offers functionality that PowerShell Core does not support
SciFi
Can You Beat The Kobayashi Maru Test?
The Kobayashi Maru is a training exercise in the fictional Star Trek universe designed to test the character of Starfleet Academy cadets in a no-win scenario. The Kobayashi Maru test was first depicted in the opening scene of the film Star Trek II: The Wrath of Khan and also appears in the 2009 film Star Trek. Screenwriter Jack B. Sowards is credited with inventing the test. The test’s name is occasionally used among Star Trek fans or those familiar with the series to describe a no-win scenario, a test of one’s character or a solution that involves redefining the problem.
'Game of Thrones' composer looks back on that iconic theme song
Game of Thrones composer Ramin Djawadi has never read A Song of Ice and Fire. He'll get to someday – he's been a bit busy for the past nine years working on the Emmy-winning Game of Thrones score.
Before Thrones, Djawadi had done a handful of TV and film scoring, including the MCU-launching Iron Man soundtrack. His work caught the attention of Game of Thrones showrunners David Benioff and D.B. Weiss, who scheduled a meeting and showed him the first two episodes.
Djawadi got to work immediately, yielding one of the most indelible television or film scores of our generation and a theme song that, to be perfectly honest, slaps.Djawadi recently spoke with Mashable about the new season, the iconic theme, and more.