Google researchers reveals iOS's exploit chains that changes everything we know about iPhone security
Security researchers from Google’s Project Zero team say they have discovered a number of compromized websites which used previously undisclosed security flaws to attack any iPhone that visited them.
"There was no target discrimination; simply visiting the hacked site was enough for the exploit server to attack your device, and if it was successful, install a monitoring implant. We estimate that these sites receive thousands of visitors per week," Ian Beer, from Google's Project Zero, wrote in a blog post published Thursday.
https://www.vice.com/en_us/article/bjwne5/malicious-websites-hacked-iphones-for-years
According to Motherboard, the attack could be one of the largest ever conducted against iPhone users: if a user visited one of the malicious websites using a vulnerable device, then their personal files, messages, and real time location data could be stolen.
Once the attack has successfully exploited the iPhone, it can deploy malware onto the phone.
In this case "the implant is primarily focused on stealing files and uploading live location data. The implant requests commands from a command and control server every 60 seconds," Beer writes.
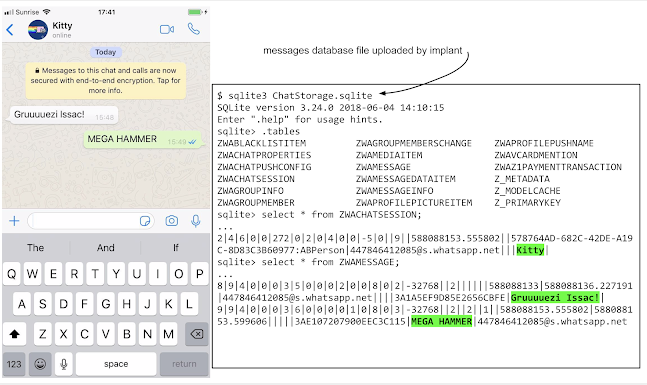
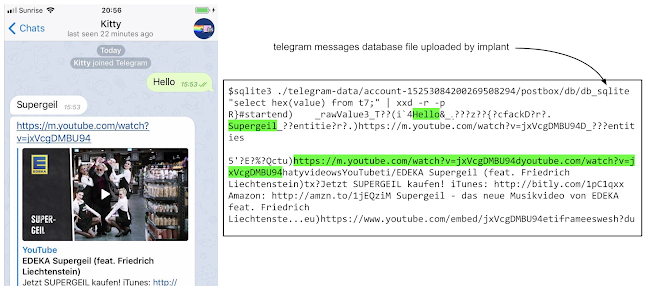
The implant also has access to the user's keychain, which contains passwords, as well as the databases of various end-to-end encrypted messaging apps, such as Telegram, WhatsApp, and iMessage, Beer's post continues. End-to-end encryption can protect messages from being read if they're intercepted, but less so if a hacker has compromised the end device itself.
The implant does not have persistence though; if a user reboots their iPhone, it will wipe the malware, Beer explains. But one infection can still of course deliver a treasure trove of sensitive information.https://www.vice.com/en_us/article/bjwne5/malicious-websites-hacked-iphones-for-years
Google's reseacrhers posted a very deep dive detailing the exploits, disclosed to Apple in Feb. 2019.

The team found five "separate, complete and unique" exploit chains using 14 vulnerabilities. Several were zero-day, meaning Apple was unaware of them at the time of Project Zero's discovery; Apple patched these within the seven-day deadline Google gave in iOS 12.1.4, the same Feb. 7 update that patched the Group FaceTime vulnerability.
The 14 vulnerabilities span across Safari and the kernel, aside from two separate instances of sandbox escapes, granting elevated “root” access to an attacker, giving it full permissions to install malware and access files also the databases of end-to-end encrypted messaging apps, such as Telegram, WhatsApp, and iMessage:
The implant has access to all the database files (on the victim’s phone) used by popular end-to-end encryption apps like Whatsapp, Telegram and iMessage.
https://googleprojectzero.blogspot.com/2019/08/implant-teardown.html
References
- https://googleprojectzero.blogspot.com/2019/08/a-very-deep-dive-into-ios-exploit.html
- iOS Exploit Chain #1
- iOS Exploit Chain #2
- iOS Exploit Chain #3
- iOS Exploit Chain #4
- iOS Exploit Chain #5
- JSC Exploits
- Implant Teardown
- https://support.apple.com/en-us/HT209520
- https://www.securityweek.com/apple-patches-facetime-spying-vulnerability