Vulnerabilities in 5G protocol may allows to track users and make fake emergency alerts
Security researchers at Purdue University and the University of Iowa have found new vulnerabilities that can be used to track a victim’s real-time location, spoof emergency alerts or silently disconnect a phone from the 5G network.
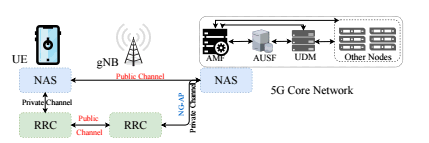
Despite some net neutrality concerns [3], 5G is said to be more fast and secure than its 4G predecessor, able to avoid exploits used to target users of older cellular network protocols like the use of cell site simulators — known as “stingrays” [2].
However, a research team, composed by Syed Rafiul Hussain, Imtiaz Karim and Elisa Bertino from Purdue University, Mitziu Echeverria and Omar Chowdhury from University of Iowa has expanded a previous research to build a new tool, dubbed 5GReasoner [1], which was used to find new vulnerabilities, confirming that 5G has weaknesses that undermine its security and privacy.
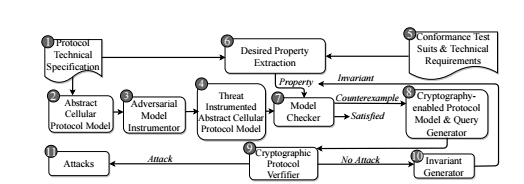
By creating a malicious radio base station, an attacker can carry out several attacks against a target’s connected phone:
The imminent deployment of the fifth generation (5G) cellular network has created a lot of enthusiasm in both industry and academia particularly due to its promise of enabling new applications such as smart vehicles and remote robotic surgery. 5G is not only envisioned as a replacement of home broadband Internet but also is expected to have impact in the military battlefield and emergency management by improving situational awareness. All these potential novel and critical applications of 5G can be attributed to its following enhancements over 4G LTE:
1 - Improvements in the physical-layer technologies enabling the support of large numbers of devices with substantially improved bandwidth;
2 - Robust security posture due to the introduction of security measures in the upper-layer of the 5G protocol stack.
The 5G standard, however, has opened the door to a wide array of new security challenges stemming from:
- New security policies that are not formally verified against adversarial assumptions;
- Retaining security mechanisms from 4G Long Term Evolution (LTE) and its predecessors.This paper thus aims to develop highly automated approaches enabling property-guided formal verification of control-plane protocols of the 5G protocol stack.
In one example attack, the researchers said they were able to obtain both old and new temporary network identifiers of a victim’s phone, allowing them to track the phone’s location, or even to broadcast fake emergency alerts.
Another attack could be used to create a denial-of-service condition against a target’s phone, disconnecting it from the cellular network.
In some cases, the vulnerabilities could be used to downgrade a cellular connection to a less-secure standard, which makes it possible to launch surveillance attacks against targets using specialist “stingray” [2] equipment.
According with the researchers, all of the new attacks can be exploited with a low-cost radio equipment and a practical knowledge of 4G and 5G networks.