ATFuzzer: exploiting AT commands on Android basebands using malicious USB and Bluetooth accessories
Researchers at Purdue College and University of Iowa have revealed a paper detailing how the baseband processors of a large number of common Android smartphones may be compromised using malicious USB and Bluetooth accessories.
The research team is, for the most, similar to the same that has published the 5GReasoner paper on 5G protocol vulnerabilities: Syed Rafiul Hussain. Imtiaz Karim, Fabrizio Cicala, Elisa Bertino from Purdue University, and Omar Chowdhury from the University of Iowa.
How it works?
Through the use of specifically crafted Bluetooth or USB equipment, the researchers had been capable to execute AT instructions directly on the device firmware, the software that allows the phone’s modem to communicate with the cell network, such as making phone calls or connecting to the internet.
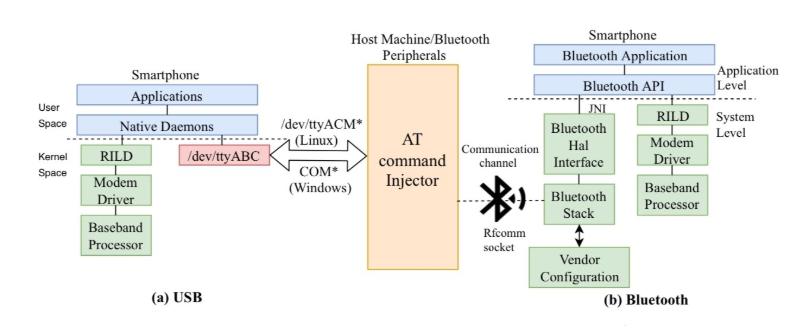
Using this technique, the experts gathered critical information such as the IMEI number, roaming status, and network settings (that can help to locate the targets), interrupted Internet connections and enabled functions such as Do Not Disturb, call blocking, call forwarding and so on.
The vulnerabilities are found in the interface used to communicate with the baseband that is typically off-limits from the rest of the device, including its apps, and often come with command blacklisting to prevent non-critical commands from running.
But the researchers found that many Android phones inadvertently allows Bluetooth and USB accessories — like headphones and headsets — to access the baseband.
This paper focuses on checking the correctness and robustness of the AT command interface exposed by the cellular baseband processor through Bluetooth and USB. A device’s application processor uses this interface for issuing high-level commands (or, AT commands) to the baseband processor for performing cellular network operations (e.g., placing a phone call). Vulnerabilities in this interface can be leveraged by malicious Bluetooth peripherals to launch pernicious attacks including DoS and privacy attacks. To identify such vulnerabilities, we propose ATFuzzer that uses a grammarguided evolutionary fuzzing approach which mutates production rules of the AT command grammar instead of concrete AT commands. Empirical evaluation with ATFuzzer on 10 Android smartphones from 6 vendors revealed 4 invalid AT command grammars over Bluetooth and 13 over USB with implications ranging from DoS, downgrade of cellular protocol version (e.g., from 4G to 3G/2G) to severe privacy leaks. The vulnerabilities along with the invalid AT command grammars were responsibly disclosed to affected vendors. Among the vulnerabilities uncovered, 2 CVEs (CVE-2019-16400 and CVE-2019-16401) have already been assigned for the DoS and privacy leaks attacks, respectively.
Which devices are vulnerable?
Devices from six producers had been examined (Samsung, LG, HTC, Google, Motorola and Huawei), and not all had been discovered to be vulnerable to each USB and Bluetooth assault vectors.
The affected phones used baseband processors manufactured by Qualcomm, Samsung, and HiSilicon (a subsidiary of Huawei).
Is there a patch?
The researchers notified the affected baseband vendors, and waited the standard 90 days before going public with their findings, in a technical paper [2] and a GitHub repository [1]. Finally, research team will present its findings also at ACSAC2019 [3].
Currently, only Samsung has committed to releasing patches for its devices.
How to mitigate this threat?
Obiously, the suggestion is do not to use accessories that are not known.
Further, using public chargers is strictly discouraged.
Using only trusted accessories is currently the only solution to the problem.