How to extract forensic artifacts from Linux swap
In order to expand the address space that is effectively usable by a process and to expand the amount of dynamic RAM, modern operating systems use the method known as swapping.
In Linux systems this typically shows up in the form of a hard disk partition devoted to this task, but swap areas can be stored in files as well.
A lot of interesting artifacts can be found in the swap space, like local account clear-text passwords, web login/passwords, email addresses, wifi network SSID and keys, Samba credentials and more.
In order to extract this information from linux swap, you can use swap_digger [1], a bash script developed by Emeric Nasi that applies several techniques in order to parse useful information from swap partitions/dumps.
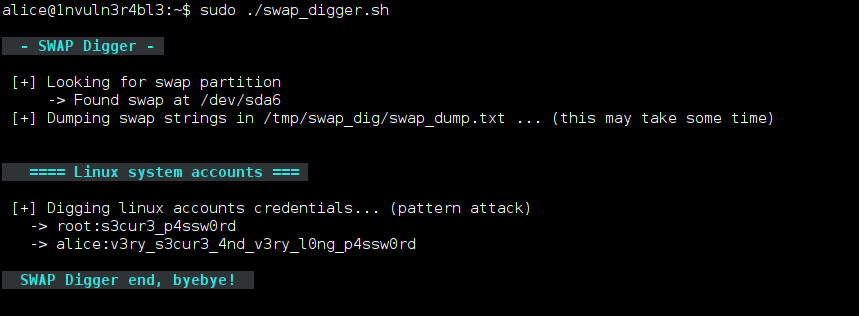
How to use swap_digger
On your machine
Use the following commands to download and run the script on your machine:
git clone https://github.com/sevagas/swap_digger.git cd swap_digger chmod +x swap_digger.sh sudo ./swap_digger.sh -vx
On a mounted hard drive
To use swap_digger on a mounted hard drive, do the following:
First, download the script using the following commands:
git clone https://github.com/sevagas/swap_digger.git cd swap_digger chmod +x swap_digger.sh
Then, find the target swap file/partition with:
sudo ./swap_digger.sh -S
Finally, analyze the target by running:
sudo ./swap_digger.sh -vx -r path/to/mounted/target/root/fs -s path/to/target/swap/device
On a third party machine
Use the following commands to download and run the script on a third party machine:
wget https://raw.githubusercontent.com/sevagas/swap_digger/master/swap_digger.sh chmod +x swap_digger.sh sudo ./swap_digger.sh -vx -c
Note: Use the -c option to automatically remove the directory created by swap_digger (/tmp/swap_dig).