QBot malware returns with new techniques in corporate attacks
QBot, a dangerous Windows banking Trojan, is being used in a new series of attacks against corporate targets.
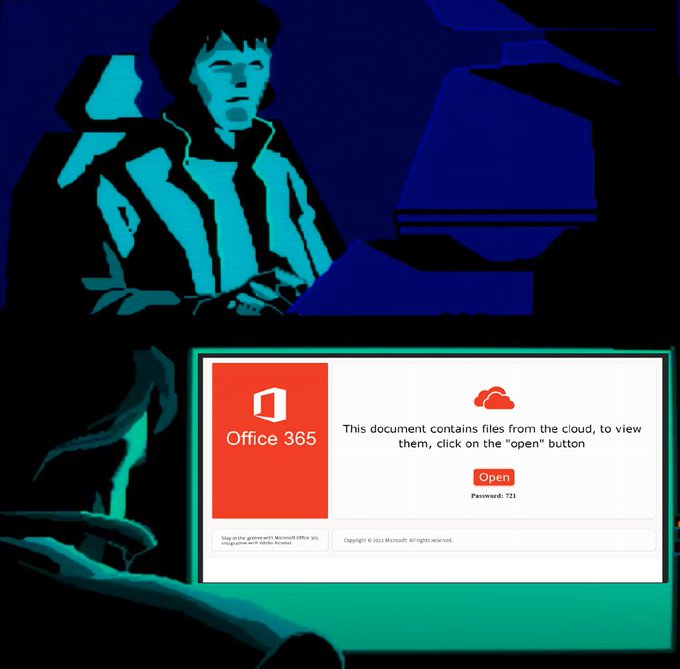
Cybercriminals are using new techniques to distribute the malware, including email phishing scams: infiltrating email conversations and tricking users into downloading a PDF attachment that actually contains a Windows script file.
According to a short report published on Twitter by cybersecurity researcher Cryptolaemus, when executed the file runs PowerShell code that downloads a DLL file containing the QBot Trojan.
The malware can steal passwords and cookies from browsers, access emails, download other payloads, including ransomware such as BlackBasta, and use Cobalt Strike to spread the infection across the network.
Indicators of Compromise
| URL/IP/HASH |
|---|
| hxxps://bebessi[.]com.tr/Q9QbSi/puangaKPpjD |
| hxxps://comunidadehebrom[.]com.br/0P16/i4dlZCkHEk |
| hxxps://theyoungandtheratchet[.]com/IzvO/EuVTmZEBRFw |
| hxxp://unitedec-eg[.]com/IFU6llZ/cO5RcAa |
| hxxps://thewatchzonebd[.]com/tkh4PH/SBL8BMSeA2rY |
| hxxps://blogdocisneiros[.]com.br/GOm/lD1vhf |
| hxxps://immunoliderazgoyoportunidad[.]com/xqa6Cny/Qt0pPfeBAM |
| hxxps://cozarqingenieria[.]com.mx/R5Awkh4/JZGpFCLYUsr |
| hxxps://propertynear.co[.]uk/QyYWyp/XRgRWEdFv |
| hxxps://graficalevi.com[.]br/0p6P/R94icuyQ |
| hxxp://rosewoodlaminates[.]com/hea/yWY9SJ4VOH |
| hxxps://chimpcity[.]com/h7e/p5FuepRZjx |
| hxxps://kmphi[.]com/FWovmB/8oZ0BOV5HqEX |
| hxxps://theshirtsummit[.]com/MwBGSm/lGP5mGh |
| hxxps://capitalperurrhh[.]com/vQ1iQg/u6oL8xlJ |
| hxxps://agtendelperu[.]com/FPu0Fa/EpN5Xvh |
| hxxps://centerkick[.]com/IC5EQ8/2v6u6vKQwk8 |
| 109.218.86.223:2222 |
| 78.130.215.67:443 |
| 70.112.206.5:443 |
| 12.172.173.82:50001 |
| 201.244.108.183:995 |
| 96.87.28.170:2222 |
| 76.80.180.154:993 |
| 95.60.243.24:995 |
| 87.202.101.164:50000 |
| 86.225.214.138:2222 |
| 74.66.134.24:443 |
| 72.203.216.98:2222 |
| 92.239.81.124:443 |
| 37.189.1.102:443 |
| 144.64.226.144:443 |
| 202.142.98.62:443 |
| 12.172.173.82:993 |
| 71.171.83.69:443 |
| 139.226.47.229:995 |
| 197.204.234.123:443 |
| 92.1.170.110:995 |
| 47.205.25.170:443 |
| 37.14.229.220:2222 |
| 92.20.204.198:2222 |
| 184.161.74.73:443 |
| 92.27.86.48:2222 |
| 84.215.202.8:443 |
| 92.154.17.149:2222 |
| 100.10.72.114:443 |
| 88.122.133.88:32100 |
| 176.171.4.107:2222 |
| 78.16.156.25:443 |
| 27.99.32.26:2222 |
| 86.98.23.66:443 |
| 119.82.123.160:443 |
| 116.75.63.150:443 |
| 103.42.86.42:995 |
| 103.212.19.254:995 |
| 190.191.35.122:443 |
| 12.172.173.82:2087 |
| 90.55.106.37:2222 |
| 116.72.250.18:443 |
| 202.142.98.62:995 |
| 122.184.143.83:443 |
| 85.241.180.94:443 |
| 103.140.174.20:2222 |
| 50.68.204.71:995 |
| 109.150.179.215:2222 |
| 12.172.173.82:465 |
| 27.109.19.90:2078 |
| 123.3.240.16:995 |
| 69.119.123.159:2222 |
| 77.126.11.114:443 |
| 91.82.133.77:443 |
| 74.92.243.115:50000 |
| 12.172.173.82:21 |
| 73.36.196.11:443 |
| 172.115.17.50:443 |
| 112.222.83.147:6881 |
| 69.133.162.35:443 |
| 45.50.233.214:443 |
| 27.0.48.233:443 |
| 78.192.109.105:2222 |
| 178.175.187.254:443 |
| 88.164.20.177:21 |
| 47.21.51.138:443 |
| 43.243.215.206:443 |
| 49.245.95.124:2222 |
| 12.172.173.82:32101 |
| 87.223.89.244:443 |
| 188.79.242.89:2222 |
| 50.68.204.71:443 |
| 84.35.26.14:995 |
| 35.143.97.145:995 |
| 184.153.132.82:443 |
| 76.170.252.153:995 |
| 2.82.8.80:443 |
| 47.34.30.133:443 |
| 81.229.117.95:2222 |
| 50.68.204.71:993 |
| 103.111.70.66:443 |
| 12.172.173.82:22 |
| 24.236.90.196:2078 |
| 114.143.176.235:443 |
| 103.144.201.53:2078 |
| 157.119.85.203:443 |
| 103.111.70.66:995 |
| 202.184.218.218:443 |
| 109.154.254.126:2222 |
| 125.99.76.102:443 |
| 86.195.14.72:2222 |
| 80.13.205.69:2222 |
| 50.68.186.195:443 |
| 176.142.207.63:443 |
| 78.69.251.252:2222 |
| 213.91.235.146:443 |
| 122.186.210.254:443 |
| 174.4.89.3:443 |
| 75.143.236.149:443 |
| 198.2.51.242:993 |
| 82.41.36.110:22 |
| 75.90.114.237:995 |
| 109.11.175.42:2222 |
| 151.62.55.207:443 |
| 197.0.146.16:443 |
| 71.38.155.217:443 |
| 12.172.173.82:20 |
| 162.248.14.107:443 |
| 98.145.23.67:443 |
| 86.154.216.221:2222 |
| 84.155.13.118:995 |
| 70.160.80.210:443 |
| 103.113.68.33:443 |
| 193.253.100.236:2222 |
| 12.172.173.82:995 |
| 72.134.124.16:443 |
| 108.32.72.145:443 |
| 161.142.103.5:995 |
| 86.143.119.184:995 |
| 197.1.218.172:443 |
| 8c30e0e3546829c7c7007b2720151342b945a6593be960cd060cee17829c95cd |
| d7608b8f684e7465599a4673fefa329de646e38d934dd79e592288c68720bcfa |