North Korea-Linked APT group BlueNoroff uses new macOS malware RustBucket in recent attacks
North Korea-linked BlueNoroff APT group has been observed by security firm Jamf using a new macOS malware called RustBucket in recent attacks.
The RustBucket malware allows operators to download and execute various payloads.
The first-stage was contained within an unsigned application named Internal PDF Viewer.app, which can only be executed by manually overriding the Gatekeeper security measure.
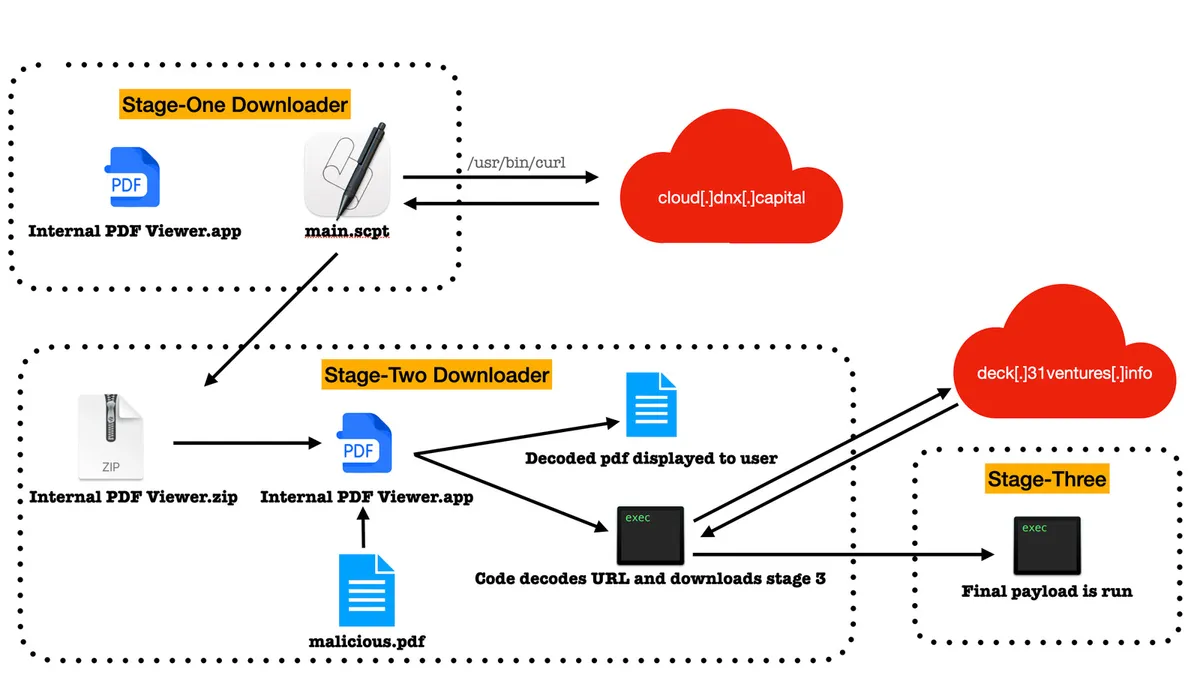
The stage-two of the malware communicates with the C2 server to fetch the stage-three payload, which is an ad-hoc signed trojan written in the Rust language. The trojan can run on both ARM and x86 architectures.
The third-stage payload allows the attacker to carry out a broad range of malicious activities on the system.
The attribution to the BlueNoroff APT group is based on the domain cloud[.]dnx[.]capital used in the stage-one dropper and the use of fake domains impersonating venture capital firms and banks. The experts believe that more APT groups may start attacking macOS.
Indicators of Compromise
| HASH/Domain |
|---|
| cloud[.]dnx[.]capital |
| deck[.]31ventures[.]info |
| dabb4372050264f389b8adcf239366860662ac52 |
| 0be69bb9836b2a266bfd9a8b93bb412b6e4ce1be |
| e0e42ac374443500c236721341612865cd3d1eec |
| ac08406818bbf4fe24ea04bfd72f747c89174bdb |
| 72167ec09d62cdfb04698c3f96a6131dceb24a9c |
| fd1cef5abe3e0c275671916a1f3a566f13489416! |
| ca59874172660e6180af2815c3a42c85169aa0b2 |
| d9f1392fb7ed010a0ecc4f819782c179efde9687 |
| 9121509d674091ce1f5f30e9a372b5dcf9bcd257 |
| a1a85cba1bc4ac9f6eafc548b1454f57b4dff7e0 |
| 7a5d57c7e2b0c8ab7d60f7a7c7f4649f33fea8aa |
| 182760cbe11fa0316abfb8b7b00b63f83159f5aa |
| 7e69cb4f9c37fad13de85e91b5a05a816d14f490 |
| be234cb6819039d6a1d3b1a205b9f74b6935bbcc |
| 469236d0054a270e117a2621f70f2a494e7fb823 |
| e7158bb75adf27262ec3b0f2ca73c802a6222379 |