Volume Shadow Copies in forensic analysis
Integral part to the Windows Operating System and essential for DFIR analysts
Shadow Copy (also known as Volume Snapshot Service, Volume Shadow Copy Service or VSS) is a technology included in Microsoft Windows that allows taking manual or automatic backup copies or snapshots of computer files or volumes, even when they are in use.
It is implemented as a Windows service called the Volume Shadow Copy service and requires the file system to be NTFS in order to create and store shadow copies: Shadow Copies can be created on local and external volumes by any Windows component that uses this technology.
Overview
VSS operates at the block level of volumes.
A snapshot is a read-only point-in-time copy of the volume that allows the creation of consistent backups of a volume, ensuring that the contents do not change and are not locked while the backup is being made.
The core component of shadow copy is the Volume Shadow Copy service, which initiates and oversees the snapshot creation process, performing all necessary data transfers using components called providers.
Windows comes with a default System Provider, but software and hardware vendors can create their own software or hardware providers and register them with Volume Shadow Copy service.
Other components that are involved in the snapshot creation process are writers, used for aim of Shadow Copy is to create consistent reliable snapshots or to complete a series of inter-related changes to several related files.
Each writer is application-specific and has 60 seconds to establish a backup-safe state before providers start snapshot creation. If the Volume Shadow Copy service does not receive acknowledgement of success from the corresponding writers with this time-frame, it fails the operation.
Initially snapshots are temporary, they do not survive a reboot: the ability to create persistent snapshots was added in Windows Server 2003 onward.
The end result is similar to a versioning file system, allowing any file to be retrieved as it existed at the time any of the snapshots was made.
VSS differences between Windows Versions
Windows XP and Server 2003
Volume Snapshot Service was first added to Microsoft Windows in Windows XP.
It can only create temporary snapshots, used for accessing stable on-disk version of files that are opened for editing (and therefore locked).
This version of VSS is used by NTBackup.
The creation of persistent snapshots (which remain available across reboots until specifically deleted) has been added in Windows Server 2003, allowing up to 512 snapshots to exist simultaneously for the same volume.
In Windows Server 2003, VSS is used to create incremental periodic snapshots of data of changed files over time.
Its client component is included with Windows XP SP2 or later, and is available for installation on Windows 2000 SP3 or later, as well as Windows XP RTM or SP1.
Windows XP and later include a command line utility called vssadmin that can list, create or delete volume shadow copies and list installed shadow copy writers and providers.
Windows Vista, 7 and Server 2008
Backup and Restore in Windows Vista, Windows Server 2008, Windows 7 and Windows Server 2008 R2 use shadow copies of files in both file-based and sector-by-sector backup.
The System Protection component uses VSS when creating and maintaining periodic copies of system and user data on the same local volume (similar to the Shadow Copies for Shared Folders feature in Windows Server) and allows reverting to an entire previous set of shadow copies called a restore point.
Furthermore, the Previous Versions feature in Windows Explorer allows restoring individual files or folders locally from restore points as they existed at the time of the snapshot.
Finally, Windows Server 2008 introduces the diskshadow utility which exposes VSS functionality through 20 different commands.
The system creates shadow copies automatically once per day, or when triggered by the backup utility or installer applications which create a restore point.
Windows 8 and Server 2012
Windows 8 supports persistent shadow copies but lacks the GUI portion necessary to browse them: the ability to browse, search or recover older versions of files via the Previous Versions tab of the Properties dialog of files was removed for local volumes.
That functionality can be recovered using third party tools, such as ShadowExplorer.
The feature is fully available in Windows Server 2012.
Windows 10
Windows 10 restored the Previous Versions tab that was removed in Windows 8.
However, it depends on the File History feature now instead of Volume Shadow copy.
Compatibility
While the different NTFS versions have a certain degree of both forward and backward compatibility, there are certain issues when mounting newer NTFS volumes containing persistent shadow copies in older versions of Windows.
This happens because the older operating system does not understand the newer format of persistent shadow copies.
Shadow Volume Copies in Digital Forensics
Why Shadow Copies are important to Forensics
Windows Shadow Volumes can provide additional data that otherwise would not be available.
They can allow a forensic investigator to recover deleted files, and to learn what was taking place on a system before he/she began the investigation.
They are an excellent tool for discovering data that was previously deleted by a system user.
Limitations of Shadow Copies in forensic investigations
Although Shadow Copies can provide forensic investigators with files that have been deleted between the time the Shadow Copy was made and the time the investigation began, they only provide one previous version of files.
If previous changes to files were made before the Shadow Copy was created, those changes will not be known.
Because Shadow Copies clone on a block-level rather than a file-level, changes to individual files may not be enough to cause Windows to make the changes in a corresponding Shadow Copy.
Additionally, the Shadow Copy service might be turned off by the user, resulting in no Shadow Copies being stored.
Other times, the disk space settings might be set too low for multiple Shadow Copies to be saved, or even for one Shadow Copy to be saved if it is larger than what the settings allow.
Furthermore, Windows automatically overwrites Shadow Copies when the disk space limit is reached, so Shadow Copies should be an aid in a forensic investigation, but they are not guaranteed as a means to discover useful information.
Volume Shadow Copies in the Registry
We can also recover information about our Volume Shadow Copies, and their characteristics, from the Windows Registry. There are multiple locations of interest, especially as this is a Windows service. The following registry key provides information on the service itself:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\VSS
For this post, I’ll focus on the following registry key:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\BackupRestore
Within this path, we’ve got three subkeys:
- FilesNotToBackup — specifies files that should not be backed up or restored.
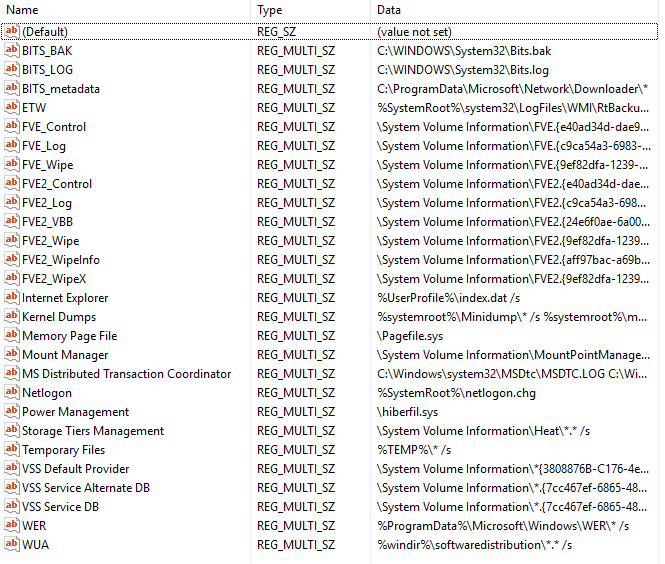
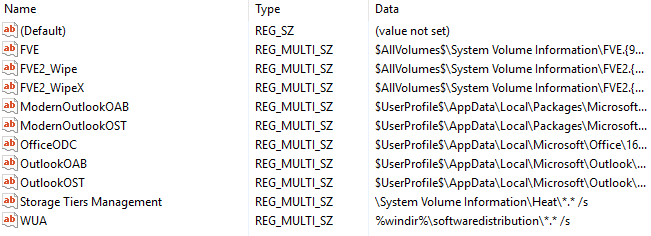
- FilesNotToSnapshot (only Vista/2008+) — Specify files that should be deleted from newly-created shadow copies
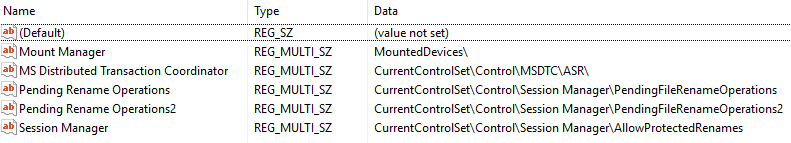
- KeysNotToRestore — Provides the names of registry keys and values that backup applications should not restore.
If you ever find any discrepancies on a system that you are analyzing, I’d recommend pulling these registry keys and determining if there was a configuration change that altered data within a VSC.
Analyzing Volume Shadow Copies
Some suggestions by https://medium.com/@mbromileyDFIR :
When incorporating VSCs into your analysis, consider the following possibilities:
- When using tools such as libvshadow, that can give you a representation of the Volume Shadow Copy as a logical volume, you can apply secondary-analysis tools such as log2timeline/Plaso, and create massive, MEGA supertimelines that peek further back in history. Just note you might have an excess of the same data; use tools to de-dupe and you’ll be in a good spot.
- If you have indicators to assist in analysis, such as malware or timeframes of interest, observe how your volume shadow copies interact with these timeframes. You may find yourself in a situation where you can peek at the system prior to infection. Additionally, if you have suspicions of timestomping, see if your Volume Shadow Copies back up that theory.
- Just because data is within a Volume Shadow Copy, it doesn’t mean analysis techniques have to change. We can still run automated scripts, hash files, perform keyword searches, etc. This is just another data source!
References
[embed]http://www.forensicswiki.org/wiki/Windows_Shadow_Volumes[/embed]
https://technet.microsoft.com/it-it/library/ee923636(v=ws.10).aspx