WPSeku: a Black-box Wordpress Security Scanner
WPSeku is a Black-box WordPress vulnerability scanner that can be used to scan remote WordPress installations to find security issues.
What is a Black-box scanner?
Black-box security testing refers to a method of software security testing in which the security controls, defences and design of an application are tested from the outside-in, with little or no prior knowledge of the application’s internal workings.
Essentially, black-box testing takes an approach similar to that of a real attacker.
(from Acunetix.com)
WPSeku is developed and mantained by m4ll0k, that have also developed other interesting security tools, like Infoga and Spaghetti.
The last available version is the 0.2.1 and can be downloaded from GitHub.
Installation
First, install requests:
# pip install requests
After, clone the git repository:
# git clone https://github.com/m4ll0k/WPSeku.git
Finally, start the tool:
# python wpseku.py
Usage
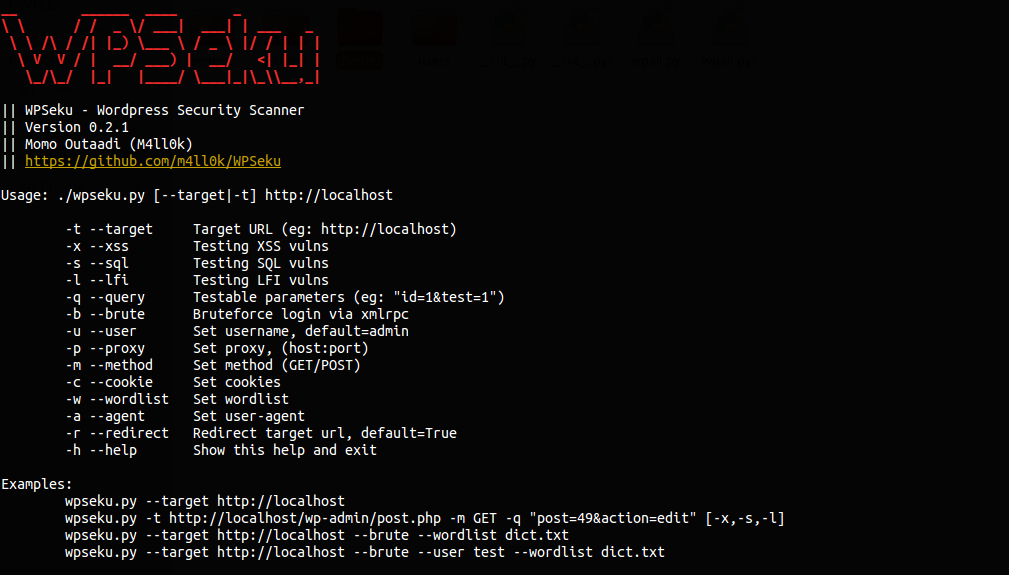
Usage: ./wpseku.py [--target|-t] http://localhost
-t --target Target URL (eg: http://localhost)
-x --xss Testing XSS vulns
-s --sql Testing SQL vulns
-l --lfi Testing LFI vulns
-q --query Testable parameters (eg: "id=1&test=1")
-b --brute Bruteforce login via xmlrpc
-u --user Set username, default=admin
-p --proxy Set proxy, (host:port)
-m --method Set method (GET/POST)
-c --cookie Set cookies
-w --wordlist Set wordlist
-a --agent Set user-agent
-r --redirect Redirect target url, default=True
-h --help Show this help and exit
Examples:
wpseku.py --target http://localhost
wpseku.py -t http://localhost/wp-admin/post.php -m GET -q "post=49&action=edit" [-x,-s,-l]
wpseku.py --target http://localhost --brute --wordlist dict.txt
wpseku.py --target http://localhost --brute --user test --wordlist dict.txt