How to retrieve user's passwords from a Windows memory dump using Volatility
About Volatility i have written a lot of tutorials, now let's try to use this information in a real context extracting the password hashes from a windows memory dump, in 4 simple steps.
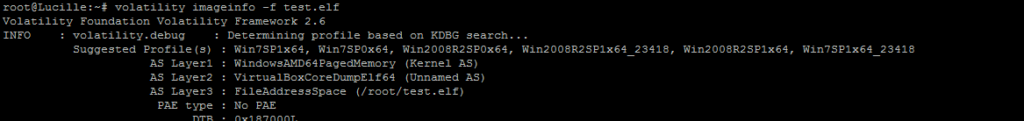
1. Identify the memory profile
First, we need to identify the correct profile of the system:
root@Lucille:~# volatility imageinfo -f test.elf
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search...
Suggested Profile(s) : Win7SP1x64, Win7SP0x64, Win2008R2SP0x64, Win2008R2SP1x64_23418, Win2008R2SP1x64, Win7SP1x64_23418
AS Layer1 : WindowsAMD64PagedMemory (Kernel AS)
AS Layer2 : VirtualBoxCoreDumpElf64 (Unnamed AS)
AS Layer3 : FileAddressSpace (/root/test.elf)
PAE type : No PAE
DTB : 0x187000L
KDBG : 0xf80001a4a110L
Number of Processors : 2
Image Type (Service Pack) : 1
KPCR for CPU 0 : 0xfffff80001a4bd00L
KPCR for CPU 1 : 0xfffff880009c5000L
KUSER_SHARED_DATA : 0xfffff78000000000L
Image date and time : 2017-11-03 09:22:45 UTC+0000
Image local date and time : 2017-11-03 10:22:45 +0100
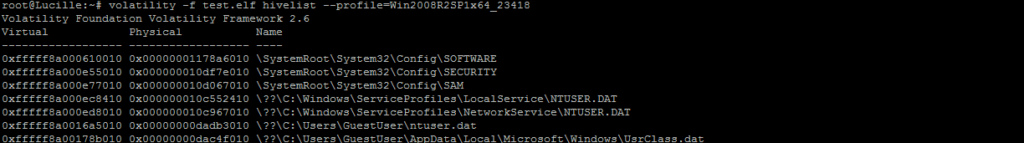
2. List the registry hive
With the correct profile, we can use the "hivelist' plugin in order to extract the list of registry hive in the memory dump:
root@Lucille:~# volatility -f test.elf hivelist --profile=Win2008R2SP1x64_23418
Volatility Foundation Volatility Framework 2.6
Virtual Physical Name
0xfffff8a000610010 0x00000001178a6010 \SystemRoot\System32\Config\SOFTWARE
0xfffff8a000e55010 0x000000010df7e010 \SystemRoot\System32\Config\SECURITY
0xfffff8a000e77010 0x000000010d067010 \SystemRoot\System32\Config\SAM
0xfffff8a000ec8410 0x000000010c552410 \??\C:\Windows\ServiceProfiles\LocalService\NTUSER.DAT
0xfffff8a000ed8010 0x000000010c967010 \??\C:\Windows\ServiceProfiles\NetworkService\NTUSER.DAT
0xfffff8a0016a5010 0x00000000dadb3010 \??\C:\Users\GuestUser\ntuser.dat
0xfffff8a00178b010 0x00000000dac4f010 \??\C:\Users\GuestUser\AppData\Local\Microsoft\Windows\UsrClass.dat
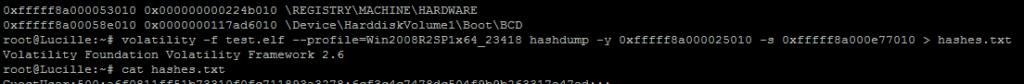
0xfffff8a001d4e010 0x00000000d1d08010 \??\C:\System Volume Information\Syscache.hve
0xfffff8a004314410 0x0000000116368410 \SystemRoot\System32\Config\DEFAULT
0xfffff8a008d69010 0x000000009ec82010 \??\C:\Windows\System32\config\COMPONENTS
0xfffff8a00000f010 0x0000000115010010 [no name]
0xfffff8a000025010 0x000000011501c010 \REGISTRY\MACHINE\SYSTEM
0xfffff8a000053010 0x000000000224b010 \REGISTRY\MACHINE\HARDWARE
0xfffff8a00058e010 0x0000000117ad6010 \Device\HarddiskVolume1\Boot\BCD
3. Extract the hashes
Now, with the virtual offset of SYSTEM and SAM, we can extract the hashes:
root@Lucille:~# volatility -f test.elf --profile=Win2008R2SP1x64_23418 hashdump -y 0xfffff8a000025010 -s 0xfffff8a000e77010 > hashes.txt
Volatility Foundation Volatility Framework 2.6
root@Lucille:~# cat hashes.txt
GuestUser:500:a6f0811ff51b73310f0fc711893a3278:5f4dcc3b5aa765d61d8327deb882cf99:::
Administrator:501:aad3b435b51404eeaad3b435b51404ee:297abf4cd76aabcb1e1155bac050671e:::
sshd:1005:aad3b435b51404eeaad3b435b51404ee:d7d95a53fca45b1ce8e3f51d880d27f1:::
4. Crack the hashes
Finally, we can process the hash using a local tool (like HashCat) or using a online tool like HashKiller:
[caption id="attachment_1902" align="alignnone" width="1024"]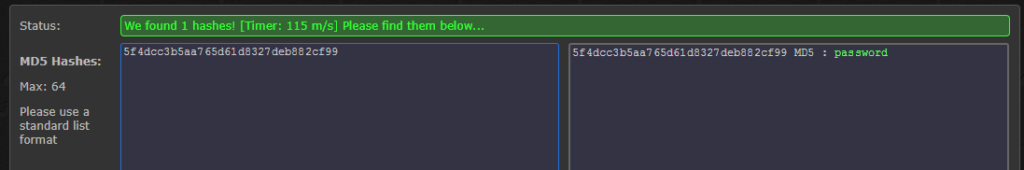 Yep, GuestUser uses a really strong password![/caption]
Yep, GuestUser uses a really strong password![/caption]