Windows PE run-time encryption with Hyperion
Hyperion is a crypter for PE files, developed and presented by Christian Amman in 2012.
The tool is a runtime crypter that can transform a Windows portable executables (PE) into an encrypted version that decrypts itself on startup and executes it’s original content.
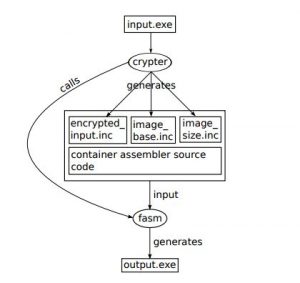
This approach provides a protection of binaries against reverse engineering but is really useful for security experts: : it allows the deployment of malicious executables in protected environments when pattern based anti virus solution detects the signature of suspicious files and blocks their execution.
The encrypted counterpart contains an unknown signature, it’s content can not be analysed by heuristics and is therefore executed normally without an intervention by the AV scanner.
The project has been presented in an interesting paper by Christian Amman in 2012, but this technique still has great margins for development:
Some important aspects are still missing in the Hyperion implementation: .NET executables are not yet supported and the code of the container has to be refactored to make it fool AV heuristics.
Furthermore, concepts like late API binding are missing.
The most important part which still has to be implemented is polymorphism: The current implementation of Hyperion just encrypts the input file. It is a worthwhile goal to encrypt the complete container and generate a small decrypter stub using polymorphism.
Bonus content
In this video you can see a brief tutorial of an antivirus evasion technique using using MSFVENOM, Hyperion and PEScrambler:
https://www.youtube.com/watch?v=FgVWHr19lI4
References
- http://www.ammann.technology/hyperion.html
- https://github.com/nullsecuritynet/tools/tree/master/binary/hyperion
- https://github.com/nullsecuritynet/papers/raw/master/nullsec-pe-crypter/nullsec-pe-crypter.pdf