Volatility tips: how to extract text typed in a notepad window from a Windows memory dump
In a comment on my article Volatility, my own cheatsheet (Part 3): Process Memory, Fabrizio asked me:
[...] da un dump di memoria su un sistema win7, ho rilevato che era in esecuzione notepad, è possibile visualizzarne il contenuto?
([...] from a memory dump on a win7 system, I found out that notepad was running, can I view its contents?)
Fabrizio has already tryed to use the volatility's notepad plugin, but is not supported by memory profile of the image.
In this case, i suggest to dump the memory of notepad.exe process and search the text using strings command.
So, let's try to simulate the process.
I've started a Windows 7 virtual machine on Virtualbox, and on this VM i've opened the notepad and written some text:
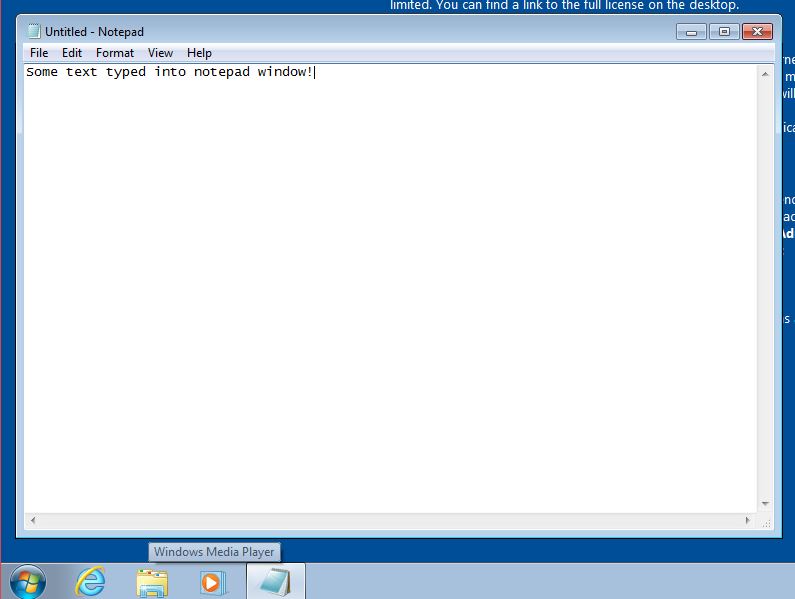
With VM still in running state, i've dumped and converted VM memory, using this procedure.
Once the memory dump is ready, we can try to extract the text.
First, identify the correct memory profile:
# volatility -f ./test.raw imageinfo Volatility Foundation Volatility Framework 2.6 INFO : volatility.debug : Determining profile based on KDBG search... Suggested Profile(s) : Win7SP1x86_23418, Win7SP0x86, Win7SP1x86 AS Layer1 : IA32PagedMemoryPae (Kernel AS) AS Layer2 : FileAddressSpace (/root/tmp/test.raw) PAE type : PAE DTB : 0x185000L KDBG : 0x82963c30L Number of Processors : 1 Image Type (Service Pack) : 1 KPCR for CPU 0 : 0x82964c00L KUSER_SHARED_DATA : 0xffdf0000L Image date and time : 2018-03-01 14:02:51 UTC+0000 Image local date and time : 2018-03-01 06:02:51 -0800
Then search the notepad.exe process
# volatility -f test.raw --profile=Win7SP1x86_23418 pslist | grep notepad Volatility Foundation Volatility Framework 2.6 0x85872b18 notepad.exe 2796 2168 5 81 1 0 2018-03-01 14:01:51 UTC+0000
...and dump the process memory:
# volatility -f test.raw --profile=Win7SP1x86_23418 memdump --dump-dir=./ -p 2796 Volatility Foundation Volatility Framework 2.6 ************************************************************************ Writing notepad.exe [ 2796] to 2796.dmp
Finally perform a strings search in the dump, using a word of the text as key:
# strings -e l ./2796.dmp | grep "Some" Some text typed into notepad window!
the "-e l" switch is needed because notepad stores text in 16-bit little-endian:
-e --encoding={s,S,b,l,B,L} Select character size and endianness:
s = 7-bit, S = 8-bit, {b,l} = 16-bit, {B,L} = 32-bit
If the text is composed by more than one line, is useful to specify a range for the grep search, for example 10 lines after and before:
# strings -e l ./2796.dmp | grep "Some" -B 10 -A 10 *:\Windows\system32\sppuinotify.dll Lucida Console ,indows\system32 dows\system32\sppsvc.exe RpcSs/ NT AUTHORITY\NetworkService Software Protection Notification Service efrag C:\Windows\system32 Some text typed into notepad window! Info Trans *8*8* ncalrpc spoolss ncalrpc ncacn_ip_tcp spoolss O8O8O ! #!%"'#)$+%-&/'1(3)5*7+9,;-=.?/A0E1I2M3Q4U5Y6]7a8e9i:m;q<u=y>}?
Obviously, you need to know at least one word that may have been written into the notepad window, otherwise you need to review the entire strings dump in order to find a readable text!
Thats all!