Blockchain and Cybersecurity: evolving security technologies
What does blockchain technology have to do with cybersecurity?
Blockchain technology seems to be a Columbus' egg: it may removes error and fraud, it can track ownership, managing identities and is resilient to cyber attacks.
Let's take a look at what blockchain is and how it relates to cybersecurity.
What is a blockchain?
A blockchain is a growing list of records, called blocks, which are linked using cryptography.
Each block contains a cryptographic hash of the previous block, a timestamp, and transaction data.
Blockchain technology has been around for just under a decade, initially introduced as a way to store and/or send the first cryptocurrency, Bitcoin.
However, as the technology has gradually spread worldwide, people have begun using it in a variety of ways in numerous industries, including as a means to increase cybersecurity.
How blockchain works?
Blockchain is typically managed by a peer-to-peer network collectively adhering to a protocol for inter-node communication and validating new blocks.
[caption id="attachment_3626" align="alignnone" width="1024"]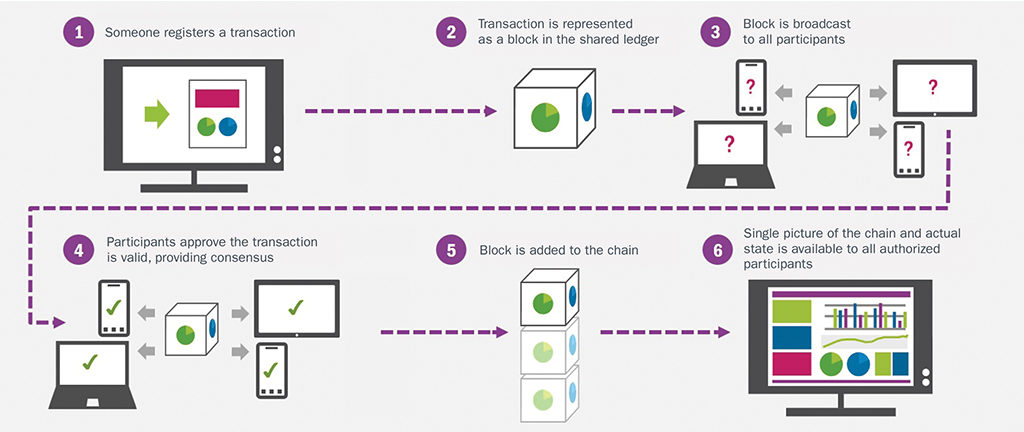 Source: https://www.mro-network.com/big-data/blockchain-mro-could-happen-sooner-you-think[/caption]
Source: https://www.mro-network.com/big-data/blockchain-mro-could-happen-sooner-you-think[/caption]
- Every user can add information to the blockchain and all data in the blockchain is secured through cryptography.
- Every other member of the network is responsible for verifying that the data being added to the blockchain is real.
This is done using a system of three keys (private, public, and the receiver’s key) that allow members to check the veracity of the data while also confirming who it comes from.
https://www.youtube.com/watch?v=SSo_EIwHSd4
A verified piece of data forms a block which then has to be added to the chain.
To do this, blockchain users have to use their respective keys and CPU time to run algorithms that solve a mathematical problems in order to validate the block. When a problem is solved, the block is added to the chain and the data it contains exists on the network forever, meaning that it cannot be altered or removed.
Why blockchain is so secure?
Another important thing to note about blockchain users is that they are able to store all of the data in their network on their computer, if they want to: every user on the network plays a part in storing some or all of the blockchain.
This results that the chain will not collapse: blockchain technology is designed in such a way that there is no central authority or storage location.
If, for instance, someone who is not the owner of a piece of data tries to tamper with a block, the whole system analyzes every single block of data to find the one that differs from the rest.
If the system finds this type of block, it simply excludes it from the chain, identifying it as false.
Alternative uses of blockchain
Blockchain technologies are, after all, the culmination of decades of research and breakthroughs in cryptography and security, that offers a totally different approach to storing informationa and establishing trust, which makes it especially suitable for environments with high security requirements and mutually unknown actors.
Thus, while cryptocurrencies like Bitcoin sometimes experience fluctuations in value, its blockchain have so far successfully withstood cyber-attacks for more than 8 years, and evolved in a modular structure that can also hosting a small logic, like Smart Contracts.
Blockchain Smart Contracts
A smart contract is similar to a contract in the physical world, but it’s digital and is represented by a tiny computer program stored inside a blockchain that stores rules for negotiating the terms of an agreement, automatically verifies fulfillment, and then executes the agreed terms.
[caption id="attachment_3627" align="alignnone" width="946"]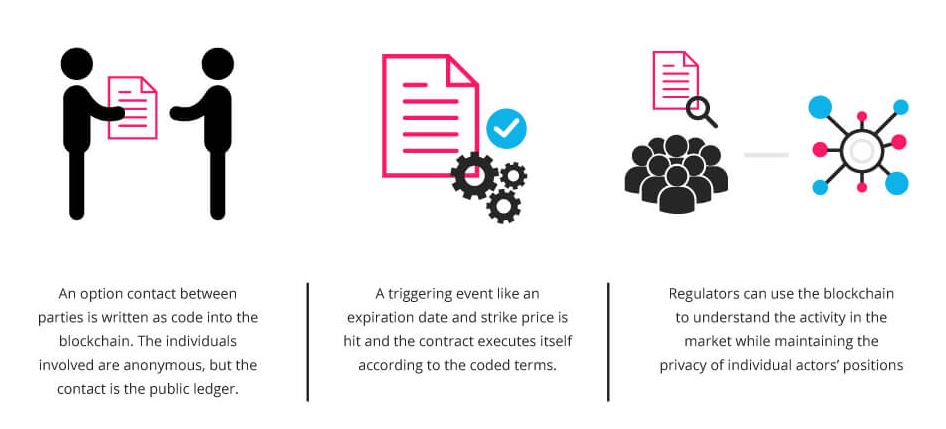 Source: https://blockgeeks.com/guides/smart-contracts/[/caption]
Source: https://blockgeeks.com/guides/smart-contracts/[/caption]
https://www.youtube.com/watch?v=ZE2HxTmxfrI
Use cases can be found in banking, insurance, energy, e-government, telecommunication, music & film industry, art world, mobility, education and many more. Smart contract use cases range from simple to complex.
From BlockchainHub:
Time-stamping services like ascribe (art registry) or governmental and semi-governmental registries (land titles, birth certificates, birth certificates, school and university degrees) are examples for simpler technological use cases (the regulatory aspects might be more complex). Decentralized autonomous organizations, on the other hand, are the most complex form of a smart contract.
[caption id="attachment_3634" align="alignnone" width="1437"]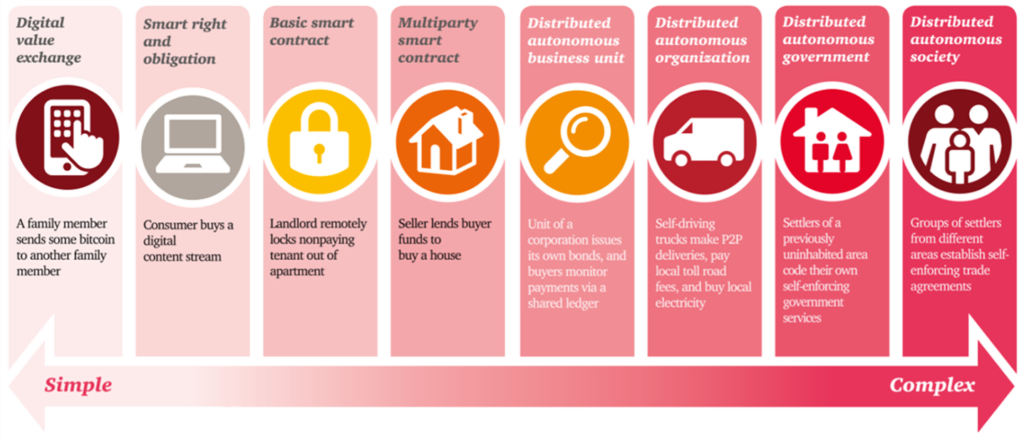 Source: https://blockchainhub.net/smart-contracts/[/caption]
Source: https://blockchainhub.net/smart-contracts/[/caption]
Using blockchain for data protection

Blockchain technology provides one of the best tools we currently have to decreasing the chance of data being stolen or compromised.
In order to destroy or corrupt a blockchain, an attacker would have to destroy the data stored on every user’s computer in the global network.
This could be millions of computers, with each one storing a copy of some or all the data.
Unless the malicious user could simultaneously bring down an entire network (which is near impossible), undamaged computers would continue running to verify and keep record of all the data on the network.
The impossibility taking down a whole chain increases along with the amount of users on a network. Bigger blockchain networks with more users have an infinitely lower risk of getting attacked by hackers because of the complexity required to penetrate such a network.
 Guardtime, founded by Estonian cryptographer Ahto Buldas in 2007, has already become successful in using blockchain technology to keep important data safe.
Guardtime, founded by Estonian cryptographer Ahto Buldas in 2007, has already become successful in using blockchain technology to keep important data safe.
The company uses blockchain to create a Keyless Signature Infrastructure (KSI), a replacement for the more traditional Public Key Infrastructure (PKI), which uses asymmetric encryption and a cache of public keys maintained by a centralized Certificate Authority (CA).
If someone tries to alter the data, the system analyses the whole mass of chains, compares them to the metadata packet and then excludes any that don’t match up.
This means that the only way to wipe the entire blockchain out is to destroy every single separate node. If just one node remains running with the correct data, the whole system can be restored, even if all of the other nodes are compromised.
Using blockchain for Identity Management
Traditional centralized Identity Management Systems suffers of many structural vulnerabilities: storing sensitive data of individuals in a particular location or server makes storage platform a target for identity thieves, and there is also the risk of loss of identity in the case of a system crash.
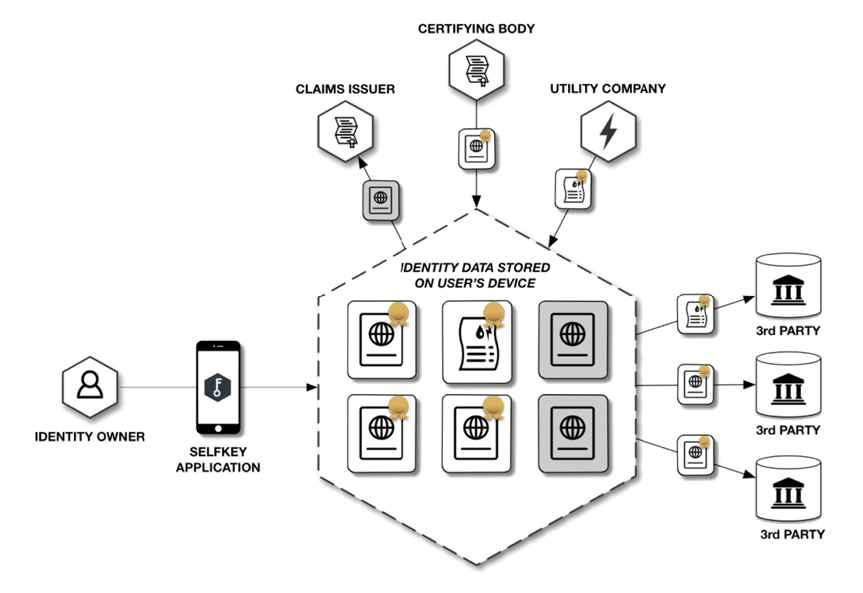
A blockchain can be used as the shared ledger that stores identity transactions, allowing users to create a self-sovereign identity.
A self-sovereign identity is fully controlled and maintained personally by the individual.
It becomes difficult to steal such an identity from an individual, and this handles the issue of identity theft that is common on the traditional identity management system.
A distributed decentralized ledger such as SelfKey would serve to eliminate the hitches of traditional identity management putting users at the centre of the identity management process, and enabling an Identity Ecosystem where users can transfer value among the Participants using a token: “KEY”.
The SelfKey token, “KEY” is a cryptocurrency,an ERC-20 token which can be freely traded.
https://www.youtube.com/watch?v=OndrivAxUwo
User’s KEY and identity documents can be stored in their identity wallet, from which they can pay to apply for services (such as a coin exchange account, a new company, or a bank account).
Using blockchain for a more secure Domain Name System
Implementing DNS on blockchain technology could fully decentralize the service, distributing the contents to a large number of nodes and making it nearly impossible for hackers to attack:
Since the data would be stored on many different nodes and every other user on the network would have a copy of the entire data on the blockchain, it would be virtually impossible to compromise it completely.
Domain editing rights would only be granted to those who need them (domain owners) and no other user could make changes, significantly reducing the risk of data being accessed or changed by unauthorized parties.

For instance, Blockstack provides a fully decentralized option for DNS, but the concept behind the company is to make the entire worldwide web decentralized by removing all third parties from managing web servers, ID systems, and databases.
https://www.youtube.com/watch?v=7SmC7AuZNWY
Using blockchain for decentralized services
MaidSafe is a company based in the UK.
The main goal of its project Safe Network is also to decentralize the web and create an alternative Internet where users are able to run apps, store data, and do everything else they normally do online, but in a more secure environment.
https://www.youtube.com/watch?v=RdGH40oUVDY
When joining to the SafeNetwork, users can choose how much of their personal storage space they want to dedicate for storing the distributed network data: every file placed onto the MaidSafe network is encrypted, fragmented, and shared among users.
The only person that can make the data readable again is its owner, ensuring that the data is not accessible by anyone other than the authorized owner.
Using blockchain in telcos for roaming fraud prevention
Roaming fraud can occur when an individual seeks to actively avoid payment for use of roaming services.
[caption id="attachment_3628" align="alignnone" width="772"]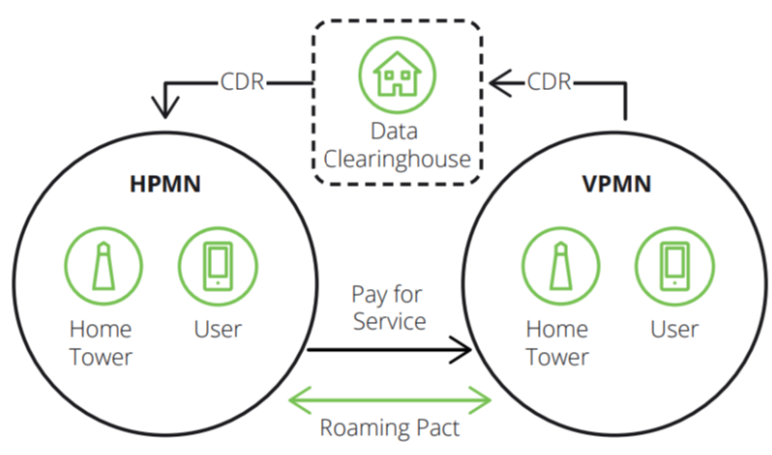 Source: Disruptive Analisys[/caption]
Source: Disruptive Analisys[/caption]
It is made possible because of the delay in time between an individual accessing a mobile network while roaming (referred to as Visited Public Mobile Network or VPMN) and that network being able to pass along the data necessary for the subscribers' home telco provider (referred to as the Host Mobile Public Network or HPMN) to bill the subscriber the relevant roaming charge.
The fraud can be mitigated by establishing a permissioned blockchain by the relevant HPMNs and VPMN partied to a smart contract-enabled roaming agreement.
[caption id="attachment_3629" align="alignnone" width="631"]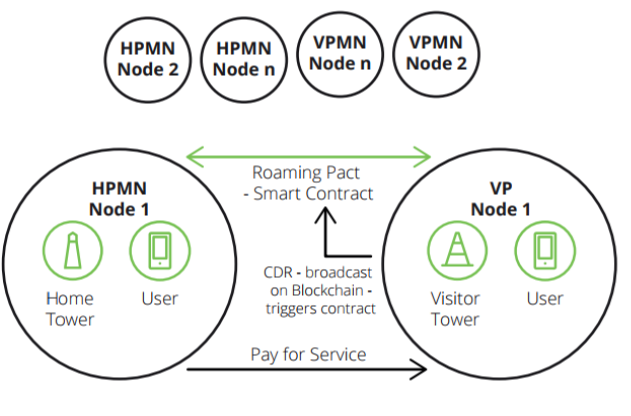 Source: Disruptive Analisys[/caption]
Source: Disruptive Analisys[/caption]
Every time an individual accesses a VPMN, a smart contract could be executed to automatically send the relevant data to the HPMN, allowing it to calculate and immediately charge (and ideally deduct) the relevant amount, which can then be transferred back to the VPMN.
Recently, IBM has published on GitHub a proof-of-concept of this process:
This is a proof of concept to demonstrate how Blockchain brings the CSPs on single Blockchain Hyperledger network which enables direct exchange of information with transactions that are immutable and executed based on consensus model using smart contract rules.
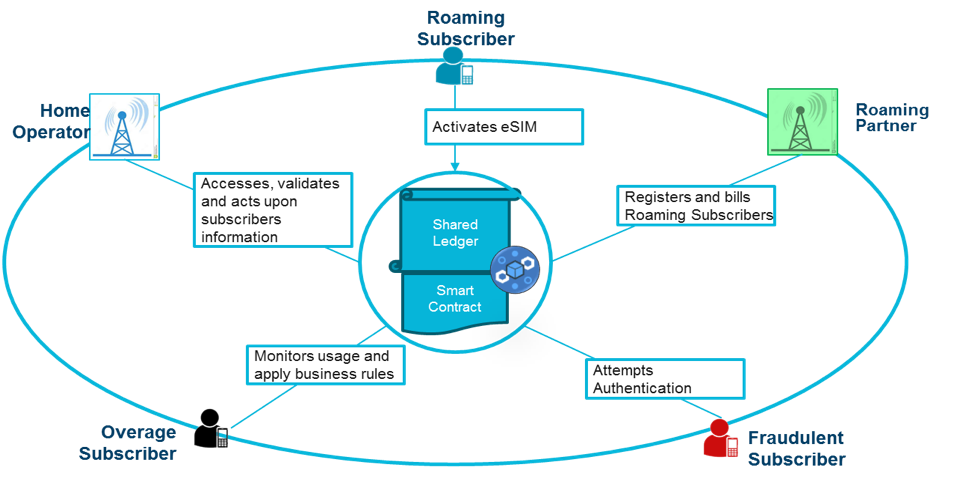
https://www.youtube.com/watch?v=enGDBnOFV60
Further readings and references
- Smart Contracts
- 3 Ways Blockchain Is Revolutionizing Cybersecurity
- How A Leading Cyber Security Company Uses Blockchain Technology To Prevent Data Tampering
- Blockchain In MRO Could Happen Sooner Than You Think
- Smart Contracts: The Blockchain Technology That Will Replace Lawyers
- Guardtime
- How Blockchain Can Solve Identity Management Problems
- The promise of managing identity on the blockchain - Techcrunch
- Using Blockchain Technology to Solve Identity Management Problems
- Blockchain For Telco Roaming