My Weekly RoundUp #75
After some months of rest, i've decided to star again publishing of my Weekly RoundUp. Why?
That’s simple: i also started a process of Social Media Detox, that involve deactivation of my Social Network accounts. Without them, i don’t have any way to share with my followers interesting links that i’ve read in the week.
So let’s start: there are a lot of news!
Cybersecurity
Huawei employee arrested, accused of “high-level espionage” for China

A Huawei employee was arrested in Poland on Tuesday and charged with spying for China, according to numerous media reports.
"Polish authorities detained and charged a local sales director of Huawei Technologies Co., a Chinese national, with conducting high-level espionage on behalf of China," The Wall Street Journal wrote today.
Huawei is a large maker of smartphones and telecommunications equipment.
Poland also arrested a Polish man "who [formerly] held several top government cybersecurity positions," the Associated Press reported.Huawei employee arrested, accused of “high-level espionage” for China | Ars Technica
Huawei has reportedly fired Wang Weijing, an employee recently arrested in Poland on espionage charges. According to Reuters, Huawei made the sacking because it wanted to distance itself from the incident. This is not the first time a Huawei employee has been arrested, last month the founder’s daughter, Meng Wanzhou was arrested in Canada for breaking sanctions on Iran.
Huawei fires executive recently charged with espionage in Poland - Neowin
Malwarebytes users complain about freezing Windows 7 computers after update
An issue with the latest version of antivirus software Malwarebytes causes computers running Windows 7 to freeze and lock-up. When the computer is frozen due to the issue, the only solution is to perform a hard reboot. So far, Malwarebytes has not been able to find the root of the issue.
Malwarebytes users complain about freezing Windows 7 computers after update - Myce.com
Technology
Autonomous robot struck and killed by a self-driving Tesla in Las Vegas
In what many are speculating was an over-the-top PR stunt, Promobot revealed one of its model v4 robots was ‘killed’ by a Tesla Model S on a Las Vegas street ahead of CES.
The accident occurred on Paradise Rd Sunday night as engineers transported the firm’s robots to the display booth.
Autonomous robot struck and killed by a self-driving Tesla in Las Vegas | Daily Mail Online
DFIR
Investigate and fight cyberattacks with SIFT Workstation
The SIFT Workstation was developed by an international team of forensics experts, including entrepreneur, consultant and SANS Fellow Rob Lee, and is available to the digital forensics and incident response community as a public service. Just because it's freely available and originally designed for training, though, doesn't mean it can't stand up to field investigations. The SIFT Workstation incorporates powerful, cutting-edge open-source tools that are frequently updated, vetted by the open source community and able to match any modern DFIR tool suite. Don't just take our word for it.
Privacy
Facebook Is a Social Menace

Facebook sells the names of its users’ “friends” without consent and allows certain corporations to read and delete private messages. It also sells the names and contact information of users and then lies about it; permits the companies that purchase its data to conceal this fact; and allows these same companies to ignore the preferences of people who disable their sharing settings.
Meanwhile, another investigation, this one by Privacy International, found that Facebook “routinely tracks users, non-users and logged-out users outside its platform through Facebook Business Tools.” In other words, Facebook spies on people who don’t even use Facebook.
Roomba's Next Big Step Is Selling Maps of Your Home to the Highest Bidder

The Roomba is generally regarded as a cute little robot friend that no one but dogs would consider to be a potential menace. But for the last couple of years, the robovacs have been quietly mapping homes to maximize efficiency. Now, the device’s makers plan to sell that data to smart home device manufacturers, turning the friendly robot into a creeping, creepy little spy.
Roomba's Next Big Step Is Selling Maps of Your Home to the Highest Bidder
Corporate Surveillance in Everyday Life
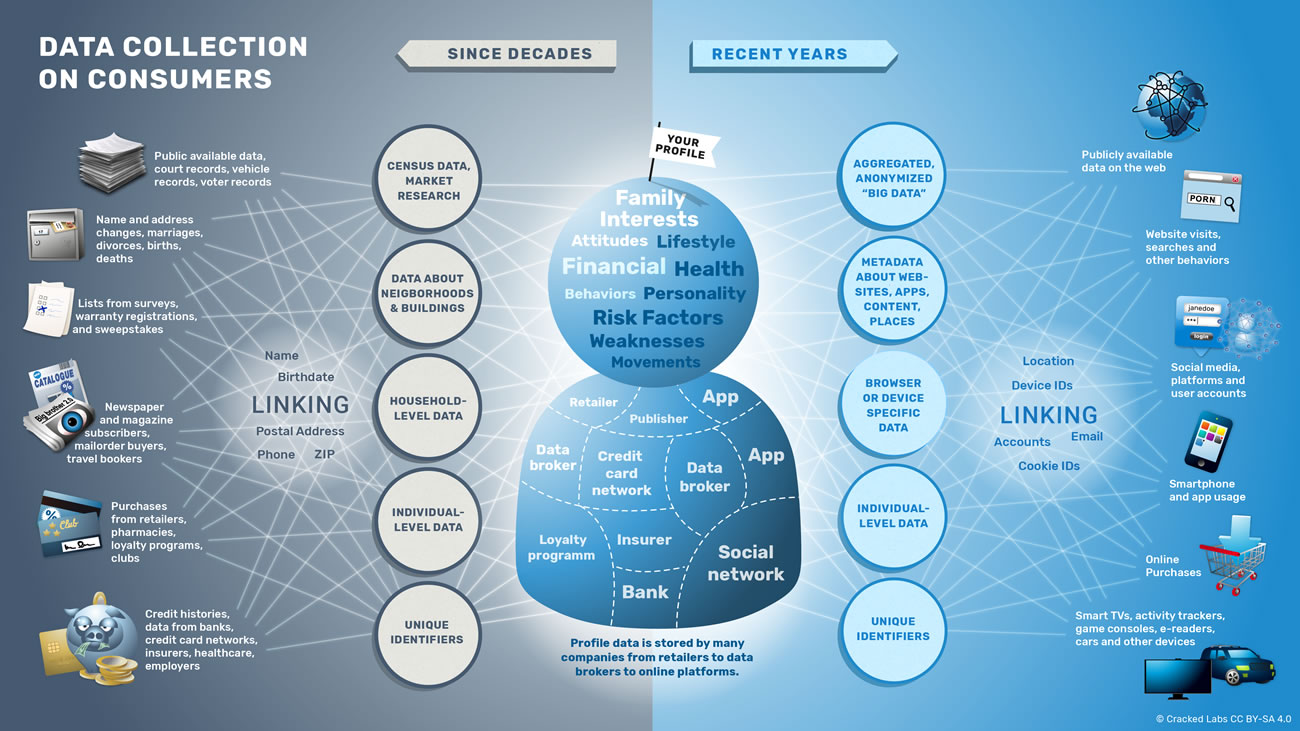
How thousands of companies monitor, analyze, and influence the lives of billions. Who are the main players in today’s digital tracking? What can they infer from our purchases, phone calls, web searches, and Facebook likes? How do online platforms, tech companies, and data brokers collect, trade, and make use of personal data?
Malware Analysis
Out of sight but not invisible: Defeating fileless malware with behavior monitoring, AMSI, and next-gen AV
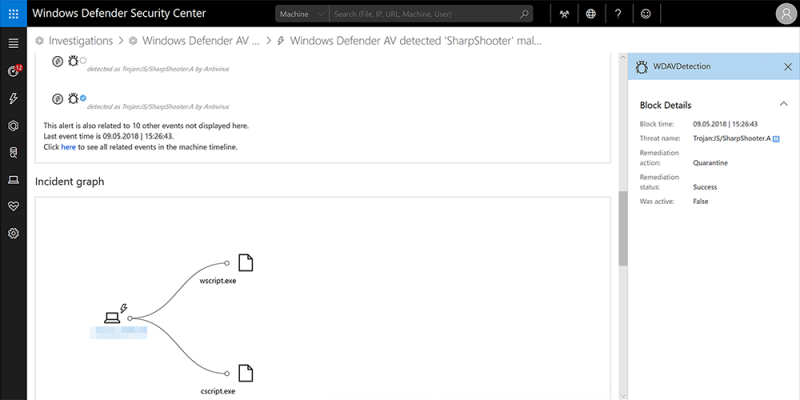
Consider this scenario: Two never-before-seen, heavily obfuscated scripts manage to slip past file-based detection and dynamically load an info-stealing payload into memory. The scripts are part of a social engineering campaign that tricks potential victims into running the scripts, which use the file names install_flash_player.js and BME040429CB0_1446_FAC_20130812.XML.PDF.js, to distribute and run the payload.
NSA to release its GHIDRA reverse engineering tool for free
reverse engineering tool for free at the upcoming RSA security conference 2019 that will be held in March in San Francisco.
The existence of the framework, dubbed GHIDRA, was first publicly revealed by WikiLeaks in CIA Vault 7 leaks, but the tool once again came to light after Senior NSA Adviser Robert Joyce announced to publicly release the tool for free in his RSA Conference session description.GHIDRA is a Java-based reverse engineering framework that features a graphical user interface (GUI) and has been designed to run on a variety of platforms including Windows, macOS, and Linux operating systems, and also supports a variety of processor instruction sets.
The toolkit can also be used to analyze binary files used by programs, including malware, for all major operating systems, including Windows, macOS, Linux as well as mobile platforms such as Android and iOS.NSA to release its GHIDRA reverse engineering tool for free – PentestTools
Software
Rapid7 announced the release of Metasploit 5.0 framework
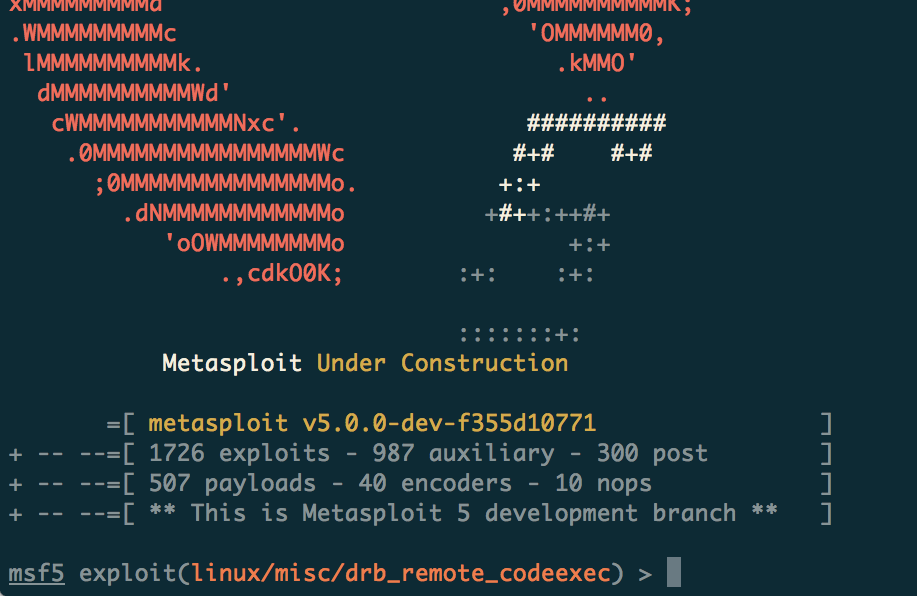
Rapid7 announced the release of Metasploit 5.0, the new version includes several new important features and, the company believes it will easier to use and more powerful.
Most important changes introduced in the Metasploit 5.0 include new database and automation APIs, evasion modules and libraries, language support, improved performance.
In order to allow for multiple Metasploit consoles and external tools to interact with the framework, the latest version can now run the PostgreSQL database by itself as a RESTful serviceRapid7 announced the release of Metasploit 5.0 framework - Security Affairs
Pylocky Unlocked: Cisco Talos releases PyLocky ransomware decryptor
PyLocky is a family of ransomware written in Python that attempts to masquerade as a Locky variant. This ransomware will encrypt all files on a victim machine before demanding that the user pay a ransom to gain access to their decrypted files. To combat this ransomware, Cisco Talos is releasing a free decryption tool.
Programming
Etsy’s experiment with immutable documentation

Writing documentation is like trying to hit a moving target. The way a system works changes constantly, so as soon as you write a piece of documentation for it, it starts to get stale. And the systems that need docs the most are the ones being actively used and worked on, which are changing the fastest. So the most important docs go stale the fastest! 1
Etsy has been experimenting with a radical new approach: immutable documentation.Etsy’s experiment with immutable documentation - Code as Craft
Music
Segovia Sunday Returns! Watch the Maestro Play Two Renaissance Lute Pieces!
Segovia Sunday Returns! Watch the Maestro Play Two Renaissance Lute Pieces! – Classical Guitar