My Weekly RoundUp #84
A bad week for Citrix, Hard Disks used as microphone and some news from Marvel.
Enjoy!
Cybersecurity
Encrypted Messaging Apps Facilitating Cybercrime in Latin America
As Spanish- and Portuguese-speaking markets continue to drop off the Deep & Dark Web (DDW), criminals are migrating more and more to encrypted chat-services platforms for communication and commerce.
Markets operating in either language have been scarce and have been shutting down due to poor sales and/or management. Buyers and sellers who bypassed markets and used underground forums to meet, were finalizing negotiations or communicating directly instead over encrypted platforms.
While this is a stark contrast to operators in Eastern Europe and North America who still heavily trade on the DDW, criminals in Latin America prefer the convenience and relatively high levels of baseline security found in encrypted chat apps. Some of this is due to a relative lack of technological sophistication within the region.
Citrix Data Breach – Iranian Hackers Stole 6TB of Sensitive Data

Popular enterprise software company Citrix that provides services to the U.S. military, the FBI, many U.S. corporations, and various U.S. government agencies disclosed last weekend a massive data breach of its internal network by "international cyber criminals."
Citrix said it was warned by the FBI on Wednesday of foreign hackers compromising its IT systems and stealing "business documents," adding that the company does not know precisely which documents the hackers obtained nor how they got in.
However, the FBI believes that the miscreants likely used a "password spraying" attack where the attackers guessed weak passwords to gain an early foothold in the company's network in order to launch more extensive attacks.
Citrix admits attackers breached its network – what we know
On Friday, software giant Citrix issued a short statement admitting that hackers recently managed to get inside its internal network.
According to a statement by chief information security officer Stan Black, the company was told of the attack by the FBI on 6 March, since when it had established that attackers had taken “business documents” during the incident:
The specific documents that may have been accessed, however, are currently unknown. At this time, there is no indication that the security of any Citrix product or service was compromised.No mention of when the attackers gained access, nor how long that had lasted. As to how they got into the network of a company estimated to manage the VPN access of 400,000 large global organisations:
While not confirmed, the FBI has advised that the hackers likely used a tactic known as password spraying, a technique that exploits weak passwords. Once they gained a foothold with limited access, they worked to circumvent additional layers of security.
Uncommon Radixes Used in Malware Obfuscation
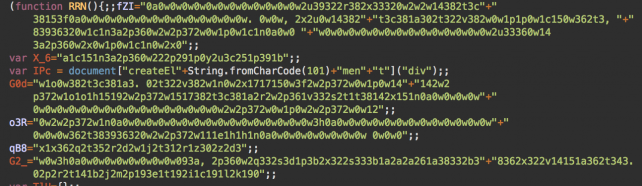
Bad actors routinely leverage obfuscation to hide malicious indicators and prevent removal or analysis — even the most common malware can evade detection if it has been craftily obfuscated in an unexpected way.
Every now and then, we discover gems like this one. These clever obfuscation techniques break up the monotony by showing how little known language features can be used in an unexpected way.https://blog.sucuri.net/2019/03/uncommon-radixes-used-in-malware-obfuscation.html
Technology
Linux 5.1 Continues The Years-Long Effort Preparing For Year 2038

The Linux kernel has been seeing "Y2038" work for years and the effort is far from over. Thomas Gleixner (a Linux kernel developer who serves as a member of the technical advisory board at The Linux Foundation) sent in the latest Y2038 work for the Linux 5.1 kernel, which after a lot of ground work in previous kernels has introduced the first set of syscalls that are Year 2038 safe.
The Year 2038 problem is where the Unix time can no longer be stored in a signed 32-bit integer and thus after 19 January 2038 will begin wrapping around as a negative number for representing the number of seconds since 1 January 1970.
https://www.phoronix.com/scan.php?page=news_item&px=Linux-5.1-Year-2038-Syscalls
Privacy
When Facial Recognition Is Used to Identify Defendants, They Have a Right to Obtain Information About the Algorithms Used on Them

EFF, ACLU, Georgetown Law’s Center on Privacy & Technology, and Innocence Project filed an amicus brief in support of the defendant’s petition for review in Willie Allen Lynch v. State of Florida. Prosecutors in the case didn’t disclose information about how the algorithm worked, that it produced other matches that were never considered, or why Lynch’s photo was targeted as the best match. This information qualifies as “Brady” material—evidence that might exonerate the defendant—and should have been turned over to Lynch.
We have written extensively about how facial recognition systems are prone to error and produce false positives, especially when the algorithms are used on African Americans, like the defendant in this case. Researchers at the FBI, MIT, and ProPublica have reported that facial recognition algorithms misidentify black people, young people, and women at higher rates that white people, the elderly, and men.
From hard drive to over-heard drive: Boffins convert spinning rust into eavesdropping mic
Eggheads at the University of Michigan in the US, and Zhejiang University in China, have found that hard disk drives (HDDs) can be turned into listening devices, using malicious firmware and signal processing calculations.
For a study titled "Hard Drive of Hearing: Disks that Eavesdrop with a Synthesized Microphone," computer scientists Andrew Kwong, Wenyuan Xu, and Kevin Fu describe an acoustic side-channel that can be accessed by measuring how sound waves make hard disk parts vibrate.[...]
The team's research work, scheduled to be presented in May at the 2019 IEEE Symposium on Security and Privacy, explores how it's possible to alter HDD firmware to measure the offset of a disk drive's read/write head from the center of the track it's seeking.
https://www.theregister.co.uk/2019/03/07/hard_drive_eavesdropping/
Programming
The force
DFIR
KAPE 0.8.3.0 released
v0.8.3.0
- Added %kapeDirectory% variable that is replaced with the full path to where kape.exe was executed from. Useful for having a reference point for config files to pass to modules, etc.
- Added SFTP support. Server name, port, and username are required. See help screen for more details and switches. SFTP password, when present, will be redacted from the ConsoleLog
- Added zip to container options. Works like VHD(x) containers, except things just get zipped up
- When targeting $J, only copy the non-sparse part of the file. This makes for a much smaller (and faster!) collection
- Added _kape.cli support. _kape.cli should contain one or more KAPE command lines (one per line). When KAPE sees this file on start up, it executes one copy of KAPE per line in the file, then renames _kape.cli by adding a timestamp to the front of the file. See https://twitter.com/EricRZimmerman/status/1104212779299426304 for more details and example usage
- Remove --toe option
- In modules, for ExportFile property, %fileName% will get replaced using the name of the file being processed. Example: ExportFile: TeraCopy-history_%fileName%.csvhttps://www.kroll.com/en/insights/publications/cyber/new-variables-and-sftp-support-in-kape
