My Weekly RoundUp #90
DockerHUB had some trouble…
Privacy
Alexa, stop being creepy! Our letter to Jeff Bezos
Dear Mr. Bezos,
We are writing to call for your urgent action regarding last week’s report[1] in Bloomberg, which revealed that Amazon has been employing thousands of workers to listen in on the recordings of Amazon Echo users.
Privacy International (PI) is a registered charity based in London that works at the intersection of modern technologies and rights. Privacy International challenges overreaching state and corporate surveillance, so that people everywhere can have greater security and freedom through greater personal privacy.https://privacyinternational.org/feature/2820/alexa-stop-being-creepy-our-letter-jeff-bezos
Zuck’s back, calling for “new rules” for the Internet, which will entrench Facebook’s power, but do nothing for privacy

Last month, Privacy News Online looked at a 3000-word essay entitled “A Privacy-Focused Vision for Social Networking“, written by Mark Zuckerberg. It’s a measure of the political pressure that Facebook finds itself under that Zuckerberg has published another big “thought piece”, where he is obviously trying to steer public discussions to his company’s advantage. This time, in a move that has surprised some, he wants “new rules” for the Internet
NSA reportedly recommends retiring phone surveillance program
The National Security Agency has recommended the White House abandon a controversial program that collects and analyzes data on millions of Americans' domestic calls and texts, The Wall Street Journal reported Wednesday.
The recommendation against renewing the program represents a dramatic reversal from the longstanding position of the agency, which had argued that the program was vital to identifying and disrupting terrorist activities.
The program, which was put in place after the 2001 terrorist attacks, has legal and logistical burdens that outweigh its value to national security, sources told the Journal.https://www.cnet.com/news/nsa-reportedly-recommends-retiring-phone-surveillance-program/
This colorful printed patch makes you pretty much invisible to AI
The rise of AI-powered surveillance is extremely worrying. The ability of governments to track and identify citizens en masse could spell an end to public anonymity. But as researchers have shown time and time again, there are ways to trick such systems.
The latest example comes from a group of engineers from the university of KU Leuven in Belgium. In a paper shared last week on the preprint server arXiv, these students show how simple printed patterns can fool an AI system that’s designed to recognize people in images.
Cybersecurity
Docker Hub Database Hack Exposes Sensitive Data of 190K Users
An unauthorized person gained access to a Docker Hub database that exposed sensitive information for approximately 190,000 users. This information included some usernames and hashed passwords, as well as tokens for GitHub and Bitbucket repositories.
According to a security notice sent late Friday night, Docker became aware of unauthorized access to a Docker Hub database on April 25th, 2019.
After performing an investigation it was determined that the database contained information for approximately 190,000 users. This information included access tokens for GitHub and Bitbucket repositories used for Docker autobuilds as well usernames and passwords for a small percentage of users.
Phone fingerprint scanner fooled by chewing gum packet

Nokia has had a bit of trouble with the fingerprint scanner on the 9, with false negatives being an annoying issue for some legitimate users.
That’s necessitated some reworking of the recognition system.
Generally speaking, re-tuning the system to bring false negatives down to a tolerable level involves a corresponding increase in false positives.
Indeed, this is what intuition suggests – the more easy-going you are about letting people in, the less strict you end up being about keeping others out.
And an imbalance in fingerprint recognition accuracy is what seems to have happened in the brief history of the Nokia 9.
An early reviewer who loved the cameras nevertheless complained that the device “has an in-display fingerprint reader that’s finicky”.https://nakedsecurity.sophos.com/2019/04/23/phone-fingerprint-scanner-fooled-by-chewing-gum-packet/
ExtraPulsar backdoor based on leaked NSA code – what you need to know
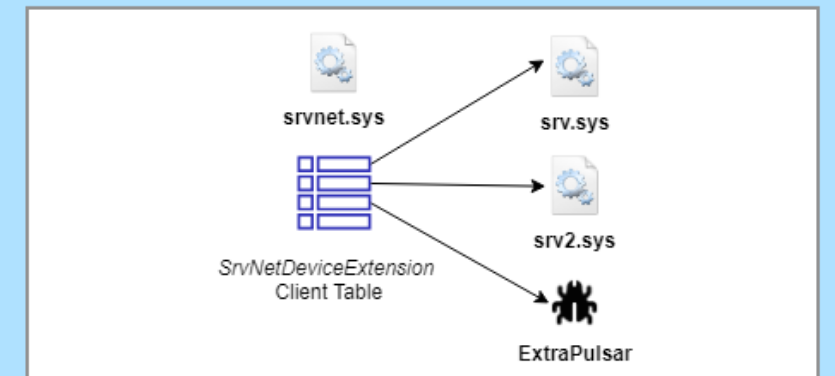
A US security researcher has come up with an open-source Windows backdoor that is loosely based on NSA attack code that leaked back in 2017 as part of the the infamous Shadow Brokers breach.
The researcher, who goes by@zerosum0x0online and Sean Dillon in real life, has dubbed his new malware ExtraPulsar, a nod to the NSA’s tool called DOUBLEPULSAR.
The code itself is intriguingly simple.
Rather than exploiting a vulnerability that wasn’t supposed to be there, it quietly makes use of an undocumented part of Microsoft’s own file server driverSRVNET.SYS.
Blochainbandit stole $54 million of Ethereum by guessing weak keys

Someone has been quietly pilfering Ethereum (ETH) cryptocurrency worth millions of dollars without anyone noticing or, apparently, caring.
The discovery was made by researchers at Independent Security Evaluators (ISE) who decided to search Ethereum’s blockchain for evidence of a surprisingly simple weakness that might allow criminals to divert funds from user wallets.
Wallets should be protected by a randomly-generated 256-bit private key, which puts the probability of their discovery at around 1 in 2256 - an unimaginably vast number.
Using a computer capable of generating 100 trillion keys per second, brute forcing such an address would take so long ISE researcher Adrian Bednarek compares it to tossing grain of sand on a beach and asking someone to find it.
That’s the theory of key generation. But the problem is how the principle appears to have been implemented by fallible software.
Programming
Creators of Python, Java, C#, and Perl discuss the evolution and future of programming language design at PuPPy
At the first annual charity event conducted by Puget Sound Programming Python (PuPPy) last Tuesday, four legendary language creators came together to discuss the past and future of language design. This event was organized to raise funds for Computer Science for All (CSforALL), an organization which aims to make CS an integral part of the educational experience.
Among the panelists were the creators of some of the most popular programming languages:
- Guido van Rossum, the creator of Python
- James Gosling, the founder, and lead designer behind the Java programming language
- Anders Hejlsberg, the original author of Turbo Pascal who has also worked on the development of C# and TypeScript
- Larry Wall, the creator of Perl
The discussion was moderated by Carol Willing, who is currently a Steering Council member and developer for Project Jupyter. She is also a member of the inaugural Python Steering Council, a Python Software Foundation Fellow and former Director.

