CVE-2019-9848: (un)patched flaw in LibreOffice allows malicious code execution
This vulnerability, discovered by Nils Emmerich, resides in LibreLogo, a programmable turtle vector graphics script that ships by default with LibreOffice, and still exists in the latest version has been patched in version 6.2.5.
LibreLogo allows users to specify pre-installed scripts in a document that can be executed on various events such as mouse-over: the flaw could allow an attacker to craft a malicious document that can silently execute arbitrary python commands without displaying any warning to a targeted user.
According to Emmerich analysis:
LibreOffice is shipped by default with LibreLogo, a macro to programmable move a turtle vector graphic. To move the turtle, LibreLogo executes custom script code that is internally translated to python code and executed. The big problem here is that the code in not translated well and just supplying python code as the script code often results in the same code after translation.
Using forms and OnFocus event, it is even possible to get code execution when the document is opened, without the need for a mouse-over event.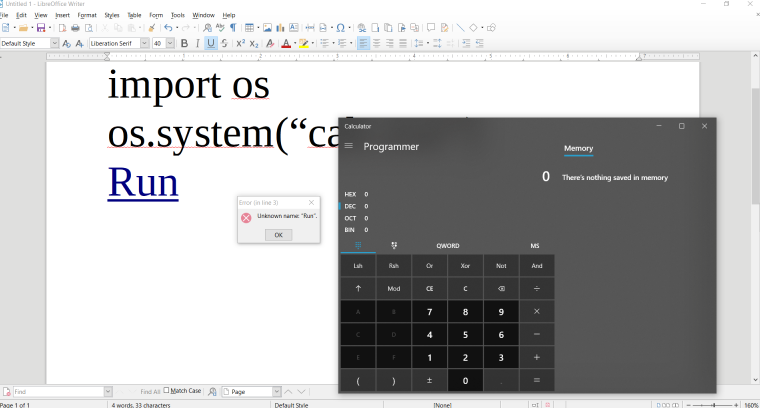
The researcher also released a proof-of-concept for this attack: https://insinuator.net/2019/07/libreoffice-a-python-interpreter-code-execution-vulnerability-cve-2019-9848/
How to protect your system?
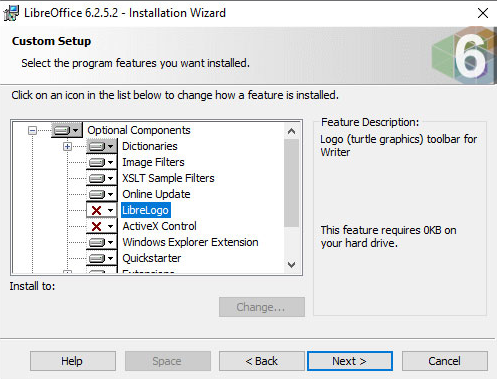
A patch is still unavailable but until the team releases an update has been released with version 6.2.5, but you also mitigate the flaw removing the LibreLogo component, by following this steps.
- Open the setup to start the installation
- Select "Custom" installation
- Expand "Optional Components"
- Click on "LibreLogo"
- Select "This Feature Will Not Be Available"
- Click Next and then Install/Update the software