Reverse engineering and penetration testing on iOS apps: my own list of tools
After a post focused on Android, another list of tools useful for penetration testing and reverse engineering of iOS applications.
Also all this tools are OSS and freely available.
Access Device
iProxy
Let's you connect your laptop to the iPhone to surf the web.
iProxy does not give you tethering - it just gives you the next best thing. A http and a socks proxy on your iPhone. Similar to the famous netshare app did before it got pulled from the App Store.
itunnel
Use to forward SSH via USB.
iFunbox

The File and App Management Tool for iPhone, iPad & iPod Touch.
Static Analysis
otool
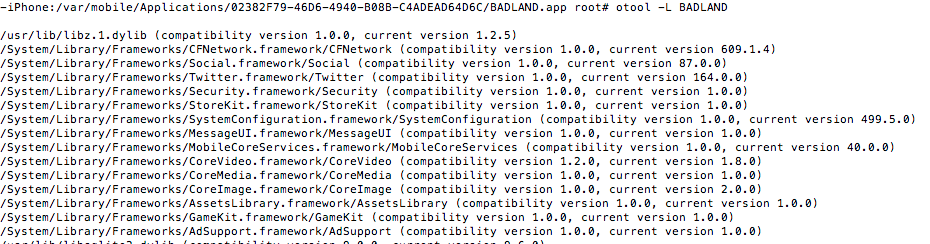
The otool command displays specified parts of object files or libraries.
Clutch
Clutch is a high-speed iOS decryption tool. Clutch supports the iPhone, iPod Touch, and iPad as well as all iOS version, architecture types, and most binaries.
Dumpdecrypted
Dumps decrypted mach-o files from encrypted iPhone applications from memory to disk. This tool is necessary for security researchers to be able to look under the hood of encryption.
class-dump
A command-line utility for examining the Objective-C runtime information stored in Mach-O files.
Weak Classdump
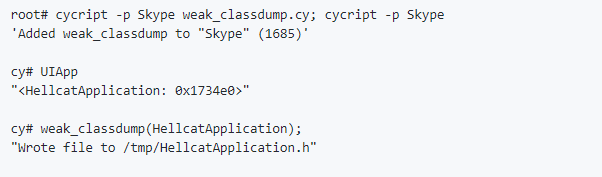
A Cycript script that generates a header file for the class passed to the function. Most useful when you cannot classdump or dumpdecrypted , when binaries are encrypted etc.
Fridpa

An automated wrapper script for patching iOS applications (IPA files) and work on non-jailbroken device.
bfinject
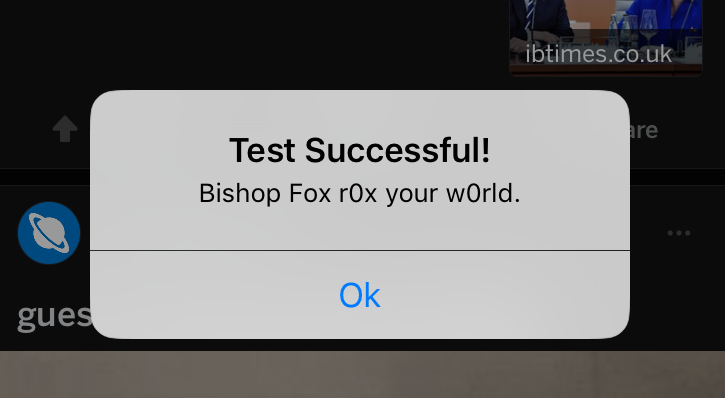
bfinject loads arbitrary dylibs into running App Store apps. It has built-in support for decrypting App Store apps, and comes bundled with iSpy and Cycript.
HopperApp
Hopper is a reverse engineering tool for OS X and Linux, that lets you disassemble, decompile and debug your 32/64bits Intel Mac, Linux, Windows and iOS executables.
Hopperscripts can be used to demangle the Swift function name in HopperApp.
Radare2
Radare2 is a unix-like reverse engineering framework and commandline tools.
iOS Reverse Engineering Toolkit (iRET)
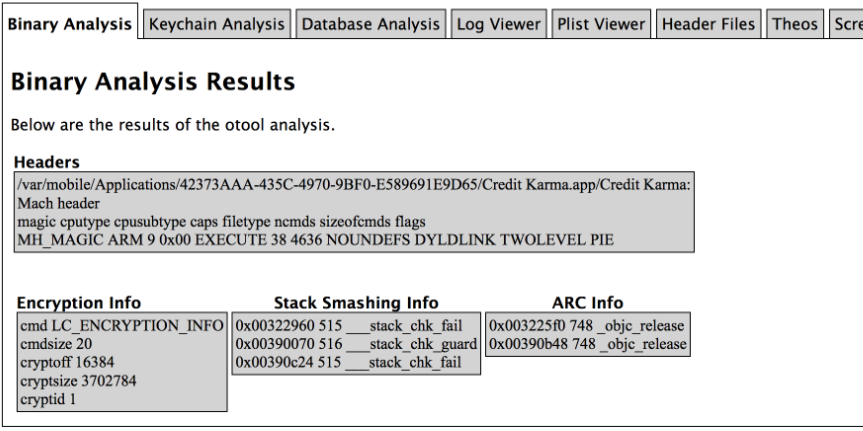
The iOS Reverse Engineering Toolkit is a toolkit designed to automate many of the common tasks associated with iOS penetration testing.
Dynamic Analysis
cycript
Cycript allows developers to explore and modify running applications on either iOS or Mac OS X using a hybrid of Objective-C++ and JavaScript syntax through an interactive console that features syntax highlighting and tab completion.
iNalyzer
AppSec Labs iNalyzer is a framework for manipulating iOS applications, tampering with parameters and method.
Passionfruit

Simple iOS app blackbox assessment tool with Fully web based GUI. Powered by frida.re and vuejs.
Introspy-iOS
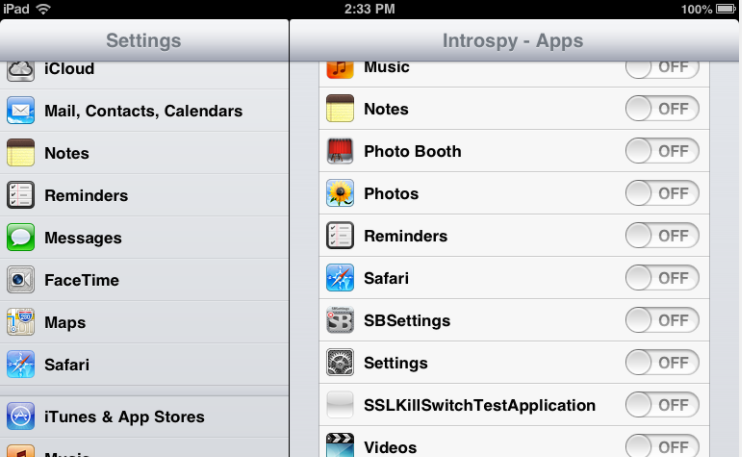
Blackbox tool to help understand what an iOS application is doing at runtime and assist in the identification of potential security issues.
Apple configurator 2
A utility which can be used to view live system log on iDevice.
keychaindumper
A tool to check which keychain items are available to an attacker once an iOS device has been jailbroken.
Network Analysis
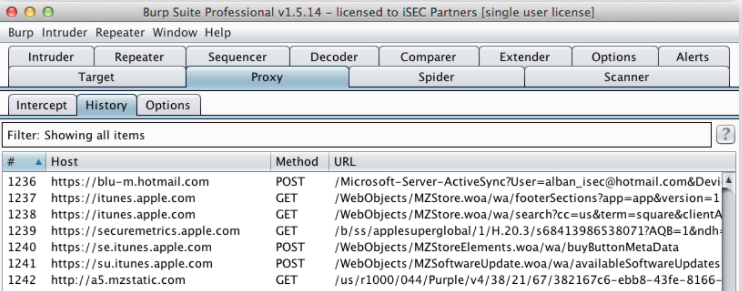
Burp Suite
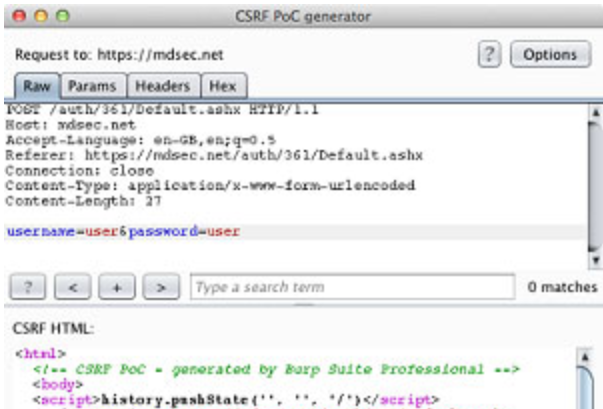
Burp Suite is an integrated platform for performing security testing of applications.
OWASP ZAP
OWASP Zed Attack Proxy Project is an open-source web application security scanner. It is intended to be used by both those new to application security as well as professional penetration testers.
Charles Proxy
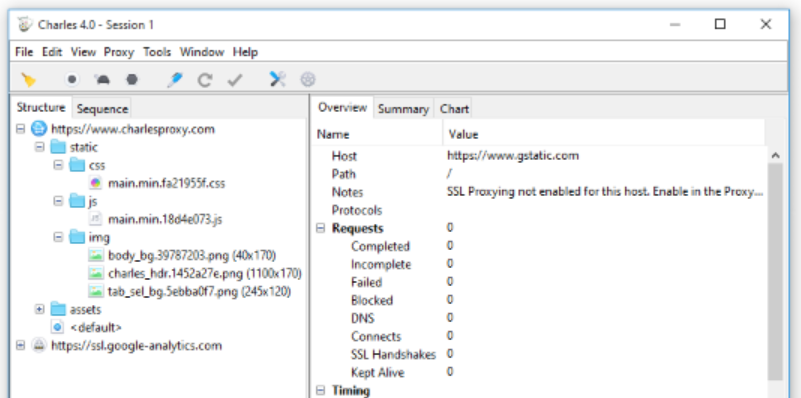
HTTP proxy / HTTP monitor / Reverse Proxy that enables a developer to view all of the HTTP and SSL / HTTPS traffic between their machine and the Internet.
Bypassing Jailbreak Detection and SSL Pinning
SSL Kill Switch 2
Blackbox tool to disable SSL certificate validation - including certificate pinning - within iOS and OS X Apps.
iOS TrustMe
Disable certificate trust checks on iOS devices.
The tool is patterned on ios-ssl-kill-switch: it uses a similar technique, but targets a C function that is lower in the call chain of most SSL certificate validation code, which allows it to disable more SSL validation code.
Xcon
A tool for bypassing Jailbreak detection.
tsProtector
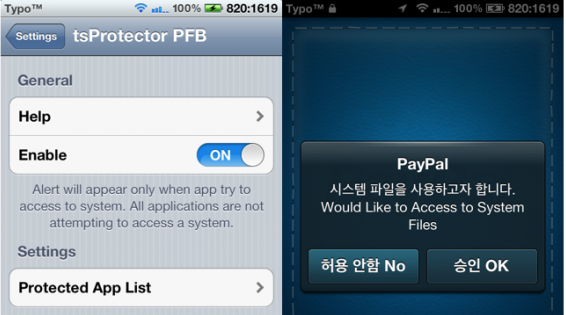
Another tool for bypassing Jailbreak detection.
Frida CodeShare

The Frida CodeShare project is comprised of developers from around the world working together with one goal - push Frida to its limits in new and innovative ways.
Security Libraries
OWASP iMAS
iMAS is a collaborative research project from the MITRE Corporation focused on open source iOS security controls.