Windows information gathering using Powershell: a brief cheatsheet
During a penetration test, once you get a local access to a target, you should start a local assessment of the machine in order to plan a correct tactic for privileges escalation and lateral movement.
So, today l'd like to share my own cheatsheet of useful powershell commands.
Basic System Information
Start-Process "systeminfo" -NoNewWindow -Wait;
Environment Variables
Get-ChildItem Env: | ft Key,Value;
Network Information
Get-NetIPConfiguration | ft InterfaceAlias,InterfaceDescription,IPv4Address;
DNS Servers
Get-DnsClientServerAddress -AddressFamily IPv4 | ft;
ARP cache
Useful for discover other assets suitable for lateral movement
Get-NetNeighbor -AddressFamily IPv4 | ft ifIndex,IPAddress,LinkLayerAddress,State;
Routing Table
Useful for understand routing and internet exposition of the target
Get-NetRoute -AddressFamily IPv4 | ft DestinationPrefix,NextHop,RouteMetric,ifIndex;
Network Connections
Start-Process "netstat" -ArgumentList "-ano" -NoNewWindow -Wait;
Connected Drives
Get-PSDrive | where {$_.Provider -like "Microsoft.PowerShell.Core\FileSystem"};
Firewall Config
Start-Process "netsh" -ArgumentList "firewall show config" -NoNewWindow -Wait
Current User
Write-Host $env:UserDomain\$env:UserName;
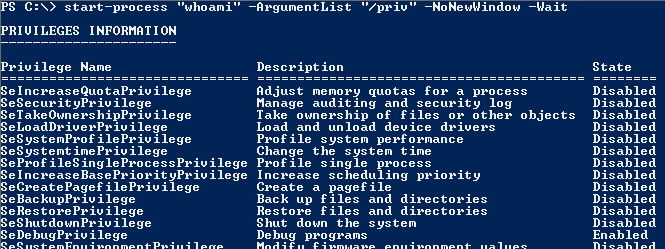
User Privileges
Information required to define a privileges escalation tactic
start-process "whoami" -ArgumentList "/priv" -NoNewWindow -Wait
Local Users
Get-LocalUser | ft Name,Enabled,LastLogon;
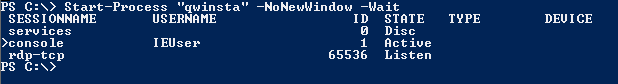
Logged in Users
Start-Process "qwinsta" -NoNewWindow -Wait
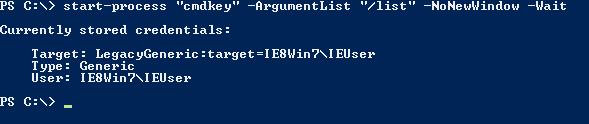
Credential Manager
start-process "cmdkey" -ArgumentList "/list" -NoNewWindow -Wait
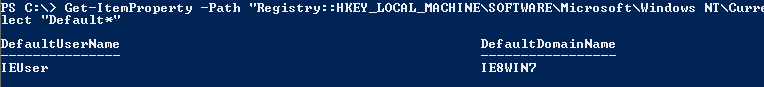
User Autologon Registry Items
Get-ItemProperty -Path "Registry::HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\WinLogon" | select "Default*"
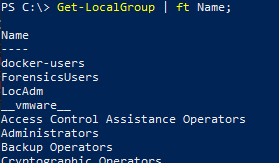
Local Groups
Get-LocalGroup | ft Name
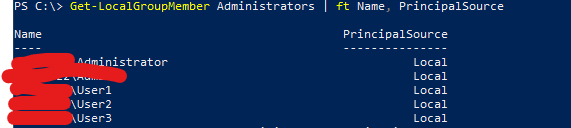
Local Administrators
Get-LocalGroupMember Administrators | ft Name, PrincipalSource
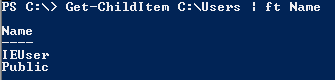
User Directories
Get-ChildItem C:\Users | ft Name
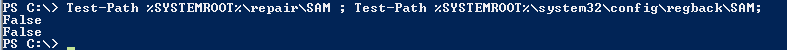
Searching for SAM backup files
A SAM backup file may be cracked in order to recover users credentials
Test-Path %SYSTEMROOT%\repair\SAM ; Test-Path %SYSTEMROOT%\system32\config\regback\SAM;
Running Processes
gwmi -Query "Select * from Win32_Process" | where {$_.Name -notlike "svchost*"} | Select Name, Handle, @{Label="Owner";Expression={$_.GetOwner().User}} | ft -AutoSize

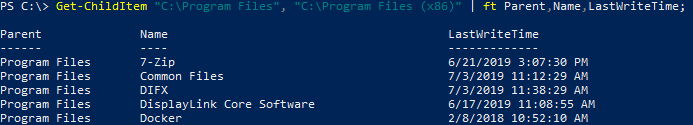
Installed Software Directories
Get-ChildItem "C:\Program Files", "C:\Program Files (x86)" | ft Parent,Name,LastWriteTime
Software in Registry
Get-ChildItem -path Registry::HKEY_LOCAL_MACHINE\SOFTWARE | ft Name
Folders with Everyone Permissions
Writable folders in sensitive location are useful for persistance
Get-ChildItem "C:\Program Files*", "C:\Program Files (x86)*" | % { try { Get-Acl $_ -EA SilentlyContinue | Where {($_.Access|select -ExpandProperty IdentityReference) -match "Everyone"} } catch {}}
Checking registry for AlwaysInstallElevated
Windows provide a group policy setting which allows a regular user to install a MSI package with system privileges: this can be abused by an attacker in order to escalate his privileges to SYSTEM
Test-Path -Path "Registry::HKEY_CURRENT_USER\SOFTWARE\Policies\Microsoft\Windows\Installer"
Unquoted Service Paths
When a service is created whose executable path contains spaces and isn’t enclosed within quotes, leads to a vulnerability known as Unquoted Service Path: Windows would handle the space as a break and pass the rest of the service path as an argument.
This misconfiguration may be exploited by an attacker in oder to execute commands with target service's privileges (usually SYSTEM).
gwmi -class Win32_Service -Property Name, DisplayName, PathName, StartMode | Where {$_.StartMode -eq "Auto" -and $_.PathName -notlike "C:\Windows" -and $_.PathName -notlike '"'} | select PathName, DisplayName, Name
Scheduled Tasks
Get-ScheduledTask | where {$_.TaskPath -notlike "\Microsoft*"} | ft TaskName,TaskPath,State;
Get-ChildItem C:\Windows\Tasks
Startup Commands
Get-CimInstance Win32_StartupCommand | select Name, command, Location, User
Searching for useful files containing sensitive information
Unattend and Sysprep files
Get-Childitem –Path C:\ -Include unattend,sysprep -File -Recurse -ErrorAction SilentlyContinue | where {($_.Name -like ".xml" -or $_.Name -like ".txt" -or $_.Name -like "*.ini")}
web.config files
Get-Childitem –Path C:\ -Include web.config -File -Recurse -ErrorAction SilentlyContinue
Files with credentials
Get-Childitem –Path C:\ -Include password,cred,vnc -File -Recurse -ErrorAction SilentlyContinue
Files with passwords
Get-ChildItem c:* -include .xml,.ini,.txt,.config -Recurse -ErrorAction SilentlyContinue | Where-Object {$_.PSPath -notlike "C:\temp" -and $_.PSParentPath -notlike "Reference Assemblies" -and $_.PSParentPath -notlike "Windows Kits"}| Select-String -Pattern "password"
Various config files
Get-Childitem –Path C:\ -Include php.ini,httpd.conf,httpd-xampp.conf,my.ini,my.cnf -File -Recurse -ErrorAction SilentlyContinue