Million of Android devices are vulnerable to a new SMS phishing attack
Researchers at CheckPoint said that over half of all Android handsets are vulnerable to a over-the-air (OTA) SMS phishing attack that could allow an attacker to route all internet traffic through a rogue proxy that can sniff traffic and steal information about (for example) email accounts and directory servers for synchronizing contacts and calendars.
According to the research, Samsung, Huawei, LG and Sony handsets are vulnerable to this attack technique.
What are OTA sms?
OTA provisioning is used to communicate with, download applications to, and manage a SIM card without being connected physically to the card.
If you've ever received a text message from your mobile network telling you to reboot your phone or that new settings have been applied to your SIM, you've received an OTA update.
The industry standard for OTA provisioning, Open Mobile Alliance Client Provisioning (OMA CP), includes rather limited authentication methods; a recipient cannot verify whether the suggested settings originate from his network operator or from an imposter. We found that phones manufactured by Samsung, Huawei, LG and Sony (corresponding to over 50% of all Android phones, according to market share data from 2018: http://gs.statcounter.com/vendor-market-share/mobile/worldwide/) allow users to receive malicious settings via such weakly-authenticated provisioning messages. Samsung phones compound this by allowing unauthenticated OMA CP messages as well.
How the attack works?
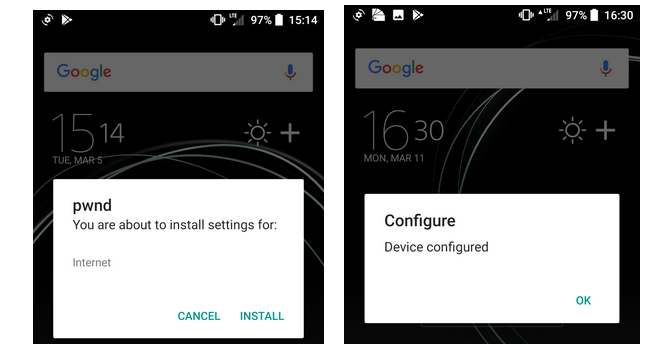
According to CheckPoint's report:
To send OMA CP messages, an attacker needs a GSM modem (either a $10 USB dongle, or a phone oper ating in modem mode), which is used to send binary SMS messages, and a simple script or off-the-shelf software, to compose the OMA CP.
The phishing CP messages can either be narrowly targeted, e.g. preceded with a custom text message tailored to deceive a particular recipient, or sent out in bulk, assuming that at least some of the recipients are gullible enough to accept a CP without challenging its authenticity.
OMA CP allows changing the following settings over-the-air:
- MMS message server
- Proxy address
- Browser homepage and bookmarks
- Mail server
- Directory servers for synchronizing contacts and calendarAnd more.
When the user receives an OMA CP message, they have no way to discern whether it is from a trusted source. By clicking 'accept', they could very well be letting an attacker into their phone
How can i defend my handset from this attack?
Anyone who has a cheap USB modem is able to trick users into installing malicious settings onto their phones.
However, the attacker needs to know the victims’ IMSI numbers, which can be obtained via an Android application having READ_PHONE_STATE permission (or using a IMSI catcher).
So, always pay attention before install on your smartphone a new application of uncertain origin (and the permissions it requires) and avoid clicking "Ok" too quickly if you receive a configuration message!