PEpper: a python script to perform malware static analysis on Portable Executable format
A useful tool: fast and easy to use.
What is Portable Executable
The Portable Executable format is the standard file format for executables, object code and DLLs used in 32- and 64-bit versions of Windows operating systems.
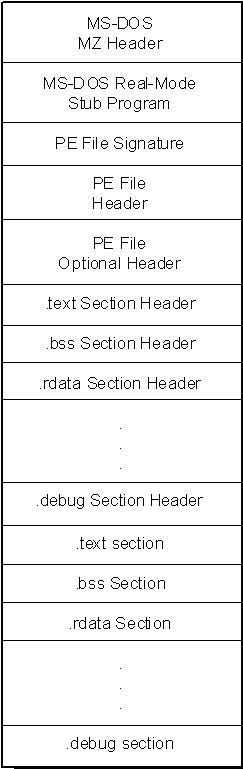
The PE file format is organized as a linear stream of data.
It begins with an MS-DOS header, a real-mode program stub, and a PE file signature.
Following is a PE file header and optional header. Beyond that, all the section headers appear, followed by all of the section bodies.
Closing out the file are a few other regions of miscellaneous information, including relocation information, symbol table information, line number information, and string table data.
PEpper
PEpper is a python script, developed to perform malware static analysis on Portable Executable.
Static analysis checks for malware without inspecting the actual code or instructions.
It applies various techniques and tools to swiftly decide whether the file is malicious or not.
The indicators collected using static analysis may comprise the file name, file type, file size, and MD5 checksums or hashes recognized by antivirus detection tools.
PEpper is able to extract this set of information:
- Suspicious entropy ratio
- Suspicious name ratio
- Suspicious code size
- Suspicious debugging time-stamp
- Number of export
- Number of anti-debugging calls
- Number of virtual-machine detection calls
- Number of suspicious API calls
- Number of suspicious strings
- Number of YARA rules matches
- Number of URL found
- Number of IP found
- Cookie on the stack (GS) support
- Control Flow Guard (CFG) support
- Data Execution Prevention (DEP) support
- Address Space Layout Randomization (ASLR) support
- Structured Exception Handling (SEH) support
- Thread Local Storage (TLS) support
- Presence of manifest
- Presence of version
- Presence of digital certificate
- Packer detection
- VirusTotal database detection
- Import hash
The installation is fast and simple: just clone the git repository, resolve the dependencies and install the tool using PIP:
$ git clone https://github.com/Th3Hurrican3/PEpper/ $ cd PEpper $ pip3 install -r requirements.txt $ python3 pepper.py ./malware_dir