#WIBattack: Not only S@T Browser, but also WIB SIM toolKit is vulnerable to SimJacker attacks
Do you remember the Simjacker vulnerability, that resides in the S@T Browser toolkit, installed on a variety of SIM cards provided by mobile operators in at least 30 countries?
Well, a researcher at Ginno Security Lab has revealed that another SIM toolkit, called Wireless Internet Browser (WIB), can also be exploited in the same way, exposing another set of hundreds of millions of mobile phones users to remote hackers.
The attack
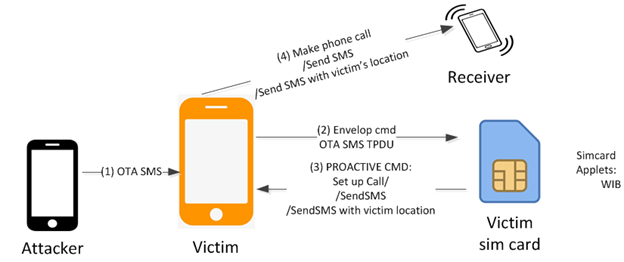
The attack scenario is very similar to the S@T vulnerability, according with the researcher report:
(1) Attacker sends a malicious OTA SMS to the victim phone number. The OTA SMS contains WIB command such as: SETUP CALL, SEND SMS, PROVIDE LOCATION INFO, etc.
(2) Right after receiving the OTA SMS, Baseband Operating System of the victim mobile phone uses ENVELOP COMMAND ( an APDU command to communicate between mobile phone and simcard) to forward the TPDU of the OTA SMS to WIB browser in victim’s simcard.
Different from the procedure of receiving the normal text sms, the procedure OTA SMS is silently handled just in baseband operating system and does not raise any alert to application operating system (android os, ios, blackberry os, …). Neither feature phone nor smart phone raises alert about the procedure of ota sms: no ringing, no vibration, no detection from users.
(3) WIB browser follows the WIB commands inside the TPDU of OTA SMS and sends the corresponding PROACTIVE COMMAND to the victim mobile phone such as: SETUP CALL, SEND SMS, PROVIDE LOCATION INFO.
(4) The victim mobile phone follows the PROACTIVE COMMAND received from victim’s simcard to perform the corresponding actions such as: make a phone call, send an sms to whatever phone number attacker wants
The flaw can be exploited to perform several tasks on a targeted device just by sending an SMS forged with a specific code:
- Retrieving targeted device' location and IMEI information
- Sending fake messages
- Launching victim's phone browser and forcing it to open a malicious web page
- Performing calls to premium-rate numbers
- Performing denial of service attacks by disabling the SIM card
- Retrieving other information like language, radio type, battery level, etc.
How much popular is the WIB toolkit?
SmartTrust is a leading provider of infrastructure solutions designed to enable secure mobile e-services. More than 85 mobile operators worldwide are using SmartTrust technology to diversify their service offerings and open new revenue streams by launching enhanced SMS services, controlling mobile end-user applications and managing the entire life cycle of the SIM/USIM.
Customers include: Vodafone UK, D2, Telenor, Sonofon, VoiceStream, Cingular Wireless, China Mobile, Bharti Cellular, Satelindo, Smart Communications, MTN and Z-Tone. The company has operations in Europe, Asia, The Americas and Australiahttps://cardflash.com/news/2002/10/oberthur-wib-certification/
How to protect from SimJacker attacks?
From mobile operator's side
- Configure message center (SMSC) in order to allow messages with STK coding from home subscribers only to the MNO platform, and not to other subscribers.
- If a SMSCs is connected to a partner content providers via SMPP and SS7, disallow messages with STK coding: content providers generally send text only in the form of A2P SMS messages.
- Finally, if SMS Home Routing hosts for incoming SMS traffic is sending SMS traffic with STK coding to home subscribers, this is clearly illegitimate activity that must be stopped.
From the user's side
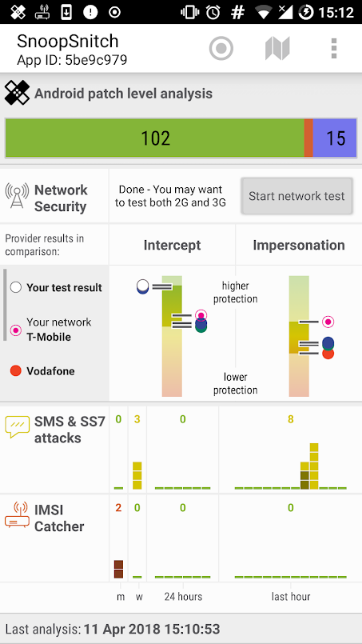
There's not too much to do, because the remediation is largerly in the hands of the mobile operators .
However, researchers at SRLabs developed an Android app called SnoopSnitch, which can detect attacks based on suspicious binary SMS including Simjacker and alert users of it.
You can download SnoopSnitch from Google Play Store, but you need to have a rooted Android smartphone with a Qualcomm chipset.