Some thoughts about Windows 10 "Timeline" forensics artifacts
Today i'll talk you briefly about the Windows 10 "Timeline": a feature that can come in handy during a forensic analysis.
How to access it and how to analyze it?
Since the April 2018 Update, Windows 10 includes a feature called “Timeline”.
Timeline is like a browser history, but for your whole computer: it provides a chronology that contains visited websites, edited/opened documents, played games, viewed images and so on.
A great resource for the forensic investigator!
The activity log is located in thie path C:\Users[USERNAME]\AppData\Local\ConnectedDevicesPlatform\AAD.xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx\ActivitivitiesCache.db.
“ActivitiesCache.db” is a SQLite (viewable with any SQLite browser) database containing 7 tables:
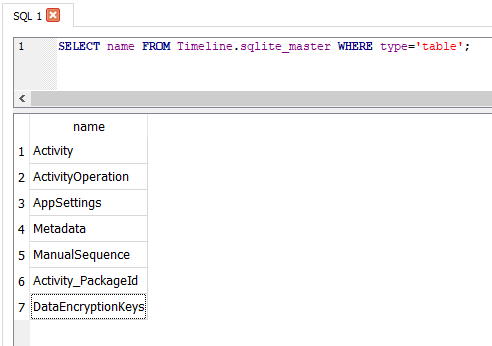
- Activity
- ActivityOperation
- AppSettings
- Metadata
- ManualSequence
- Activity_PackageId
- DataEncryptionKeys
The most interesting table is Activity, as it contains data directly related to the entries displayed in the timeline and how that data is displayed.
Much of the data in the Activity table (and indeed the database as a whole) is serialised as JSON, sometimes stored as text and other times as a binary data in a BLOB field, with the text encoded as UTF-8.
Activities also have an associated App ID, stored as a JSON object in the AppId field: it does not record the application which generated the activity, rather it contains a list of applications which are suitable for continuing this activity across multiple platforms.
Remember: this activity log has been created in order to allow also a syncronization through differente devices and cloud instances, non with forensic purposes!
Automated parsing of the ActivitivitiesCache.db
Eric Zimmerman has written a tool to parse this database, named WxTCmd:

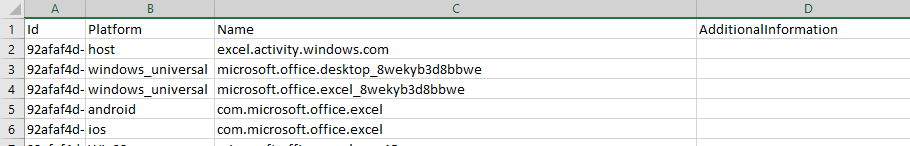
The tools process the ActivitivitiesCache.db and exports all activities in a single CSV file.
You can find it on the Eric's github page: https://ericzimmerman.github.io/