Court forces e-mail provider Tutanota to release unencrypted messages
The e-mail provider Tutanota advertises to be the "world's most secure e-mail service".
The company offers encrypted e-mail communication and claims to have six million customers relying on this security promise.
However, on October 2, 2018, the district court of Itzehoe asked managing director Matthias Pfau to provide the e-mails of Tutanota unencrypted and in real time to the police [4].
Why?
In the previous months hackers blackmailed several companies based in Schleswig-Holstein, using an e-mail address from Tutanota.
So the investigators wanted to read the e-mails to get the cyber criminals on the track.
So this case leads to a dispute between security authorities, who claims that too secure encryption methods avoids the tracking of suspect, and privacy advocates, who want more data to be encrypted to better protect citizens and businesses from criminals, espionage and data hunger by tech companies.
How Tutanota works?
Tutanota's service works like this: when two users write an e-mail, it is automatically protected with the most secure end-to-end encryption. Only sender and receiver can read the message.
However this works only between tutanota users: mail providers like Google or Hotmail do not have such protection.
If a customer receives an e-mail from a person who does not have a Tutanota account, according to provider FAQ, the message was automatically encrypted as soon as it lands on Tutanota servers.
The court request
Therefore, the district court asked to Tutanota that the entire contents of the e-mails be sent out without end-to-end encrypted.
The company initially refused, however, five months later, the court ruled that Tutanota must hand over the data and imposed a fine of $ 1,000.
Now Tutanota has to program a new function for the prosecutors: If an account has a valid legal order from a German court, the company must also create a copy of the e-mails that the investigators can read.
Obiously, authorities still cannot read mails sent with end-to-end encryption between Tutanota users.
So what?
In this reddit thread on /r/privacytoolIO [1], Tutanota team attended the conversation, basically confirming concerns of privacy conscious users:
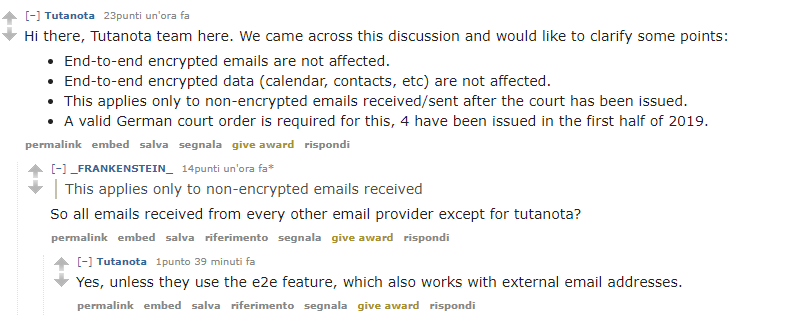
Tutanota:
Hi there, Tutanota team here. We came across this discussion and would like to clarify some points:
- End-to-end encrypted emails are not affected.
- End-to-end encrypted data (calendar, contacts, etc) are not affected.
- This applies only to non-encrypted emails received/sent after the court has been issued.
- A valid German court order is required for this, 4 have been issued in the first half of 2019.
This applies only to non-encrypted emails received
So all emails received from every other email provider except for tutanota?
Yes, unless they use the e2e feature, which also works with external email addresses.
My 2 cents
In a privacy context, relying on just one security layer is wrong.
Thinking that with a secure provider your messages are secured and confidential means overstimate your privacy model.
So, reinforce every sensible message with an additional layer of security, using (for example) PGP encryption [2], suitable also from webmails and with providers less privacy-focused (like Gmail), using a specific browser extension [3].