My Weekly RoundUp #123
Just some stuff i read in the last seven days...
Cybersecurity
Cable Haunt: Unknown millions of Broadcom-based cable modems open to hijacking

A vulnerability (CVE-2019-19494) in Broadcom‘s cable modem firmware can open unknown millions of broadband modems by various manufacturers to attackers, a group of Danish researchers has warned.
CVE-2019-19494, also dubbed Cable Haunt, is present in the spectrum analyzer, a standard component of Broadcom chips that identifies potential problems with the connection through the modem’s coaxial cable.
“The cable modems are vulnerable to remote code execution through a web-socket connection, bypassing normal CORS and SOC rules, and then subsequently by overflowing the registers and executing malicious functionality. The exploit is possible due to lack of protection proper authorization of the web-socket client, default credentials and a programming error in the spectrum analyzer,” the researchers explained.
“These vulnerabilities can give an attacker full remote control over the entire unit, and all the traffic that flows through it, while being invisible for both the user and ISP and able to ignore remote system updates.”
How Malware Gains Trust by Abusing the Windows CryptoAPI Flaw
The new Windows CryptoAPI CVE-2020-0601 vulnerability disclosed by the NSA can be abused by malware developers to sign their executables so that they appear to be from legitimate companies. This creates trust in the program, which may cause a user to be more willing to execute them.
Most of the coverage of this vulnerability illustrates how the vulnerability can be exploited to spoof certificates used for TLS connections to web sites and perform MiTM attacks.
For example, Kudelski Security illustrated how they used the vulnerability to create a fake certificate that impersonates github.com. To protect users, Chrome added protections that block users from accessing sites using these spoofed certificates.
China-linked APT40 group hides behind 13 front companies
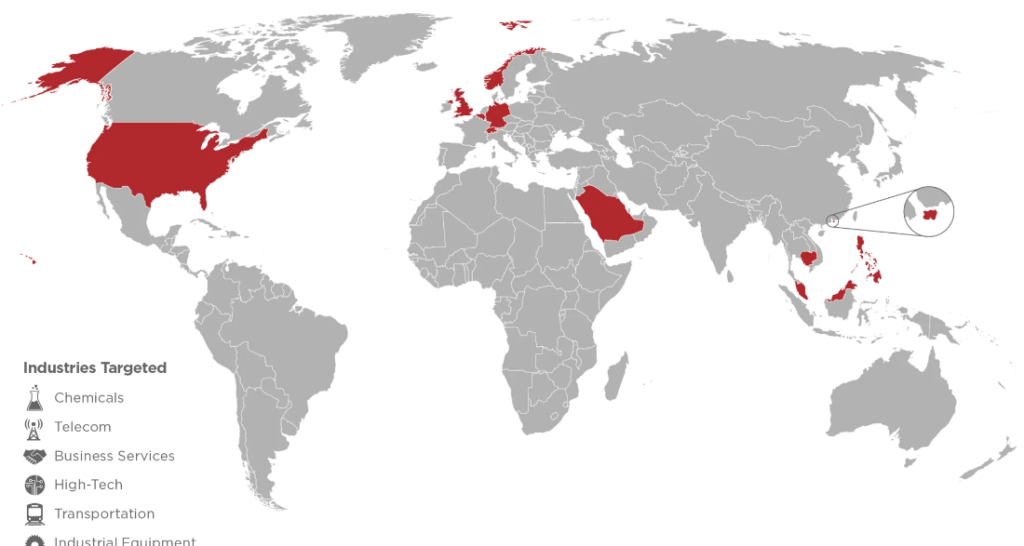
A group of anonymous security researchers that calls itself Intrusion Truth has discovered that a China-linked cyberespionage group, tracked as APT40, uses 13 front companies operating in the island of Hainan to recruit hackers.
The Intrusion Truth group has doxed the fourth Chinese state-sponsored hacking operation.
“We know that multiple areas of China each have their own APT.” reads the report.
“After a long investigation we now know that it is possible to take a province and identify front companies, from those companies identify individuals who work there, and then connect these companies and individuals to an APT and the State.”
The Intrusion Truth group has already other APT groups operating in other provinces of the country, including APT3 (from the Guangdong province), APT10 (from Tianjin province), and APT17 (Jinan province). The last group tracked by the researcher is now operating out of the Hainan province, an island in the South China Sea.
Intrusion Truth did not associate the group from Hainan with a specific Chinese APT group, but FireEye and Kaspersky researchers believe that the China-linked group is the APT40 (aka TEMP.Periscope, TEMP.Jumper, and Leviathan).
Ryuk Ransomware Uses Wake-on-Lan To Encrypt Offline Devices
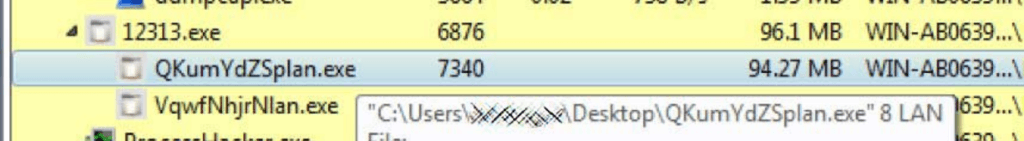
The Ryuk Ransomware uses the Wake-on-Lan feature to turn on powered off devices on a compromised network to have greater success encrypting them.
Wake-on-Lan is a hardware feature that allows a powered down device to be woken up, or powered on, by sending a special network packet to it. This is useful for administrators who may need to push out updates to a computer or perform scheduled tasks when it is powered down.
According to a recent analysis of the Ryuk Ransomware by Head of SentinelLabs Vitali Kremez, when the malware is executed it will spawn subprocesses with the argument '8 LAN'.
Technology
Minecraft mod creates huge in-game Harry Potter RPG
Despite Warner Bros Interactive Entertainment definitely working on their Harry Potter RPG game, it is taking the publisher a long time to admit it. Thankfully, for those wishing to get their wizarding on, Minecraft modders Floo Network are working to bring you into a more cubic version of Hogwarts.
Shown off through an in-depth YouTube video, the modding group showed their incredible attention to detail in recreating the world of Harry Potter. The Minecraft recreation isn’t limited to just Hogwarts; every main location from the original stories are in playable form.
In the Minecraft School of Witchcraft and Wizardry, players can explore and learn through Hogwarts, trade in Diagon Alley, complete quests and explore iconic locations throughout the Wizarding World.
Bitcoin fans just turned their Tesla car into a full node
Tesla cars are capable of a lot, from self-driving, smart summoning, and automatic parking — but what about running Bitcoin?
As it turns out, they can do that too. Cryptocurrency fans have shared video footage of a Tesla car’s onboard computer system operating as a Bitcoin full node.
This is possible thanks to the Bcoin project, which shared the video. Bcoin is an alternative implementation of the Bitcoin protocol that any machine — like Tesla‘s onboard computer — can run via its internet browser to join in the consensus process.
So, for at least a short while, there was a Tesla car out there helping to keep Bitcoin chugging along smoothly.
Privacy
Unable to unlock gunman’s iPhones, the FBI (once again) asks for Apple’s help

Attorney General William Barr ratcheted up the standoff when, according to the New York Times, he declared the shooting an act of terrorism. Barr issued an extraordinarily high-profile call for Apple to provide access to the gunman's two iPhones. He also said that to date Apple has provided no “substantive assistance” in doing so. The development further suggests that the 2016 high-stakes clash pitting privacy against national security are likely to play out again.
DuckDuckGo is Now a Default Search Engine Option on Android in the EU

DuckDuckGo will soon be offered as an option for default search engine on Android devices across the EU.
European regulators are forcing Google to present Android users with the option to choose their own default search engine. The option to choose default search providers has always been available on Android devices, but it’s something users would have to seek out on their own in the settings menu.
Google’s previous practices of setting itself as the default search provider on its own operating system was ruled illegal under EU antitrust rules. As a result, Google was hit with a record-breaking $5 billion fine.
Now, Google has to change its practices and prompt users to choose their own default search engine when setting up a European Android device that has the Google Search app built in. Not all countries will have the same options, however, as the choices included in Google’s new prompt all went to the highest bidders.
Programming
Terrier: An Open-Source Tool for Identifying and Analyzing Container and Image Components
As part of our Blackhat Europe talk “Reverse Engineering and Exploiting Builds in the Cloud” we publicly released a new tool called Terrier.
In this blog post, I am going to show you how Terrier can help you identify and verify container and image components for a wide variety of use-cases, be it from a supply-chain perspective or forensics perspective. Terrier can be found on Github https://github.com/heroku/terrier.
Entertainment
Netflix Got More Oscar Nominations Than Any Other Studio

Despite the anticipation they drum up, the Oscars are nothing if not predictable. (Seriously, predicting who will be nominated for, and win, Academy Awards is practically a news media—and social media—sport.) This year is seemingly no different, as, once again, the Academy announced the nominations today, and the field is largely white and not a single woman was given a best-director nod. (The nominees in that category were Quentin Tarantino for Once Upon a Time in Hollywood, Martin Scorsese for The Irishman, Sam Mendes for 1917, Bong Joon Ho for Parasite, and Todd Phillips for Joker.) Joker led the nominations across the board, with 11—including one for best picture, a category that includes 1917, Ford v Ferrari, The Irishman, Jojo Rabbit, Little Women, Marriage Story, Once Upon a Time in Hollywood, and Parasite (the first South Korean film to be nominated for best picture and best international feature). Overall, The Irishman, 1917, and Once Upon a Time in Hollywood each got 10 nods, while Jojo Rabbit, Little Women, Marriage Story, and Parasite all nabbed six. In an interesting twist, Netflix received more nominations—24—than any other major Hollywood studio or distributor, thanks in large part to the performance of The Irishman and Marriage Story.