Ghostcat (CVE-2020-1938): ongoing scans for unpatched Apache Tomcat servers. Patch now!
A brief update regarding the Ghostcat vulnerability (CVE-2020-1938) that affects Apache Tomcat servers.
According to a tweet by cyber threat intelligence firm Bad Packets, "mass scanning activity targeting this vulnerability has already begun":
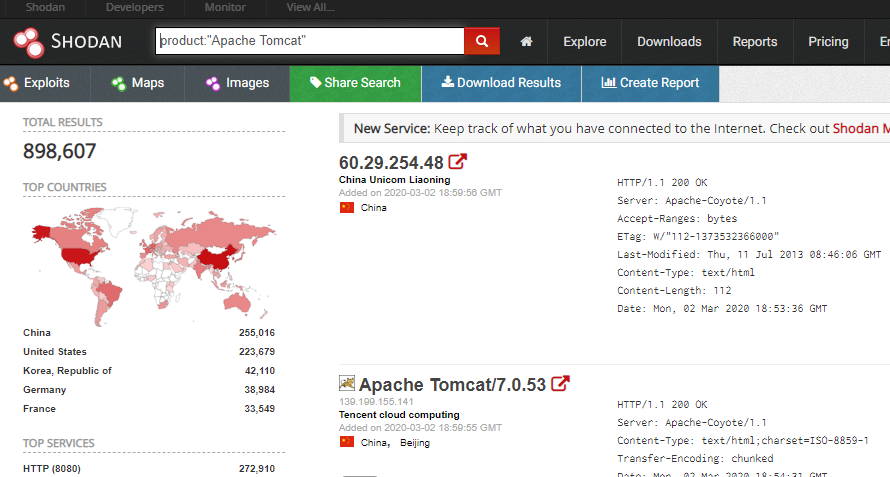
The attack perimeter is huge: according to Shodan [1], more than 890,000 Tomcat servers are currently reachable over the Internet.
More information about patching/mitigations are available on my previous post.
Patch, patch ASAP!
References
Further readings
- Apache Tomcat AJP Ghostcat File Read / Inclusion
- Ghostcat bug impacts all Apache Tomcat versions released in the last 13 years - ZDNet
- 13-year-old Ghostcat Bug Affected Apache-Tomcat Let Hackers Remotely Inject Any Files in The Servers - GBHackers
- CVE-2020-1938: Ghostcat aka Tomcat 9/8/7/6 in the default configuration (port 8009) leading to disclosure of configuration files and source code files of all webapps deployed and potentially code execution - REDDIT
- https://github.com/0nise/CVE-2020-1938
- https://github.com/xindongzhuaizhuai/CVE-2020-1938
- https://github.com/nibiwodong/CNVD-2020-10487-Tomcat-ajp-POC
- https://github.com/laolisafe/CVE-2020-1938
- https://github.com/YDHCUI/CNVD-2020-10487-Tomcat-Ajp-lfi