Windows Forensic Analysis: some thoughts on RDP related Event IDs
Recently I had to perform a forensic investigation on a server that had made some strange Remote Desktop activities.
In that case, the analysis of windows events has turned out really useful.
So, today I'd like to share a brief cheatsheet of Windows Event IDs related to RDP activities.
Connection
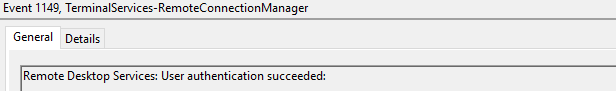
Event ID 1149
Logfile
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-RemoteConnectionManager%4Operational.evtx
Description
User authentication succeeded
Despite this description, this event does not indicate a successful user authentication: actually is referring to successful network authentication, like as a user who launched an RDP client and connected to the target displaying the target system’s screen.
Authentication
Login successful
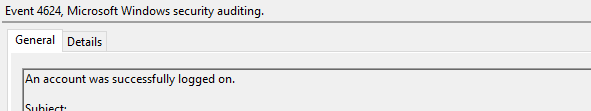
Event ID 4624
Logfile
%SystemRoot%\System32\Winevt\Logs\Security.evtx
Description
An account was successfully logged on
A user successfully logged on to the target system: this step generates a type 10 logon type, or type 7 if it’s a reconnection from a previous/existing RDP session.
Login failed
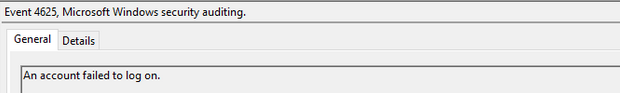
Event ID 4625
Logfile
%SystemRoot%\System32\Winevt\Logs\Security.evtx
Description
An account failed to log on
User failed to log on to the target system: this event is helpful in identifying suspicious activities.
The Status Code and Sub Status Code will also be helpful in identify legitimate failures (for example an expired password) as well as malicious activities such as brute force attemps.
Session Connected
This group of events covers the post-authentication process that occours upon successful authentication and logon to the system.
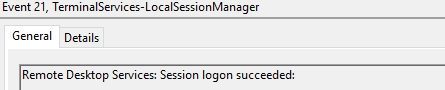
Event ID 21
Logfile
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
Description
Remote Desktop Services: Session logon succeeded
Indicates successful RDP logon and session instantiation, only when the Source Network Address contains a remote IP address: if Source Network Address is LOCAL, this event indicates a local logon and and will also be generated upon system (re)boot/initialization.
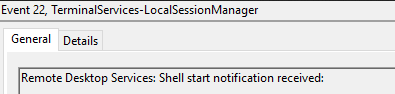
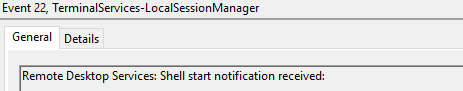
Event ID 22
Logfile
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
Description
Remote Desktop Services: Shell start notification received
This typically immediately accours after an Event ID 21, and indicates successful RDP logon and Windows Explorer start.
Like event 21, a Source Network Address set to LOCAL indicates a local logon.
Session Disconnected
There are some ID related to disconnection events:
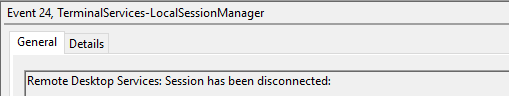
Event ID 24
Logfile
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
Description
Remote Desktop Services: Session has been disconnected
This event indicates that a user has disconnected from an RDP session, when the Source Network Address contains a remote IP address.
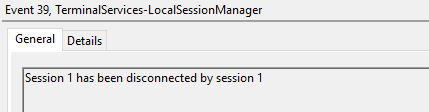
Event ID 39
Logfile
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
Description
Session X has been disconnected by session Y
This event indicates that a user has formally disconnected from an RDP session via the Disconnect function in Windows GUI versus simply close out of the RDP window.
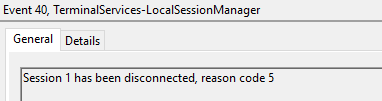
Event ID 40
Logfile
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
Description
Session X has been disconnected, reason code Z
This event also specify information about the reason of disconnection.
The list of reason codes can be seen here: https://docs.microsoft.com/en-us/windows/win32/termserv/extendeddisconnectreasoncode
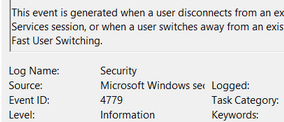
Event ID 4779
Logfile
%SystemRoot%\System32\Winevt\Logs\Security.evtx
Description
A session was disconnected from a Window Station.
This event occurs when a user disconnects from an RDP session: is usually paired with Event IDs 24, 39 and 40.
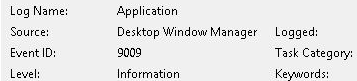
Event ID 9009
Logfile
%SystemRoot%\System32\Winevt\Logs\System.evtx
Description
The Desktop Window Manager has exited with code...
Occurs when a user formally closes the RDP desktop GUI: useful to identify a closed/finalized RDP connection.
Session Reconnected
This couple of events occours when a user reconnect to a RDP session.
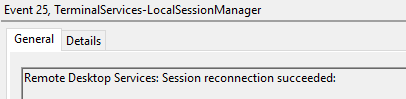
Event ID 25
Logfile
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
Description
Remote Desktop Services: Session reconnection succeeded
This event refers to a user reconnection to an RDP session, but only when the Source Network Address contains a remote IP address.
Event ID 4778
Logfile
%SystemRoot%\System32\Winevt\Logs\Security.evtx
Description
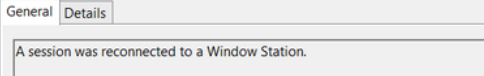
A session was reconnected to a Window Station.
This event occurs when a user reconnects to an existing RDP session: is usually paired with Event ID 25.
Logoff
This group of events cover the case of a user's logoff performed using the 'Logoff' feature of Windows GUI
Event ID 23
Logfile
%SystemRoot%\System32\Winevt\Logs\Microsoft-Windows-TerminalServices-LocalSessionManager%4Operational.evtx
Description
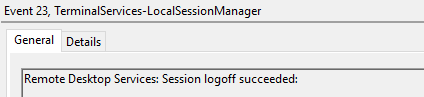
Remote Desktop Services: Session logoff succeeded
This event refers to a user reconnection to an RDP session, but only when the Source Network Address contains a remote IP address.
Event ID 4634
Logfile
%SystemRoot%\System32\Winevt\Logs\Security.evtx
Description
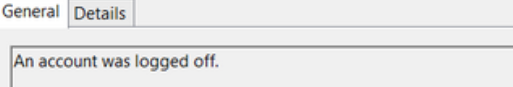
An account was logged off.
This event occurs whenever a user disconnects from an RDP session or formally logs off (via Windows Start Menu Logoff).
This is typically paired with an Event ID 23.
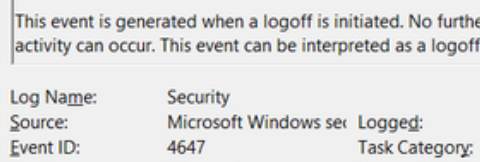
Event ID 4647
Logfile
%SystemRoot%\System32\Winevt\Logs\Security.evtx
Description
User initiated logoff
This event occurs when a user initiates a system logoff: is not necessarily RDP specific.