CobaltStrikeScan: identify CobaltStrike beacons in processes memory
Cobalt Strike was born as a penetration testing tool, useful for Red Teaming activities.
However, several threat actors started using it in real attacks. So, a proper detection of Cobal Strike activities during an incidend respose process is extremely important.
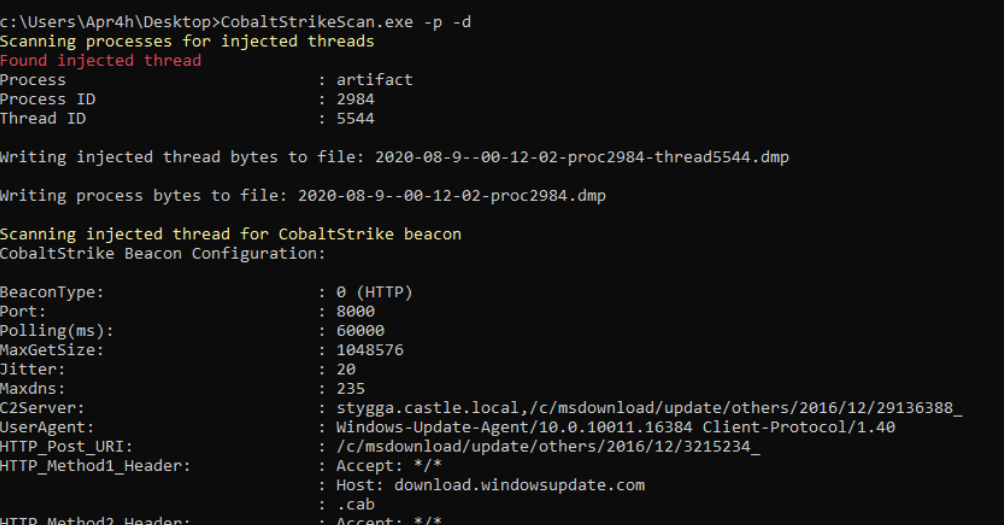
A security researcher known as "Apra" has published on his GitHub account [2] a new tool, called "CobaltStrikeScan" [1], useful for identify Cobalt Strike beacons in files and processes memory:
CobaltStrikeScan scans Windows process memory for evidence of DLL injection (classic or reflective injection) and performs a YARA scan on the target process' memory for Cobalt Strike v3 and v4 beacon signatures.
Alternatively, CobaltStrikeScan can perform the same YARA scan on a file supplied by absolute or relative path as a command-line argument.
If a Cobalt Strike beacon is detected in the file or process, the beacon's configuration will be parsed and displayed to the console.
References