iOS Forensic: full disk acquisition using checkra1n jailbreak
A simple step-to-step tutorial for iOS full acquisition.
The release of Checkm8 iOS exploit, in september 2019, was a bit topic: an exploit could be used on every iOS device made over an approximately 5-year period had major consequences.
Checkm8 is a iOS BootROM vulnerability exploit which affects iPhone 4S through to iPhone X (A5 to A11 chipsets).
Starting from this exploit, has been developed another tool called checkra1n [1]: a jailbreak tool based on the Checkm8 exploit on iOS operating system for iOS 12.3 and up.
In this brief article, I tried to provide a simple workflow useful to perform a iOS system acquisition using a Linux system and the checkra1n jailbreak.
So, before to start, we need to fulfil some requirements.
Install checkra1n and iProxy
checkra1n can be fetched from official repository (tested on Debian/Ubuntu):
echo "deb https://assets.checkra.in/debian /" | sudo tee -a /etc/apt/sources.list sudo apt-key adv --fetch-keys https://assets.checkra.in/debian/archive.key sudo apt update sudo apt install checkra1n
We also needs iProxy, which is contained within the libusbmuxd-tools package:
sudo apt install libusbmuxd-tools
Perform jailbreak
Start checkra1n with root privileges:
$ sudo checkra1n
The tool starts with a simple GUI:
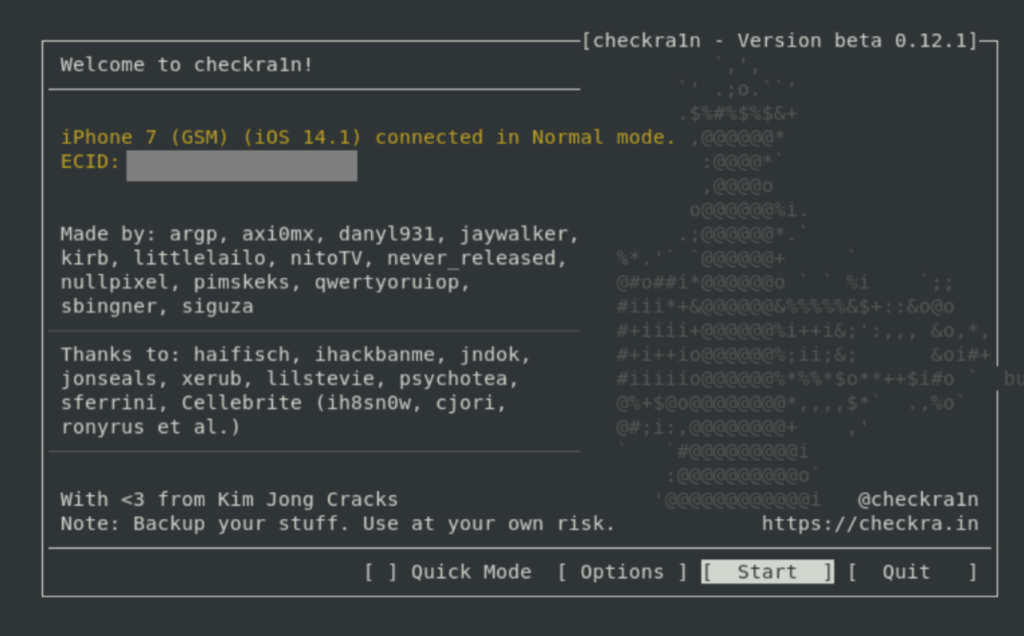
Then connect target iOS device, "Trust" it the computer entering device unlock code.
Select “Start” and follow the prompts to place the device into DFU mode:
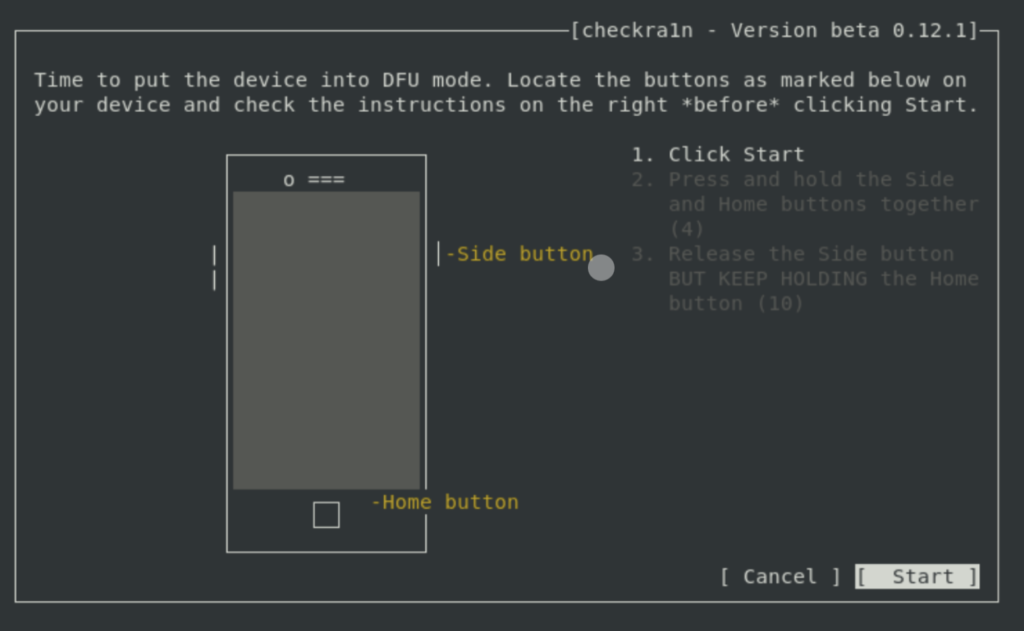
Wait until this process completes.
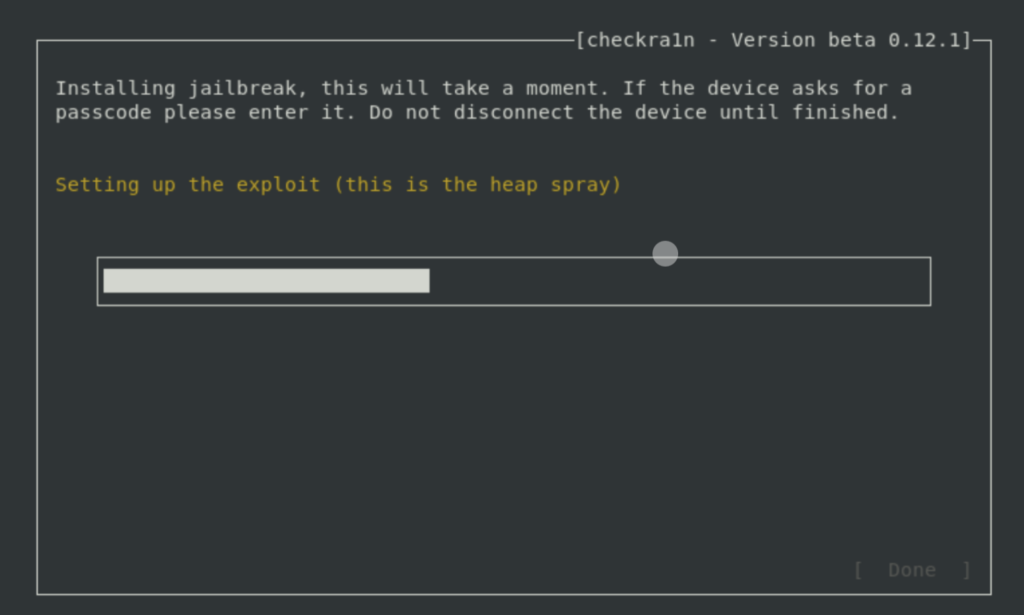
Once the device has booted you can run iproxy to allow you to SSH into iOS device via USB:
$ iproxy 4242 22
Now is possible to access into device via SSH (root password is alpine):
$ ssh root@127.0.0.1 -p 4242
Perform acquisition
In order to perform a “partition-to-image” acquisition, you can use DD:
ssh root@127.0.0.1 -p 4242 dd if=/dev/rdisk0s1s1 bs=4k | dd of=system.dd
You can use as input device rdisk0s1s1, if you need to acquire system partition, or rdisk0s1s2, which corresponds to the second slice of the device internal storage, containing the data partition [2].
Furthermore, you cal also acquire the user data using tar:
$ ssh root@127.0.0.1 -p 4242 'tar -cf - /private/var/' > private-var.tar
From here, you can parse the tarball in your forensic tool of choice (for example Autopsy).