How to detect Cobalt Strike Beacons using Volatility
Recently I’ve already written about Cobalt Strike detection during forensics analysis. However, some followers asked my if it was possibile to perform this activities using Volatility, in order to integrate them in existing analysis workflows.
Well, a solution has been already developed by japanise CERT: a Volatility plugin [3] useful to identify Cobal Strike activities in memory dumps.
The plugin provides a couple of useful features:
- cobaltstrikescan: Detect Cobalt Strike Beacon from memory image
- cobaltstrikeconfig: Detect Cobalt Strike Beacon from memory image and extract
How to install and run the plugin
First, download the plugin (cobaltstrikescan.py) from JP-CERT GitHub repository and save it in ”contrib/plugins/malware” folder in Volatility.
Then, execute the following command:
$python vol.py [cobaltstrikescan|cobaltstrikeconfig] –f <memory.image> ––profile=<profile>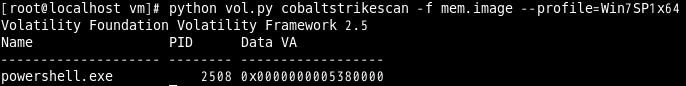
The plugin has been released in 2018, so I would recommend, in case you are facing an incident with a big spread, to customize it in order to fit detection with updated data from forensics analysis of compromised hosts.
In order to modify the plugin, you can refer to the useful tutorial [4] realized by Iñaki Abadía.