Didier Stevens: finding Metasploit & Cobalt Strike URLs
An interesting article and video lesson by security reserarcher Didier Stevens.
Cobalt Strike and Metasploit are the offensive security tools most commonly used to host malware command-and-control (C2) servers: both tool allows generation of shellcode for http(s) shells so, during a malware/forensic analysis, is really useful be able to identify URLs used by this kind of payloads.
The researcher Didier Stevens comes to our help with a couple of articles published on SANS ISC forum:
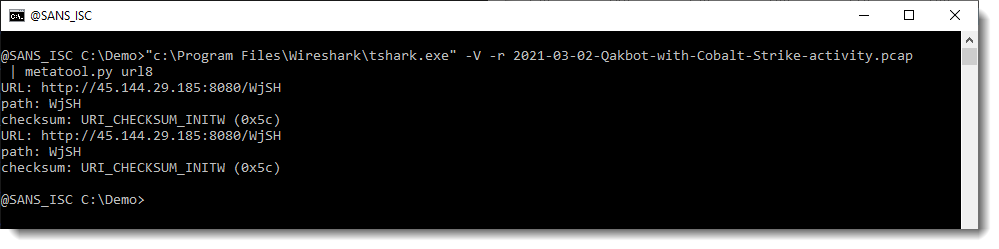
Metasploit and Cobalt Strike generate shellcode for http(s) shells. The URLs found in this shellcode have a path that consist of 4 random alphanumeric characters. But they are not completely random: their 8-bit checksum is a member of a small set of constants.
In the first post [1] Stevens explains how, starting from a network traffic dump generated with Wireshark, it is possible to identify some patterns related to Metasploit and Cobal Strike activities using metatool.py [2], a python utility developed by himself.
Few days after, Stevens published another post [3], this time with a video, in order to show the method and explaining in detail the checksum calculation.
I don't use this method to go hunting (in proxy logs for example), as the checksum has a low-entropy, thus prone to collisions/false positives. But I do use this when I suspect the presence of Metasploit or Cobalt Strike traffic.
Cobalt Strike beacons often use HTTPS, but the URLs I talked about in my diary entry, are not the ones used by the beacon itself. These are the URLs of the staging shellcode, that precedes the beacon.
I hope it will be helpfull!