How smartphones reacts to IMSI catching attacks?
I recently happened to read a research, presented during the ACM WINTECH 2020 conference, related to IMSI Catchers and their exploitation for tracking users of mobile devices.
Mobile telephony standards have always used and recorded user's locations: when a user moves across the various radio cells, his mobile phone must identify itself with the cell, and this could allow to track its position simply by "listening" to the user's identification (the IMSI - International Mobile Subscriber Identity) transmitted by the mobile phone.
To overcome this problem, starting from the GSM standard adopted in second generation mobile phones, instead of transmitting the IMSI, the mobile phone uses an anonymized version of the user identification, called TMSI (Temporary Mobile Subscriber Identity), that constantly being changed and this should prevent a malicious user capable of analyzing radio transmissions to locating and tracking users
However, there are devices, called IMSI catchers, which are able to "deanonymize" those identifiers, generally made by specialized manufacturers and are mainly used by law enforcement agencies to identify and track the SIM cards used by suspects.
What is an IMSI-catcher?
I've already written about this topic [1]:
IMSI-catcher is a telephone eavesdropping device used for intercepting mobile phone traffic and tracking movement of mobile phone users.
Essentially consist of a “fake” mobile tower acting between the target mobile phone and the service provider’s real towers with a man-in-the-middle (MITM) attack.
IMSI-catchers are used in some countries by law enforcement and intelligence agencies, but their use has raised significant civil liberty and privacy concerns and is strictly regulated in some countries. Furthermore, some countries do not even have encrypted phone data traffic or uses a very weak encryption, thus rendering an IMSI-catcher unnecessary.
The IMSI-Catchers are so commonly used, are very easy to using and they leave no traces.
The research
The 5Gsec group of the CNIT research unit of the University of Rome Tor Vergata, formed by Ivan Palamà , Giuseppe Bianchi, Nicola Blefari Melazzi and Francesco Gringoli, published a research [2] that shows how cybercriminals can create and use and IMSI catcher for LTE systems using exclusively public domain software.
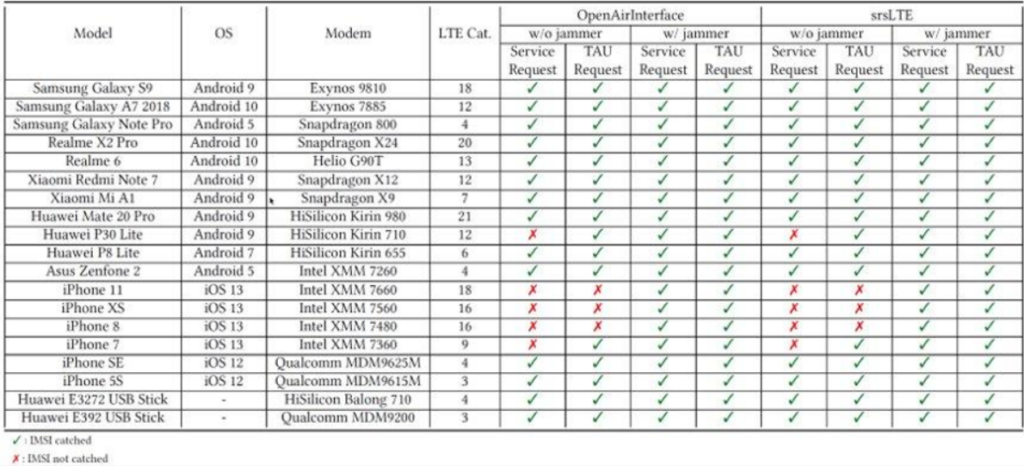
The goal of this paper is to assess how different User Terminals react to IMSI-catching attacks, namely location privacy attacks aiming at gathering the user's International Mobile Subscriber Identity (IMSI). After having implemented two different attack techniques over two different Software-Defined-Radio (SDR) platforms (OpenAirInterface and srsLTE), we have tested these attacks over different versions of the mobile phone brands, for a total of 19 different radio modems tested. We show that while the majority of devices surrender almost immediately, iPhones seem to implement some cleverness that resembles proper countermeasures. We also bring about evidence that the two chosen SDR platforms implement different signaling procedures that differentiate their ability as IMSI-catchers. We finally analyse IMSI-catchers' behaviors against subscribers of different operators, showing that successfulness of the attack depends only on the chipset and the SDR tool. We believe that our analysis may be useful either to practitioners that need to experiment with mobile security, as well as engineers for improving the design of mobile modems.
The research also shows how smartphones from different vendors may react to IMSI catching attacks. The team tested 19 smartphones of different brands and with different operating systems by analyzing the behavior of the devices when attacked by the IMSI Catcher, bringing to light different behaviors:
The results show a markedly distinct behavior in Android devices compared to iOS: iPhone 8 and later versions are not vulnerable to IMSI catching attack unless ajammer is used. Even when a jammers is used, the authors observed that such devices often switch to 3G or GSM instead of revealing their IMSI.