iLEAPP: an iOS logs, events, and plists parser
iLEAPP is a good iOS forensic tool developed by Alexis Brignoni. It’s composed by a set of python script previously developed by Alexis, collected in a single, useful, tool.
iLEAPP [1] is developed in order to help forensic analyst during the processing of iOS artifacts, and currently has this parsing capabilities:
- Mobile Installation Logs.
- Nested bplists inside a iOS KnowledgeC.db field.
- LastBuildInfo.plist
- IconState.plist
- iOS version 11, 12, & 13 Notifications content
- ApplicationState.db bundle ID to app GUID parsing and correlation.
- Cellular Wireless Information Plists
This parsing tasks can be performed on a full disk image, but also on a logical device acquisition.
Installation
First, clone the repository:
$ git clone https://github.com/abrignoni/iLEAPP
Then install tkinter:
$ sudo apt-get install python3-tk
Finally, install dependencies:
$ cd iLEAPP $ pip install -r requirements.txt
If running the binaries provided in the version releases [2] no dependencies are needed.
Usage
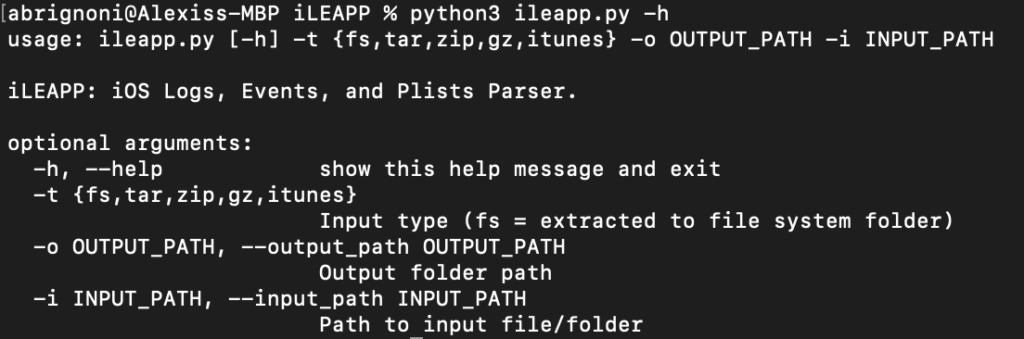
$ python ileapp.py -t <zip | tar | fs | gz | itunes> -i <path_to_extraction> -o <path_for_report_output>
For installation and usage on macOS, please refers to this useful video by 13cubed: