My Weekly Roundup #145
Cybersecurity
LemonDuck botnet plunders Docker cloud instances in cryptocurrency crime wave

Operators of the LemonDuck botnet are targeting Docker instances in a cryptocurrency mining campaign. LemonDuck is cryptocurrency mining malware wrapped up in a botnet structure.
Threat Assessment: BlackByte Ransomware
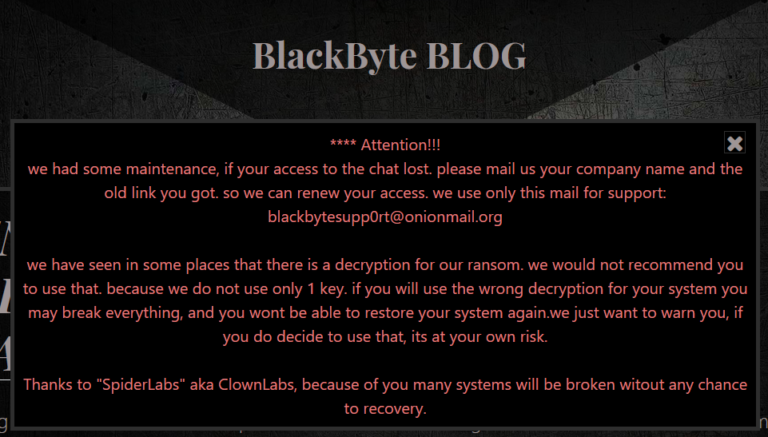
BlackByte is ransomware as a service (RaaS) that first emerged in July 2021. Operators have exploited ProxyShell vulnerabilities to gain a foothold in the victim’s environment. BlackByte has similarities to other ransomware variants such as Lockbit 2.
Spring4Shell Vulnerability CVE-2022-22965 Exploited to Deploy Cryptocurrency Miners

Among the exploitation attempts were ones aimed at deploying cryptocurrency miners. In this section, we look at how the malicious actors behind these exploitation attempts create a web shell to deploy their cryptocurrency miners.
Atlassian Drops Patches for Critical Jira Authentication Bypass Vulnerability

Atlassian has published a security advisory warning of a critical vulnerability in its Jira software that could be abused by a remote, unauthenticated attacker to circumvent authentication protections. Tracked as CVE-2022-0540, the flaw is rated 9.
QNAP warns of new bugs in its Network Attached Storage devices

QNAP, the makers of Networked Attached Storage (NAS) devices that are especially popular with home and small business users, has issued a warning about not-yet-patched bugs in the company’s products.
Leaked Chats Show LAPSUS$ Stole T-Mobile Source Code
KrebsOnSecurity recently reviewed a copy of the private chat messages between members of the LAPSUS$ cybercrime group in the week leading up to the arrest of its most active members last month.
REvil reborn? Notorious gang’s dark web site redirects to new ransomware operation

Sometimes referred to as Sodinokibi, the notorious REvil ransomware-as-a-service (RAAS) enterprise was responsible for a series of high profile attacks against the likes of the world’s biggest meat supplier JBS Foods and IT service firm Kaseya.
Conti ransomware claims responsibility for the attack on Costa Rica

Conti ransomware gang claimed responsibility for a ransomware attack that hit the government infrastructure of Costa Rica. Last week a ransomware attack has crippled the government infrastructure of Costa Rica causing chaos.
In a remote-work world, a zero-trust revolution is necessary

Last summer, law enforcement officials contacted both Apple and Meta, demanding customer data in “emergency data requests.” The companies complied. Unfortunately, the “officials” turned out to be hackers affiliated with a cyber-gang called “Recursion Team.”
T-Mobile confirms Lapsus$ hackers breached internal systems

T-Mobile has confirmed that the Lapsus$ extortion gang breached its network “several weeks ago” using stolen credentials and gained access to internal systems.
Technology
Pixel Watch prototype is left at a bar, gets photographed

The Pixel Watch had an iPhone 4 moment over the weekend. Just as Apple’s 2010 flagship leaked after being left at a bar, Google’s upcoming Pixel Watch was apparently lost and found at a restaurant.
The metaverse is a transformational opportunity for the business world

We are excited to bring Transform 2022 back in-person July 19 and virtually July 20 - 28. Join AI and data leaders for insightful talks and exciting networking opportunities. Register today! I first wrote the word metaverse on a whiteboard in October 2017.
2022 Sci-Fi Contest: Your Home Assistant, HAL 9000

Anyone who has seen 2001: A Space Odyssey will easily remember HAL 9000, the sentient computer that turned against its human companions aboard Spacecraft Discovery One. [Ben Brooks] decided to recreate the foreboding digital being, and put it to work as a smart home assistant.
ZX Spectrum Home Computer Turns 40

Today marks the 40th anniversary of a truly important date in computing history: the release of the ZX Spectrum. The Spectrum was by no means the first home computer. It wasn’t the first home computer that came pre-assembled in an affordable package.
The Glorious Utility of the Mid-Range Phone

We’re big fans of cheap phones here at WIRED. If you can do without all the beefed-up chips, six-pack cameras, and lidars of the $1,000 handsets, mid-range options get the job done for not a lot of cash. Sometimes you even get more from the cheaper phones, like an actual headphone jack.
Privacy
Internet spring cleaning: How to delete Instagram, Facebook and other accounts

So you’ve washed your sheets and vacuumed under the couch in the name of spring cleaning. But what about your online clutter? Apps that delight, inform and keep you connected deserve room in your digital space.
Entertainment
New Monkey Island Game: Yes To Hints, No To Pixel Art

Return to Monkey Island will have modern graphics and a hint system. Creator Rob Gilbert has explained that he’s had some major rethinks over what he calls a “new” Monkey Island game rather than “another” game in the series.
‘Do We Have the Game All Wrong?’: Natasha Lyonne’s Cosmic Journey Into ‘Russian Doll’ Season 2

“I’m deeply cracked from a combination of Talmud and LSD,” says Natasha Lyonne, flicking a cigarette in her hand from the couch of her Los Angeles home, where she’s been chatting by Zoom for over an hour.