My Weekly Roundup #152
Cybersecurity
Multi-factor Authentication In-The-Wild bypass methods

Two-factor authentication (2FA) or multi-factor authentication ( MFA ) is a method to authenticate through a service that requires at least two proofs of recognition.
PACMAN M1 chip attack defeats ‘the last line of security’ – but requires physical access

When designing the M1 chip, Apple created various layers of security, each designed to protect against an attacker who succeeded in penetrating the previous ones. Its final layer is a security feature known as PAC – and this has now been defeated …
Symbiote: A New, Nearly-Impossible-to-Detect Linux Threat

This research is a joint effort between Joakim Kennedy, Security Researcher at Intezer, and the BlackBerry Research & Intelligence Team. It can be found on the Intezer blog here as well. In biology, a symbiote is an organism that lives in symbiosis with another organism.
SSNDOB Shutdown: DOJ Announces Closure of Darknet Market Selling Social Security Numbers and Other Personally Identifiable Information

Today, the U.S. Department of Justice (DOJ) announced the shutdown of SSNDOB, a marketplace that sold personally identifiable information (PII) of victims around the world on both the darknet and clearnet, following an investigation by IRS-Criminal Investigation and the FBI.
EU working on possible ban on providing cloud services to Russia - source
/cloudfront-us-east-2.images.arcpublishing.com/reuters/W7CYDGM5Y5KP7AZFDMM3QRLABM.jpg)
BRUSSELS, June 8 (Reuters) - The European Union is working on a possible ban on the provision of cloud services to Russia as part of new sanctions against the Kremlin for the invasion of Ukraine, an EU official told Reuters on Wednesday, noting the measure was technically complex.
Cloudflare announces Private Access Tokens - verification without CAPTCHAs

Cloudflare has announced a new technology called Private Access Tokens that allow you to validate visitors to your site are real, in a private manner.
Technology
DOOM? In Your BIOS? More Likely Than You Think!
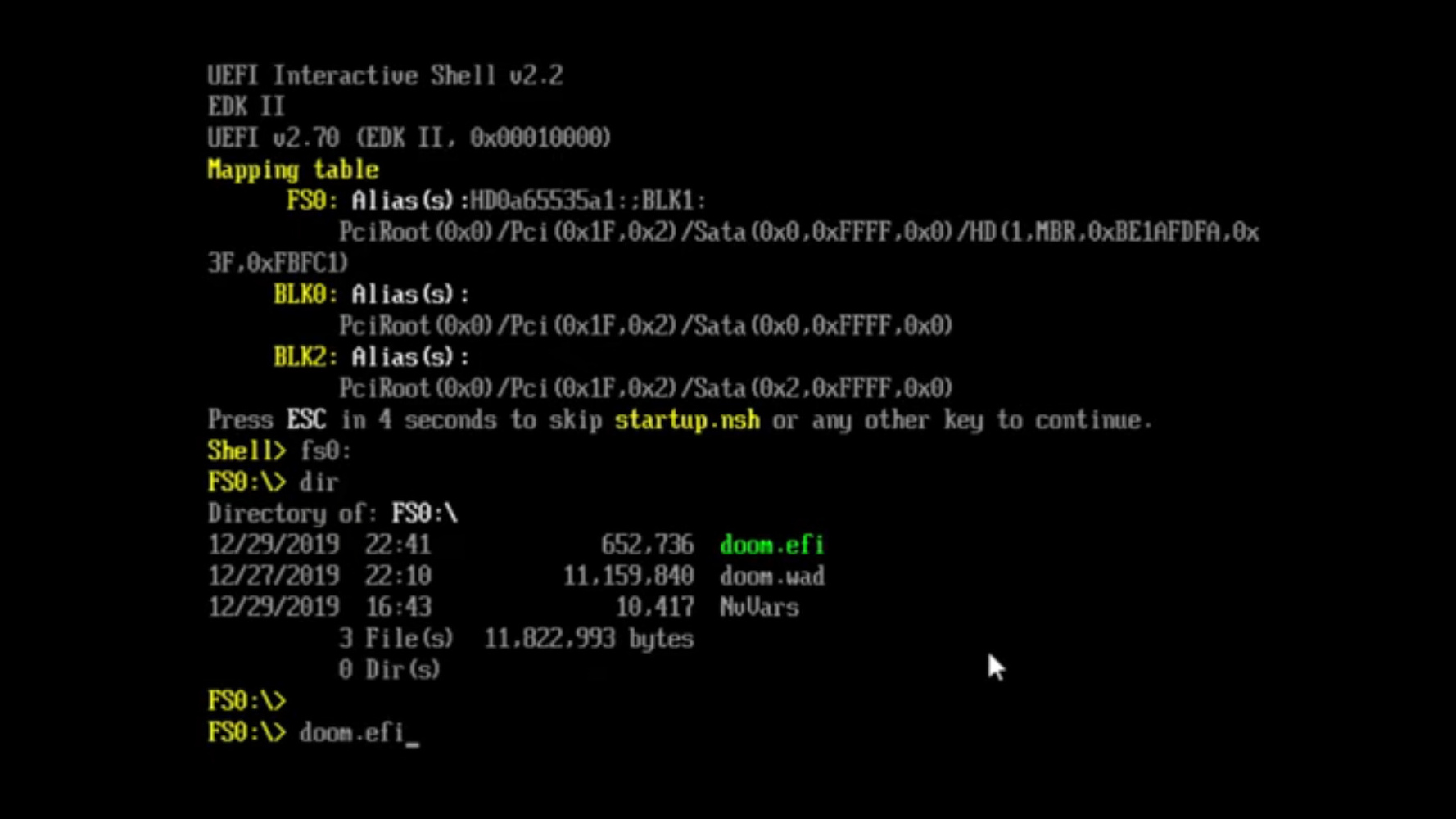
We’ve seen hackers run DOOM on a variety of appliances, from desk phones to pregnancy tests. Now, the final frontier has been conquered – we got DOOM to run on an x86 machine. Of course, making sure we utilize your PC hardware to its fullest, we have to forego an OS.
Apple tweaks third-party dating app payment rules to comply with Dutch regulator’s order
Apple has announced a handful of changes to its rules related to dating app payments in order to comply with orders from the Netherlands Authority for Consumers and Markets (ACM).
Meta Facing 8 Lawsuits That Allege Its Addictive Algorithms Harm Young Users

Meta, the parent company of Facebook and Instagram, is facing a slew of lawsuits alleging the company hasn’t done enough to prevent psychological harm to its young users and is exploiting them for profit.
An AI chatbot trained on 4chan has sparked outrage and fascination

Writer at Neural by TNW — Thomas covers AI in all its iterations. Likes Werner Herzog films and Arsenal FC.
PyScript: Python In The Web Browser
A chainsaw can make short work of clearing out the back forty. It can also make a good horror movie. So while some people will say we don’t need another tool to allow more malicious scripting in the browser, we also know that, like any tool, you can use it or abuse it.
iPadOS 16’s new multitasking feature won’t work on most iPads

Reports that preceded this week’s WWDC 2022 press conference claimed that Apple would introduce a new iPad multitasking system that mimics the multitasking experience on laptops and desktops.
NASA plans to explore the hellish atmosphere of Venus

NASA has big plans to explore Venus within the next 10 years. Last week, the space agency shared details about its Deep Atmosphere Venus Investigation of Noble Gases, Chemistry, and Imaging (DAVINCI) probe. The probe is scheduled to launch in June of 2029.
Apple Pimps Lock Screen For iOS16

Apple has unveiled a series of changes with iOS 16. It’s largely about personalization though there’s a surprise financial change. The new system will support the iPhone 8 and later, along with most iPad models released from 2017 on.
Privacy
WiFi probing exposes smartphone users to tracking, info leaks

Researchers at the University of Hamburg in Germany have conducted a field experiment capturing hundreds of thousands of passersby’s WiFi connection probe requests to determine the type of data transmitted without the device owners realizing it.
Firefox and Chrome are squaring off over ad-blocker extensions

There’s a growing split over how much room browsers should leave for ad blocking — and Chrome and Firefox have ended up on opposite sides of the fight.
How a Saxophonist Tricked the KGB by Encrypting Secrets in Music

In 1985, saxophonist Merryl Goldberg found herself on a plane to Moscow with three fellow musicians from the Boston Klezmer Conservatory Band. She had carefully packed sheet music, reeds, and other woodwind supplies, along with a soprano saxophone, to bring into the USSR.
Entertainment
Darth Vader Takes a Break From Obi-Wan Kenobi to Sulk in Times Square

A few months ago Lucasfilm teamed with LG to shift Boba Fett’s throne all the way from Tatooine to Manhattan—virtually at least, for a 3D-effect billboard promoting The Book of Boba Fett in the heart of Times Square.
Music
Twin Peaks’ Angelo Badalamenti and Julee Cruise on the creation of the show’s timeless theme music

How Julee Cruise’s haunting and glacial theme song set the tone for David Lynch’s off-kilter TV series. Originally published in Uncut’s June 2017 issue.