My Weekly Roundup #155
Cybersecurity
Rogue HackerOne employee steals bug reports to sell on the side

A HackerOne employee stole vulnerability reports submitted through the bug bounty platform and disclosed them to affected customers to claim financial rewards.
Facebook 2FA phish arrives just 28 minutes after scam domain created

We’ll tell this story primarily through the medium of images, because a picture is worth 1024 words. As you can see, the link in the email, highlighted in blue by our Oulook email client, appears to go directly and correctly to the facebook.com domain.
AstraLocker 2.0 ransomware isn’t going to give you your files back

Reversing Labs reports that the latest verison of AstraLocker ransomware is engaged in a a so-called “smash and grab” ransomware operation. Smash and grab is all about maxing out profit in the fastest time.
Phishing QR-code attack on QQ users

Folks today are generally mostly aware that clicking links from questionable sources, for example in e-mails, isn’t a good idea. However, when it comes to scanning QR codes, people are often much less vigilant.
Hacking the Crypto-monetized Web

The web is several decades old. But it largely still relies on the same method of monetization as it always has: advertising. However, things are changing thanks to the power of cryptocurrency and blockchain. It’s what Trend Micro has coined the “crypto-monetized web” (CMW).
Black Basta ransomware – what you need to know

What is Black Basta? Black Basta is a relatively new family of ransomware, first discovered in April 2022.
Toll fraud malware: How an Android application can drain your wallet

Toll fraud malware, a subcategory of billing fraud in which malicious applications subscribe users to premium services without their knowledge or consent, is one of the most prevalent types of Android malware – and it continues to evolve.
North Korea’s Lazarus Group Suspected of $100m Harmony Hack

Blockchain analytics company Elliptic suggested North Korea’s Lazarus Group may be behind last week’s $100m theft from cryptocurrency firm Harmony.
Bronze Starlight uses loader malware to deploy ransomware

Bronze Starlight, a Chinese APT, is deploying ransomware LockFile, AtomSilo, Rook, Night Sky, and Pandora via the HUI loader malware to carry out double extortion.
Ex-Canadian government employee admits to being a member of the Russian cybercrime gang NetWalker

A former Canadian government IT worker admitted to being a high-level member of the Russian cybercrime group NetWalker. A former Canadian government employee, Sebastien Vachon-Desjardins, pleaded guilty in the U.S. to charges related to his involvement with the Russian cybercrime group NetWalker.
The SessionManager IIS backdoor: a possibly overlooked GELSEMIUM artefact

Following on from our earlier Owowa discovery, we continued to hunt for more backdoors potentially set up as malicious modules within IIS, a popular web server edited by Microsoft. And we didn’t come back empty-handed…
Smash-and-grab: AstraLocker 2.0 pushes ransomware direct from Office docs

Joseph Edwards, Senior Malware Researcher at ReversingLabs. ReversingLabs recently discovered instances of the AstraLocker 2.0 malware distributed directly from Microsoft Word files used in phishing attacks.
Black Basta Ransomware Operators Expand Their Attack Arsenal With QakBot Trojan and PrintNightmare Exploit

We look into a recent attack orchestrated by the Black Basta ransomware ransomware group that used the banking trojan QakBot as a means of entry and movement and took advantage of the PrintNightmare vulnerability to perform privileged file operations.
OpenSea discloses data breach, warns users of phishing attacks

OpenSea, the largest non-fungible token (NFT) marketplace, disclosed a data breach on Wednesday and warned users of phishing attacks that could target them in the coming days. The online NFT marketplace says it has more than 600,000 users and a transaction volume that surpassed $20 billion.
Atlassian Confluence OGNL Injection Remote Code Execution (RCE) Vulnerability (CVE-2022-26134)
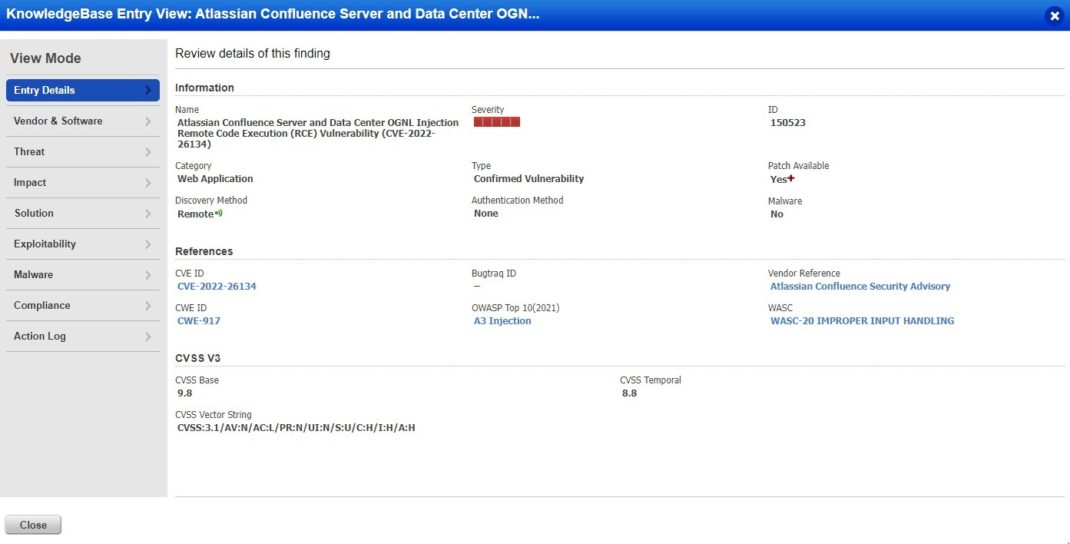
On June 02, 2022, Atlassian published a security advisory about a critical severity Unauthenticated Remote Code Execution vulnerability affecting Confluence Server and Data Center.
Israel plans ‘Cyber-Dome’ to defeat digital attacks from Iran and others

The new head of Israel’s National Cyber Directorate (INCD) has announced the nation intends to build a “Cyber-Dome” – a national defense system to fend off digital attacks.
AMD investigates RansomHouse hack claims, theft of 450GB data

Semiconductor giant AMD says they are investigating a cyberattack after the RansomHouse gang claimed to have stolen 450 GB of data from the company last year.
De-anonymizing ransomware domains on the dark web
We have developed three techniques to identify ransomware operators’ dark websites hosted on public IP addresses, allowing us to uncover previously unknown infrastructure for the DarkAngels, Snatch, Quantum and Nokoyawa ransomware groups.
Russian hacking group takes credit for wide-ranging cyberattack on Lithuania

A hacking group aligned with the Russian government took credit for a large cyberattack on several government institutions in Lithuania on Monday.
Conti vs. LockBit: A Comparative Analysis of Ransomware Groups

These characteristics visible from the data can be examined in greater depth by matching them with information provided by different threat intelligence sources. Conti, for example, has vowed not to target Russia’s allies, such as former Soviet Union countries and China.
Revive: from spyware to Android banking trojan

As in the majority of cases, Revive uses different Social Engineering techniques to appear as a legitimate app in order to mislead the victims. In fact, the malware is delivered through a phishing page and it hides behind a new 2FA app of the targeted bank.
Fake Copyright Emails Used to Deploy LockBit Ransomware
The LockBit ransomware is a kind of malicious software that is aimed to prevent users’ access to computer systems in return for a ransom payment.
Technology
The GPU shortage is over

If you buy something from a Verge link, Vox Media may earn a commission. See our ethics statement. For nearly two years, you’ve had to be incredibly lucky, skilled, or patient to get an Nvidia or AMD graphics card at MSRP.
Copilot works so well because it steals open source code and strips credit
Tristan is a futurist covering human-centric artificial intelligence advances, quantum computing, STEM, physics, and space stuff.
How quantum batteries could lead to million-mile EVs

Tristan is a futurist covering human-centric artificial intelligence advances, quantum computing, STEM, physics, and space stuff.
Hacked Tesla Model S Plaid breaks speed record, goes 216 mph

If you thought Tesla Model S Plaid was fast at its official top speed of 175 miles per hour, you haven’t seen anything yet.
Updated timeline for the new integrated view for Gmail

Beginning today, we are rolling out the opt-out experience to a segment of Gmail users. This means that select users will see the new Gmail experience by default, but they will still have the option to revert to classic Gmail via the settings menu.
Privacy
TikTok Confirms Some China-Based Employees Can Access US User Data
For more than one decade, Kurt Wimmer was this blog and this blogger’s First Amendment defender, representing me pro bono.
New Ipandetec’s Report Features ISPs’ Privacy Best Practices and Flaws in Panamá

Panamá’s mobile internet service providers have improved their commitments to transparency and user privacy, according to the new edition of IPANDETEC’s ¿Quien Defiende Tus Datos? (“Who Defends Your Data?”) report.
Canada’s national police force admits use of spyware to hack phones
In a “remarkable” disclosure, Canada’s national police force has described for the first time how it uses spyware to infiltrate mobile devices and collect data, including by remotely turning on the camera and microphone of a suspect’s phone or laptop.
Italian Garante Bans Google Analytics

On June 23, 2022, Italy’s data protection authority (the “Garante”) determined that a website’s use of the audience measurement tool Google Analytics is not compliant with the EU General Data Protection Regulation (“GDPR”), as the tool transfers personal data to the United States, which
TikTok Quietly Updated Privacy Policy to Collect Faceprints and Voiceprints

TikTok, one of the most downloaded apps of 2021 so far, decided to quietly update its privacy policy to collect biometric identifiers and biometric information know in the US as faceprints and voiceprints.
Drunk worker loses USB stick containing details of every resident of his city

It’s all too easy to imagine. After a hard day at work, you head off with some mates into the city. Maybe you stop at a bar. Possibly you have a few drinks. Perhaps you hit the dance floor.
Entertainment
‘Thor: Love and Thunder’ cast playing Spin The Hammer results in total chaos

When Jimmy Kimmel’s colleague Guillermo is interviewing celebrities you know there’s going to be tequila involved — but in this game of “Spin the Hammer” with the cast of Thor: Love and Thunder above, there’s so much more besides.
