My Weekly Roundup #157
A selection of interesting news published during this week on news.andreafortuna.org.
Cybersecurity
Above the Fold and in Your Inbox: Tracing State-Aligned Activity Targeting Journalists, Media

Key Takeaways Those involved in media make for appealing targets given the unique access, information, and insights they can provide on topics of state-designated import.
INJ3CTOR3 Operation – Leveraging Asterisk Servers for Monetization

Recently, Check Point Research encountered a series of worldwide attacks relevant to VoIP, specifically to Session initiation Protocol (SIP) servers. Based on information provided by our global sensors, there appears to be a systematic exploitation pattern of SIP servers from different manufactures.
Google Removes “App Permissions” List from Play Store for New “Data Safety” Section

Following the launch of a new “Data safety” section for the Android app on the Play Store, Google appears to be readying to remove the app permissions list from both the mobile app and the web. The change was highlighted by Esper’s Mishaal Rahman earlier this week.
Threats Making WAVs - Incident Response to a Cryptomining Attack

The attack was cleaned by removing the malware, terminating the malicious processes and deleting the registry keys containing the binary payloads. Soon after these steps, all indicators of compromise (blue screens, suspicious network communication, Powershell processes, etc.) ceased to appear.
Top 5 Infrastructure as Code Security Challenges

Infrastructure as code (IaC), an essential component of contemporary software, enables developers to spin up software infrastructure while offering systems the ability to grow in a flexible and on-demand manner.
Digium Phones Under Attack: Insight Into the Web Shell Implant
Installing a web shell on a web server is a common approach malware authors take to launch exploits or run commands remotely. In November 2020, the INJ3CTOR3 operation targeted the Sangoma PBX, a popular VoIP PBX system, by installing a web shell on its web server.
Windows Network File System flaw results in arbitrary code execution as SYSTEM
Trend Micro Research has published an anatomy of a Windows remote code execution vulnerability lurking in the Network File System.
New PayPal Phishing Kit Hijacks WordPress Sites

Researchers have uncovered a new phishing kit that, under the guise of security controls, injects malware into legitimate WordPress sites and uses a fake PayPal-branded social engineering scam to trick targets into handing over their most sensitive data.
Inside The Russian Cybergang Thought To Be Attacking Ukraine—The Trickbot Leaks

Reports concerning the impact of cyber operations, directed at both Russian and Ukrainian targets, have been many and varied.
Mantis Botnet Behind the Largest HTTPS DDoS Attack on Over 3000 Cloudflare Customers
The botnet behind the largest HTTPS distributed denial-of-service (DDoS) attack in June 2022 has been linked to a spate of attacks aimed at nearly 1,000 Cloudflare customers.
North Korean threat actor targets small and midsize businesses with H0lyGh0st ransomware

A group of actors originating from North Korea that Microsoft Threat Intelligence Center (MSTIC) tracks as DEV-0530 has been developing and using ransomware in attacks since June 2021.
Targeted Attack on Government Agencies
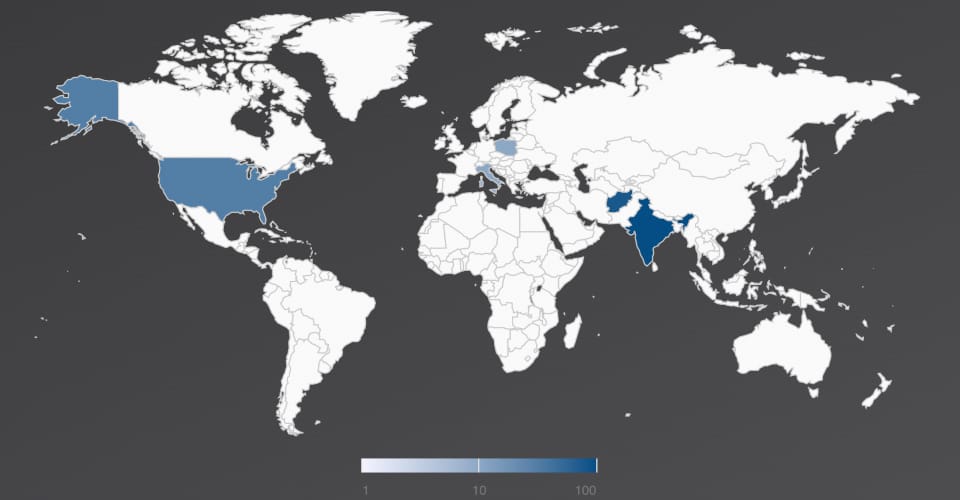
The Trellix Email Security Research Team has discovered a malicious campaign targeting government agencies of Afghanistan, India, Italy, Poland, and the United States since 2021. The attack starts with a spear phishing email with a geo-political theme.
First Cyber Safety Review Board report finds Log4j has become an ‘endemic vulnerability’

The flaw uncovered late last year in the widely-used Log4j Java library will remain a danger for many years to come, the independent body charged with investigating the global incident said Thursday.
Transparent Tribe begins targeting education sector in latest campaign

Cisco Talos has been tracking a new malicious campaign operated by the Transparent Tribe APT group. This campaign involves the targeting of educational institutions and students in the Indian subcontinent, a deviation from the adversary’s typical focus on government entities.
New Lilith ransomware emerges with extortion site, lists first victim

A new ransomware operation has been launched under the name ‘Lilith,’ and it has already posted its first victim on a data leak site created to support double-extortion attacks. Lilith is a C/C++ console-based ransomware discovered by JAMESWT and designed for 64-bit versions of Windows.
New UEFI firmware flaws impact over 70 Lenovo laptop models

The UEFI firmware used in several laptops made by Lenovo is vulnerable to three buffer overflow vulnerabilities that could enable attackers to hijack the startup routine of Windows installations.
Uncovering a macOS App Sandbox escape vulnerability: A deep dive into CVE-2022-26706

Microsoft uncovered a vulnerability in macOS that could allow specially crafted codes to “escape” the App Sandbox and run unrestricted on the system.
Cobalt Strikes again: UAC-0056 continues to target Ukraine in its latest campaign

The Malwarebytes Threat Intelligence team recently reviewed a series of cyber attacks against Ukraine that we attribute with high confidence to UAC-0056 (AKA UNC2589, TA471).
New 0Day Hack Attack Alert Issued For All Windows Users
With 84 security issues requiring fixing, Microsoft’s monthly Patch Tuesday patch rollout is upon us. While only four of these security vulnerabilities are classified by Microsoft as critical in nature, one does stand out for requiring your most urgent attention.
Rise in Qakbot attacks traced to evolving threat techniques

Active since 2008, Qakbot, also known as QBot, QuackBot and Pinkslipbot, is a common trojan malware designed to steal passwords. This pervasive threat spreads using an email-driven botnet that inserts replies in active email threads.
BlackCat Ransomware group implements quadruple extortion

The BlackCat ransomware group performs quadruple extortion techniques to pressurize victims in order to pay ransom. Recently, the ransomware group has raised its stakes up to $2.5M in demands.
From cookie theft to BEC: Attackers use AiTM phishing sites as entry point to further financial fraud

A large-scale phishing campaign that used adversary-in-the-middle (AiTM) phishing sites stole passwords, hijacked a user’s sign-in session, and skipped the authentication process even if the user had enabled multifactor authentication (MFA).
Callback Phishing Campaigns Impersonate CrowdStrike, Other Cybersecurity Companies

On July 8, 2022, CrowdStrike Intelligence identified a callback phishing campaign impersonating prominent cybersecurity companies, including CrowdStrike. The phishing email implies the recipient’s company has been breached and insists the victim call the included phone number.
ChromeLoader: New Stubborn Malware Campaign

In January 2022, a new browser hijacker/adware campaign named ChromeLoader (also known as Choziosi Loader and ChromeBack) was discovered. Despite using simple malicious advertisements, the malware became widespread, potentially leaking data from thousands of users and organizations.
TikTok Postpones Privacy Policy Update in Europe After Italy Warns of GDPR Breach

Popular video-sharing platform TikTok on Tuesday agreed to pause a controversial privacy policy update that could have allowed it to serve targeted ads based on users’ activity on the social video platform without their permission to do so.
‘Callback’ Phishing Campaign Impersonates Security Firms

Victims instructed to make a phone call that will direct them to a link for downloading malware.
‘Luna Moth’ Group Ransoms Data Without the Ransomware

A little social engineering and commercially available remote administration tools (RATs) and other software are all the new Luna Moth ransom group has needed to infiltrate victims’ systems and extort payments.
Technology
Operation 404 Hit So Many Piracy Apps It’s Surprising There Are Any Left

Last month anti-piracy initiative ‘Operation 404’ reportedly took down 226 websites and 461 piracy apps, a huge amount by any standard. With the dust settling this week, anti-piracy company Nagra provided more information on its role in the operation.
It’s ChromeOS now, not Chrome OS

Chrome OS, Google’s Linux-based operating system for its Chromebook devices, has been around for more than a decade, but the company has made a small but notable branding change: it’s now called ChromeOS, with no space in between.
Privacy
The difference between pseudonymity and anonymity: When zero is more

We are excited to bring Transform 2022 back in-person July 19 and virtually July 20 - 28. Join AI and data leaders for insightful talks and exciting networking opportunities. Register today!
Amazon Gave Ring Doorbell Camera Footage To Police Without Consent

Amazon, the online retail giant, has confirmed handing over Ring doorbell camera footage to law enforcement at least eleven times so far this year without a search warrant or the knowledge of the owner, according to a disclosure shared by U.S. Senator Ed Markey on Wednesday.
Entertainment
Netflix’s ‘Resident Evil’ Is Gossip Girl With Zombies

Fans of the video game series Resident Evil will most likely not enjoy Netflix’s series of the same name. If you wish CW shows like Roswell involved more chainsaws, however, you might dig it. Resident Evil as a series has had a complicated relationship to the medium of film.
Amazing Cover of Thunderstruck on a 21-String Chinese Guzheng [Video]

Check out this amazing cover of AC/DC’s Thunderstruck performed on a 21-string Chinese Guzheng by Moyun.
Music
10 bands who didn’t let the death of a key member stop them reuniting

Nothing stops rock’n’roll, not even death. Over the years, countless bands have reunited despite the demise of one or more key members – some with more success than others.
Axl Rose Dedicates Shows to Taylor Hawkins, Blasts Vladimir Putin in Tour Message

Axl Rose capped off Guns N’ Roses‘ European tour with a note on Twitter in which he thanked fans for their support, dedicated the band’s trek to the late Taylor Hawkins and slammed “murderous little man” Vladimir Putin — all in just a few paragraphs.
Watch the Rolling Stones Play ‘You Can’t Always Get What You Want’ With Ukrainian Choir

The Rolling Stones brought out a Ukrainian choir to join them for a special performance of “You Can’t Always Get What You Want” near the end of their concert Friday night at Vienna, Austria’s Ernst Happel Stadium to show their solidarity with the embattled nation.
Metallica’s Master of Puppets conjures UK Top 40 hit thanks to Stranger Things

First there was Kate Bush, scoring a No 1 hit with Running Up That Hill 37 years after it was released. Now, the supernatural power of Stranger Things to resurrect old hits continues, giving Metallica their first UK Top 40 hit since 2008.
10 killer performances from metal bands in Hollywood movies

Hollywood and heavy metal have never had the best relationship. For every film that gets what the genre’s all about, there are a dozen that paint its artists and fans as doofuses and/or devil worshippers.
Is Taylor Swift’s ‘Red (Taylor’s Version)’ Eligible for Grammy Nods? We Have the Answer

There has been some uncertainty about whether Taylor Swift’s Red (Taylor’s Version) will be eligible for the 65th annual Grammy Awards. The album, if eligible, would be a strong contender for nominations for both album of the year and best country album.
King Crimson’s Robert Fripp Sets Fall Release for Band Doc. But Another Tour? ‘Only to Prevent World War III’

In the universe of King Crimson, one of rock’s most challenging art-prog bands, nothing was ever easy: personnel changed as often as time signatures.