My Weekly Roundup #158
Cybersecurity
Reverse Image Search Guide #osint
The tool I recommend you start your search with is Yandex Images. Not only does it search very well for similar images, but it also recognizes the text on them and identifies the location if it is an image of a famous landmark.
The Return of Candiru: Zero-days in the Middle East

We recently discovered a zero-day vulnerability in Google Chrome (CVE-2022-2294) when it was exploited in the wild in an attempt to attack Avast users in the Middle East. Specifically, a large portion of the attacks took place in Lebanon, where journalists were among the targeted parties.
Qakbot Resurfaces with new Playbook

During a routine threat-hunting exercise, Cyble Research Labs came across a Twitter post wherein a researcher shared new IoCs related to the infamous Qakbot malware. For initial infection, Qakbot uses an email mass spamming campaign.
Redeemer Ransomware back Action

Cyble Research Labs has constantly been tracking emerging threats as well as their delivery mechanisms from Ransomware groups, RATs, etc. During a routine threat-hunting exercise, we came across the latest version of Redeemer ransomware on darkweb cybercrime forums.
Senators intro bill to foster federal move to quantum-resistant technology

A bipartisan pair of senators on Thursday introduced legislation to motivate federal agencies to shift their information systems to quantum-resistant cryptography. The Quantum Computing Cybersecurity Preparedness Act by Sens. Maggie Hassan (D-N.H.
Attackers target Ukraine using GoMet backdoor

Executive summary Since the Russian invasion of Ukraine began, Ukrainians have been under a nearly constant barrage of cyber attacks.
LockBit 3.0 Update | Unpicking the Ransomware’s Latest Anti-Analysis and Evasion Techniques

LockBit 3.0 ransomware (aka LockBit Black) is an evolution of the prolific LockBit ransomware-as-a-service (RaaS) family, which has roots that extend back to BlackMatter and related entities. After critical bugs were discovered in LockBit 2.
Ten process injection techniques: A technical survey of common and trending process injection techniques
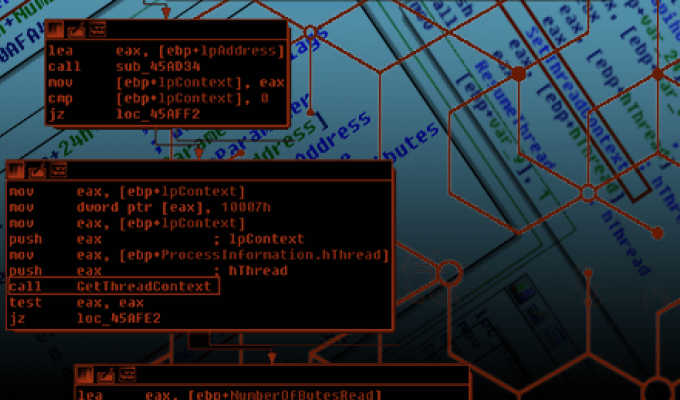
Process injection is a widespread defense evasion technique employed often within malware and fileless adversary tradecraft, and entails running custom code within the address space of another process. Process injection improves stealth, and some techniques also achieve persistence.
Il magico mondo dei malware

Cos’è un malware e in che categorie possiamo dividerli? Ad oggi con malware intendiamo un programma con intenzioni malevole nei nostri confronti, o meglio nei confronti dei nostri dispositivi.
Lightning Framework: New Undetected “Swiss Army Knife” Linux Malware ⚡
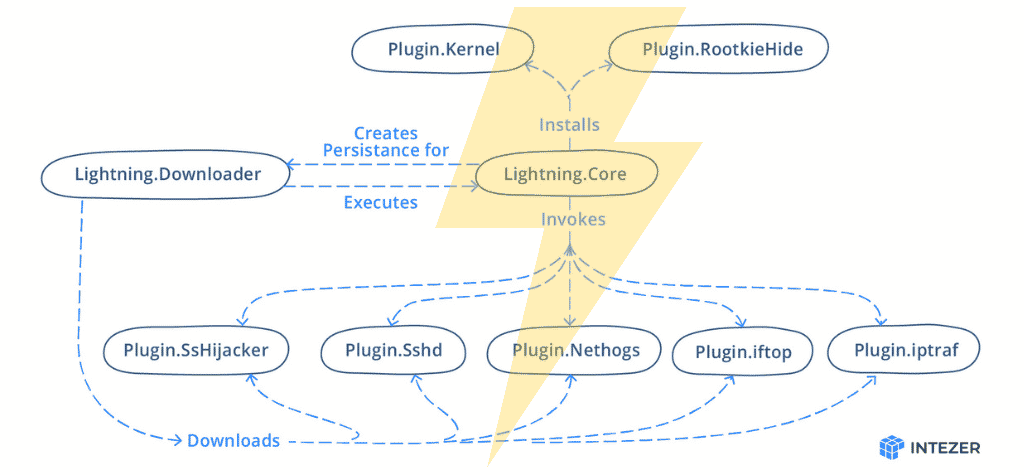
Lightning Framework is a new undetected Swiss Army Knife-like Linux malware that has modular plugins and the ability to install rootkits. Year after year Linux environments increasingly become the target of malware due to continued threat actor interest in the space.
Unit 42 Threat Group Naming Update

What’s in a Name? One of the complex aspects of working in cyber threat intelligence is how we identify the various elements of an attack campaign we are tracking. We give names to malware families, attack techniques, intrusion sets and even vulnerabilities.
Unpatched flaws in popular GPS devices could let hackers disrupt and track vehicles

Flaws discovered in a GPS device used in fleet management could allow attackers to remotely disrupt operations and surveil vehicle movements, the U.S. Cybersecurity and Infrastructure Security Agency (CISA) and security firm BitSight warned Tuesday.
Continued cyber activity in Eastern Europe observed by TAG

Google’s Threat Analysis Group (TAG) continues to closely monitor the cybersecurity environment in Eastern Europe with regard to the war in Ukraine.
Russian APT29 Hackers Use Online Storage Services, DropBox and Google Drive
Organizations around the world rely on the use of trusted, reliable online storage services – such as DropBox and Google Drive – to conduct day-to-day operations.
Air-gapped systems leak data via SATA cable WiFi antennas
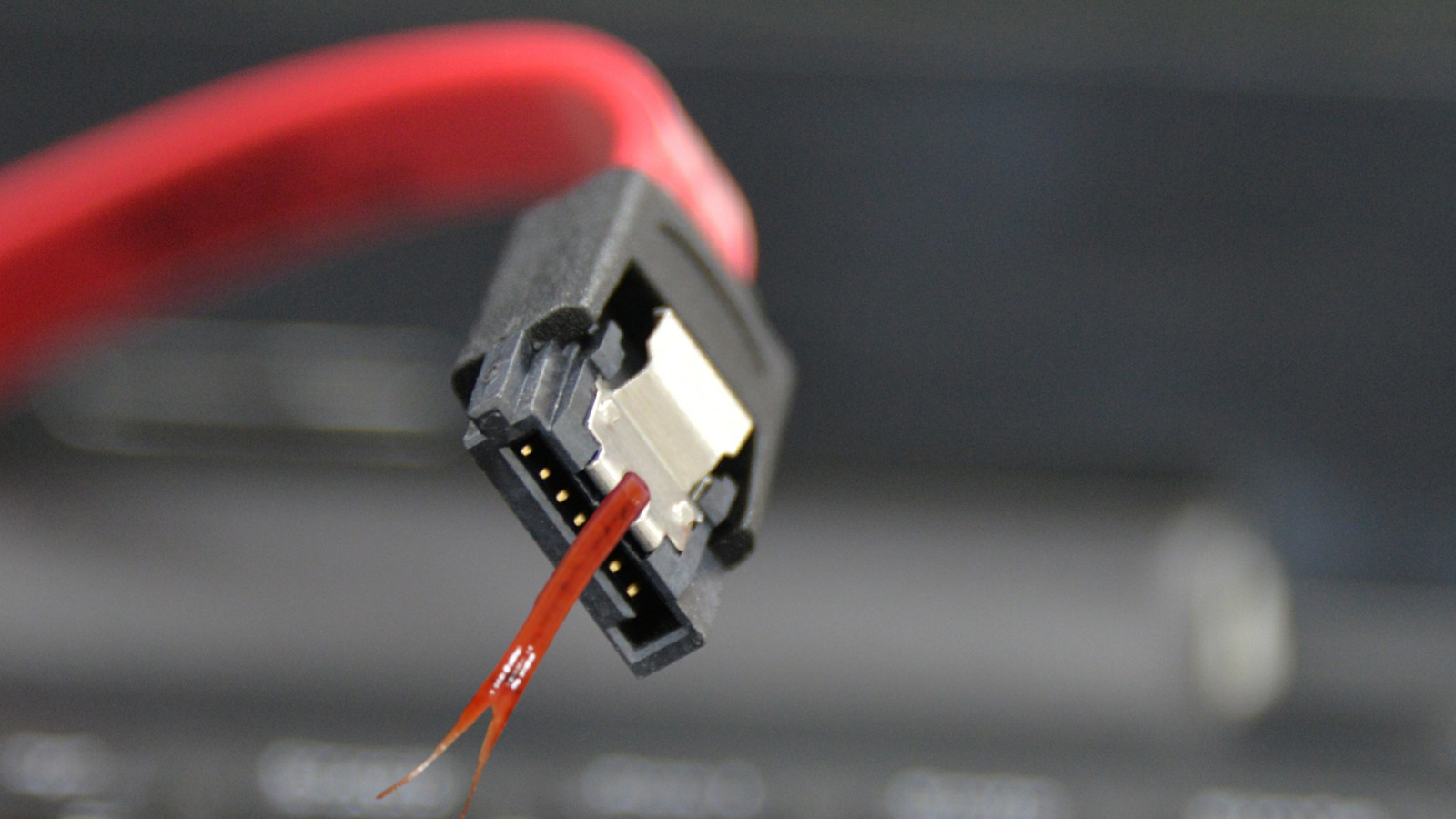
A security researcher has found a new way to steal data from air-gapped systems by using serial ATA (SATA) cables present inside most computers as a wireless antenna that sends out data via radio signals.
I see what you did there: A look at the CloudMensis macOS spyware

Previously unknown macOS malware uses cloud storage as its C&C channel and to exfiltrate documents, keystrokes, and screen captures from compromised Macs In April 2022, ESET researchers discovered a previously unknown macOS backdoor that spies on users of the compromised Mac and exclusively uses pu
Ongoing Roaming Mantis smishing campaign targeting France

This blog post on Roaming Mantis group is an extract of the “FLINT 2022-037 – Ongoing Roaming Mantis smishing campaign targeting France” report (SEKOIA.IO Flash Intelligence) sent to our clients on July 07, 2022. On July 4, 2022, a SEKOIA.
Technology
Google fires software engineer who claims AI chatbot is sentient

Google has dismissed a senior software engineer who claimed the company’s artificial intelligence chatbot LaMDA was a self-aware person.
Le case discografiche in Italia agiscono con successo contro CloudFlare

IFPI, l’organizzazione che rappresenta l’industria discografica nel mondo, ha coordinato l’azione intrapresa con successo contro CloudFlare da parte delle aziende associate in Italia (Sony Music Entertainment Italy s.p.a., Universal Music Entertainment Italy s.r.l., Warner Music Italia s.r.l.).
Privacy
Police Are Still Abusing Investigative Exemptions to Shield Surveillance Tech, While Others Move Towards Transparency

How transparent are police about surveillance technology? It depends on where you look.
ChromeOS has a test tool for Chromebook privacy from snooping
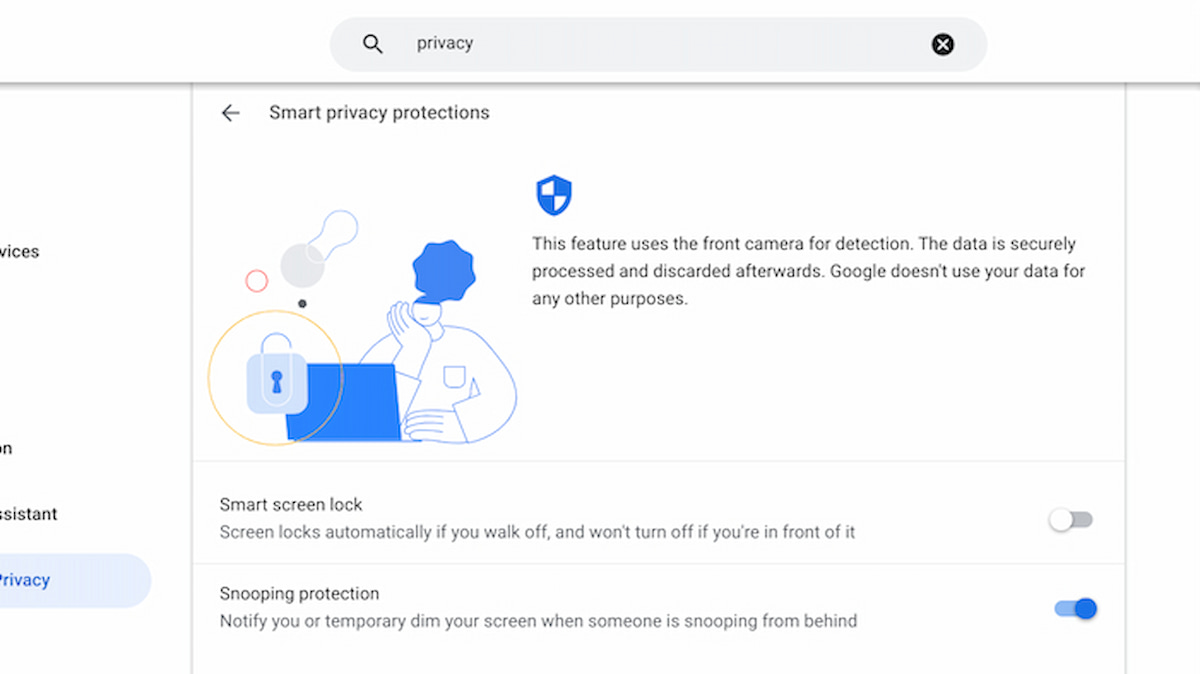
Back in December, I called attention to a new Chromebook privacy effort that detects when someone behind you is snooping on your laptop. The feature is still in the works so don’t go looking for it just yet.
Pegasus Spyware Used Against Thailand’s Pro-Democracy Movement

Key Findings We discovered an extensive espionage campaign targeting Thai pro-democracy protesters, and activists calling for reforms to the monarchy. We forensically confirmed that at least 30 individuals were infected with NSO Group’s Pegasus spyware.
Music
Ozzy Osbourne says he once thought Eric Clapton was stalking him around Los Angeles

Ozzy Osbourne has revealed that he was under the impression that Eric Clapton was tracking him around Los Angeles many years ago.
Official Dio documentary set for release at the end of the summer

The official Ronnie James Dio documentary, DIO: Dreamers Never Die, will be officially released at the end of the summer. The late vocalist’s wife and manager Wendy Dio revealed the news during an interview on Iowa radio station Lazer 103.3.
The 10 best metal covers of Queen songs

One of the many brilliant things about Queen was that they could do everything. Epic hard rock anthems, slick pop gems, grandstanding ballads, sweaty disco-funk workouts, playful ragtime jazz, batshit crazy operatic bombast – it was all in the mix.