Windows 10 administrator password recovery
Time ago I have had to perform memory capture on a Windows 10 system that was infected with malware but whose administrator password had been lost. “Fortunately,”, the malware had gained a fair amount of persistence and was able to survive reboots comfortably: the need in that case was to obtain an image of the memory of the infected system, and then analyze it for the purpose of integrating the results of the malware analysis. So, in that case I chose to change the Administrator password by a “quick-and-dirty” method, which I outline below.
-
Insert the Windows 10 installation media into a USB key. To do this, go to this page, click on Download the tool now and then prepare a bootable USB key with the Windows 10 installation files.
-
Boot the system from that media.
-
When the screen for choosing language and keyboard layout appears, press SHIFT + F10 to bring up the command prompt.
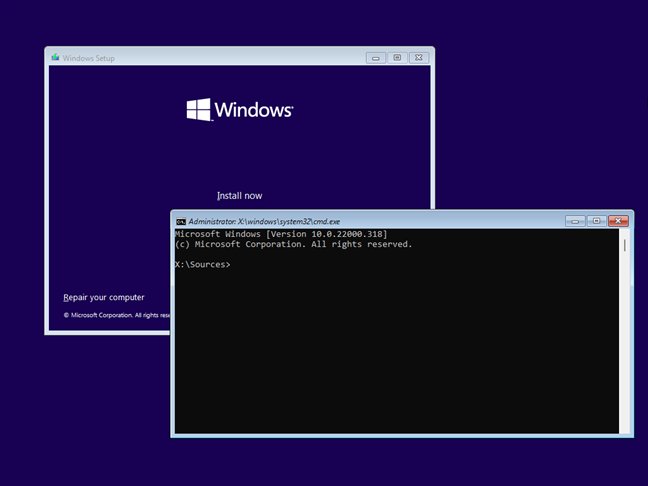
-
Check the drive where Windows 10 is installed. This may not necessarily be the C: drive. For example, type dir C:\windows and then dir D:\windows or dir E:\windows until you find the correct drive letter.
-
Then type regedit, click on branch HKEY_LOCAL_MACHINE, choose the File menu, Load hive then select [SYSTEM DISK]:\windows\system32\config\SOFTWARE.
-
After clicking the Open, Registry Editor will ask you to enter a name for the key you are uploading (for example WIN10). This gives you access to the contents of the HKEY_LOCAL_MACHINE\SOFTWARE of your Windows 10 installation.
-
Click on the HKEY_LOCAL_MACHINE\WIN10.
-
Go to the HKEY_LOCAL_MACHINE\WIN10\Policies\Microsoft\Windows Defender then, in the right panel, right-click, select New, DWORD value (32 bit) assigning it the name DisableAntiSpyware and the value 1. In this way you have temporarily disabled Windows Defender.
-
Go to the key HKEY_LOCAL_MACHINE\WIN10\Microsoft\Windows NT\CurrentVersion\Image File Execution Options. Then right-click on Image File Execution Options and choose New, Key. the new subkey just inserted the name sethc.exe.
-
Select the key HKEY_LOCAL_MACHINE\WIN10\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\sethc.exe, click in the right panel then select New, String value. to the string value just added debugger and c:\windows\system32\cmd.exe.
-
Go to the HKEY_LOCAL_MACHINE\WIN10\Microsoft\Windows Defender\Features and set DWORD value TamperProtection to 0.
-
Close all open windows repeatedly to restart the machine and extract the Windows installation media.
-
When the Windows 10 logon window appears, press the SHIFT key five times, and the command prompt window will appear.
From here,for example, you can create a new administrative account with the commands net user testadmin / add and net localgroup administrators testadmin / add
Then, with the command net user testadmin * you can set a password.
The same command, specifying the name of an account currently present on the machine instead of testadmin , allows you to reset the password of any other account: Windows 10 will ask for the new password to be set.
Note: If you use this method to retrieve the administrator password on a ‘personal’ or ‘production’ system that is to be used later, I recommend rolling back all changes on the registry once the password has been changed.